
A recent wave of cyberattacks against Albanian organizations involved the use of tools called no justice.
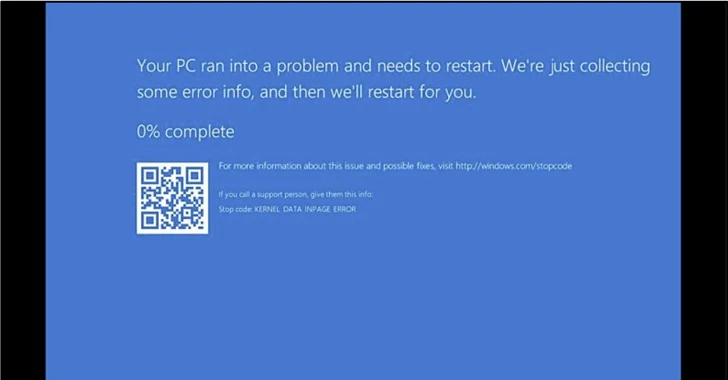
The findings come from cybersecurity firm ClearSky, which said the Windows-based malware “crashes the operating system in a manner that makes it impossible to reboot.”
The intrusions have been attributed to an Iranian “psychological operations group” called Homeland Justice, which has been operating since July 2022 and specializes in planning destructive attacks against Albania.
On December 24, 2023, the adversary resurfaced after a hiatus, claiming that it was “back to eliminate terrorist supporters” and describing its latest campaign as #DestroyDurresMilitaryCamp. The Albanian city of Durrës is currently home to the dissident group Mujahideen of Iran (MEK).
Targets include ONE Albania, Eagle Mobile Albania, Air Albania, and the Albanian Parliament.
The two main tools deployed during the campaign include an executable wiper and a PowerShell script designed to spread the former to other computers on the target network after enabling Windows Remote Management (WinRM).

No-Justice Eraser (NACL.exe) is a 220.34 KB binary file that requires administrator privileges to erase data on your computer.
This is accomplished by removing the boot signature from the Master Boot Record (MBR), which is the first sector of any hard drive and is used to identify the location of the operating system on the disk so that it can be loaded. into the computer’s RAM.
Legitimate tools such as Plink (also known as PuTTY Link), RevSocks, and the Windows 2000 Resource Kit were also provided during the attack to facilitate reconnaissance, lateral movement, and persistent remote access.
This development comes amid ongoing geopolitical tensions in the Middle East, with pro-Iran threat actors such as the Cyber Av3ngers, Cyber Toufan, Haghjoyan and YareGomnam Team increasingly targeting Israel and the United States.
Check Point revealed last month that “groups such as Cyber Av3ngers and Cyber Toufan appear to have adopted a retaliatory narrative in their cyberattacks.”
“By opportunistically targeting U.S. entities using Israeli technology, these hacktivist agents sought to pursue a dual retaliation strategy—claiming to target both Israel and the United States in a single, orchestrated cyberattack.”

Cyber Toufan, in particular, has been linked to numerous hacking breach operations targeting over 100 organizations, which wiped out infected hosts and posted stolen material on their Telegram channels.
“They caused so much damage that many organizations—almost a third, in fact—were unable to recover,” said security researcher Kevin Beaumont. “More than a month later, some of them are still Completely offline, victims removed include private companies and Israeli state government entities.”
Last month, Israel’s National Cyber Authority (INCD) said it was tracking about 15 hacker groups linked to Iran, Hamas and Hezbollah since the war between Israel and Hamas broke out in October 2023 , these organizations conduct malicious activities in Israeli cyberspace.
The agency further noted that the techniques and tactics employed had similarities to those used in the Ukraine-Russia war, using psychological warfare and wipe malware to destroy information.

3 Comments
Pingback: Pro-Iran hacker group targets Albania with unfair Wiper malware – Tech Empire Solutions
Pingback: Pro-Iran hacker group targets Albania with unfair Wiper malware – Paxton Willson
Pingback: Pro-Iran hacker group targets Albania with unfair Wiper malware – Mary Ashley