
Over the past few years, SaaS has grown to become the backbone of enterprise IT. Service businesses such as medical practices, law firms, and financial services companies are almost entirely SaaS-based. About 70% of software for non-service companies, including manufacturers and retailers, is in the cloud.
These applications contain vast amounts of data, from the least sensitive general company information to the most sensitive intellectual property, customer records and employee data. Threat actors have noticed this shift and are actively working to compromise applications to access data.
Here are the key trends shaping the SaaS security landscape in 2024 and what you can do about it.
The democratization of SaaS
SaaS applications change the way organizations purchase and use software. Business units purchase and use the SaaS tools that best suit their needs. While this helps business units that have long suffered from delays in procuring and installing software, it does require organizations to rethink how they protect their data.
Security teams are forced to develop new ways to protect company data. Due to the lack of access and visibility into the application, their role is to provide advice to business units using SaaS applications. To further complicate matters, each SaaS application has a different setup and uses different terminology to describe security features. Because of the differences between applications, security teams cannot create one-size-fits-all guidance documents.
Security teams must find new ways to work with business units. They need a tool that provides visibility and guidance for each application setting so that they and the business understand the risks and consequences involved in the configuration choices they make.
ITDR forms a critical safety net
If a threat actor gains access to a high-privilege account, they can gain unrestricted access within the application. Organizations now realize that identity is the de facto boundary of their SaaS applications.
When threat actors take over an authorized user account, they typically follow common tactics, techniques, and procedures (TTPs) to obtain the data they want through the application. They leave behind indicators of compromise (IoC), which may be based on actions taken within the application or logs.
As we enter the new year, we will see more organizations adopting an identity threat detection and response (ITDR) approach. ITDR alleviates this concern. As a key component of identity security posture management, ITDR capabilities detect TTPs and IoCs and then send alerts to incident response teams. With ITDR, threat actors who successfully breach identity boundaries can still be stopped before they can steal critical data or insert ransomware into applications.
Learn how ITDR can help you address these today’s SaaS security trends
Cross-border compliance means more tenants can be protected
Multinational companies increasingly face different regulatory requirements in different countries. Therefore, the number of tenants in specific geographies will increase through 2024 as part of the effort to maintain data segmentation based on different regulations.
This change will have a limited impact on software costs because most SaaS application pricing is based on subscribers rather than tenants. However, this will have a significant impact on security. Each tenant requires independent configuration, and just because one instance of an application is secure does not mean that all tenants are secure.
To secure all these tenants, security teams should look for a security solution that allows them to baseline applications, compare tenants, and display security settings side-by-side without charging extra for each additional tenant. By applying best practices throughout the organization, companies can ensure the security of all tenants.
 |
| Figure 1: Adaptive Shield’s platform monitors and presents all Salesforce tenants |
Misconfigured settings lead to new exploits
A preset misconfiguration in ServiceNow caused widespread panic in October. This setting is part of the application access control list and allows unauthorized users to extract data from the records. Configuration errors affected thousands of companies. A similar misconfiguration that occurred in the Salesforce community in May also affected a number of companies and resulted in data leakage.
Such misconfigurations can cause significant damage to a company. They can lead to data breaches, undermine trust between a company and its stakeholders, and have the potential to turn into hefty fines, depending on the nature of the data leaked.
Protecting misconfigurations is an organization’s best chance at preventing these vulnerabilities from impacting its operations and damaging its bottom line.
Learn how to automate SaaS misconfigurations and regain control of your SaaS stack
Increased reliance on third-party applications increases SaaS risk
Third-party applications add real value to the end user. They improve processes, extend functionality, and connect data across multiple applications. Users can connect these SaaS applications with the click of a button and start improving their workflows immediately.
In March 2023, Adaptive Shield released a report showing that organizations using Google Workplace with 10,000-20,000 users had an average of 13,913 third-party applications connected to Google Workplace. Surprisingly, 89% of them requested high-risk or medium-risk permissions. Many of these high-risk applications are used once and then forgotten about, or used by a small number of employees. However, even these dormant or rarely used apps have important permissions and can be used to compromise or corrupt SaaS applications.
