What happened?
Two men are accused of hacking into computer networks in the United States, Britain, other NATO countries and Ukraine on behalf of the Russian government.
Who are the men?
The U.S. Department of Justice named the two men as officers of Russia’s Federal Security Service (FSB) Center 18, Ruslan Aleksandrovich Peretyatko and Andrei Stannis Andrey Stanislavovich Korinets.
Financial Stability Board? Isn’t this the successor to the KGB?
that’s right. These individuals are said to be members of the Callisto Group (also known as Star Blizzard, SEABORGIUM, TA446, COLDRIVER, TAG-53 and BlueCharlie). The Callisto Group is believed to be controlled by the FSB Information Security Center No. 18.
So, what did these two Russians do?
These individuals, along with other co-conspirators who have not yet been charged, allegedly launched sophisticated spear phishing campaigns to gain access to victims’ computers and email accounts.
Who are their targets?
The FSB, through the Callisto Group, is believed to be behind the hack:
What does a spear phishing campaign look like?
According to Microsoft, a typical attack begins with an email pretending to be from a known contact of the intended victim. Typically, emails are sent from a free Proton (@proton.me or @protonmail.com) account.
The initial email typically does not contain attachments or links, but simply asks the recipient to view the file. When the intended victim responds, they will receive a new message containing a link to a PDF or PDF attachment on the cloud-based platform.
However, the content of the PDF will be blurred, and a button will appear asking the recipient to open the file in a cloud service such as OneDrive.
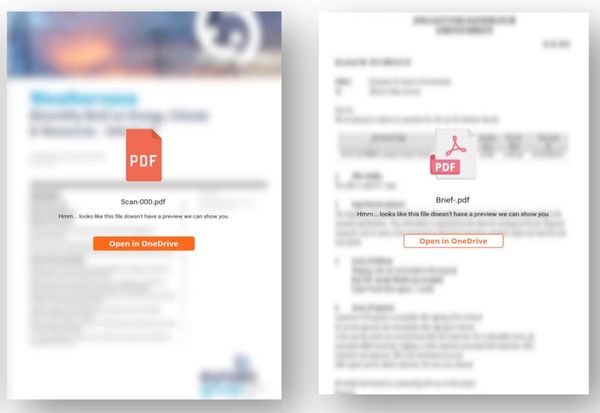
However, clicking the button will take the intended victim to a phishing page that could potentially steal their password and (if multi-factor authentication is enabled) any authentication tokens entered.
I guess hardware authentication keys would be a stronger form of MFA?
that’s right. But most people don’t have any form of multi-factor authentication, let alone a hardware key.
These men have been charged by U.S. authorities, but what are the chances that they will appear in a U.S. court?
They likely won’t, even though the U.S. State Department has announced a reward of up to $10 million for information leading to the identity or location of these men and their co-conspirators.
In addition to the charges, the U.S. and British governments announced sanctions against Peretyatko and Korinec for their roles in the hack.
The British government said that although some of the hacking did lead to the leak of documents, “the attempt to interfere with British politics and democracy was not successful.”
British Foreign Secretary David Cameron said: “Russia’s attempts to interfere in British politics are completely unacceptable and seek to threaten our democratic processes. Despite their repeated efforts, they have failed.” “Today’s sanctions on those responsible are and subpoenaing the Russian ambassador, we uncovered their malign influence attempts and revealed yet another example of how Russia chooses to operate on the global stage. We will continue to work with our allies to expose their influence.” Russian Covert Network activities and hold Russia accountable for its actions. “
