
Threat actors are called UAC-0099 Related to ongoing attacks targeting Ukraine, some of which exploit high-severity flaws in WinRAR software to spread malware called LONEPAGE.
“Threat actors are targeting Ukrainian employees working at companies outside Ukraine,” cybersecurity firm Deep Instinct said in an analysis on Thursday.
UAC-0099 was first documented by the Computer Emergency Response Team of Ukraine (CERT-UA) in June 2023, detailing its espionage-motivated attacks on state organizations and media entities.
From user to administrator: Learn how hackers gain total control
Learn the secret tactics hackers use to become administrators and how to detect and stop it before it’s too late. Register now for our webinar.
Join now
The attack chain leveraged phishing messages containing HTA, RAR, and LNK file attachments, leading to the deployment of LONEPAGE, a Visual Basic Script (VBS) malware capable of contacting a command and control (C2) server to retrieve other Payloads such as keyloggers, stealers, and screenshot malware.
“Between 2022 and 2023, the above-mentioned organization received unauthorized remote access to dozens of computers in Ukraine,” CERT-UA said at the time.
New analysis from Deep Instinct shows that the use of HTA accessories is just one of three different infection chains, with the other two utilizing self-extracting (SFX) archives and booby-trapped ZIP archives. ZIP archives exploit the WinRAR vulnerability (CVE-2023-38831, CVSS score: 7.8) to distribute LONEPAGE.
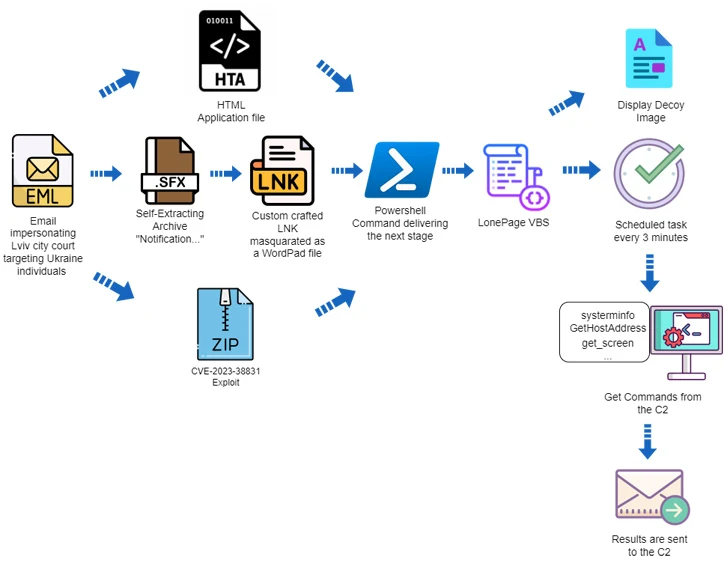
In the former, the SFX file contains a LNK shortcut that disguises itself as a court subpoena DOCX file while using an icon of Microsoft WordPad to trick the victim into opening it, which results in the execution of malicious PowerShell code, thereby releasing the LONEPAGE malware.
Another attack sequence used a specially crafted ZIP archive that was vulnerable to CVE-2023-38831. Deep Instinct discovered UAC-0099 on August 5, 2023, three days after WinRAR maintainers released a patch for the bug. of two such artifacts.

“The strategy used by ‘UAC-0099’ is simple but effective,” the company said. “Although the initial infection vector is different, the core infections are the same – they rely on PowerShell and the creation of scheduled tasks that execute VBS files.”
This development comes as CERT-UA warns of a new wave of phishing messages purporting to be indebted to Kyivstar and designed to deliver a remote access Trojan called Remcos RAT. The agency attributed the activity to UAC-0050.