As more apps are developed and employees use their own judgment when incorporating third-party apps into their stacks, rather than checking with their security teams, the use of third-party apps will only Increase. Security teams must develop visibility into all their integrated applications and gain a deep understanding of the permissions required, the value the applications contribute to the organization, and the risks they pose.
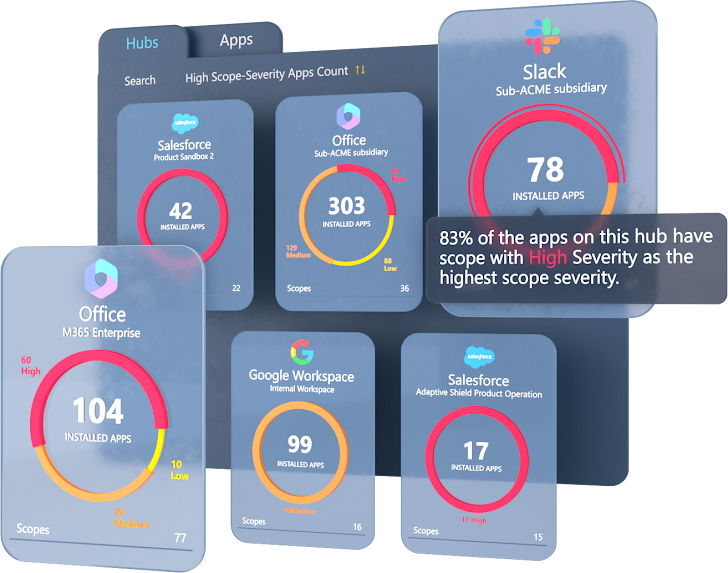 |
| Figure 2: The Adaptive Shield platform shows integrated third-party applications, their risk scores, and scope granted |
Work from home is ubiquitous and multiple devices need to be protected
In 2023, nearly 40% of employees will work from home at least part of the time. According to WFHResearch, about 12% of employees work exclusively from home, while another 28% work hybrid jobs.
These numbers should give pause to security personnel concerned about users logging into their work accounts from personal devices. One of the biggest concerns for security teams is high-privileged users using unmanaged or unsecured devices to log into their accounts. These devices can contain critical vulnerabilities and create new attack vectors. For many teams, it’s nearly impossible to tell which devices are being used to access SaaS applications or to see if those devices are secure.
Organizations are turning to SSPM to protect SaaS
While all of these trends point to legitimate SaaS security issues, SaaS security posture management (SSPM) tools combined with ITDR capabilities such as Adaptive Shield can fully protect the SaaS stack. SSPM is designed to automatically monitor configurations, looking for configuration drifts that impair application state. In SaaS Security Investigation, 2024 Plans and Priorities According to the Cloud Security Association and Adaptive Shield survey, 71% of respondents said their companies have increased investment in SaaS security tools in the past year, and 80% have either sued SSPM or plan to do so in the next 18 Invest in one within the month.
SSPM provides benchmarking tools for multiple tenants of the same application, allowing users to establish best practices, compare settings across instances, and improve the overall health of the SaaS stack.
SSPM also detects and monitors third-party applications, alerts users if its integrated applications require excessive access permissions, and updates the security team if integrated applications are dormant. It tracks users and monitors the devices used to access applications to prevent the use of unmanaged or unsecured devices on enterprise SaaS applications. Additionally, their built-in communication tools make it easy for business units to collaborate with security personnel to protect their applications.
SaaS applications are popular for good reason. They allow organizations to scale as needed, subscribe to the applications they need today, and limit investments in certain IT. Through SSPM, the security of these applications can also be protected.
Watch a ten-minute live demo to learn how to start securing your SaaS stack

1 Comment
I was examining some of your articles on this internet site
and I think this website is rattling informative! Continue putting up.Raise range