About nine years ago, KrebsOnSecurity profiled a Pakistan-based cybercriminal group called “manipulator,” a massive web hosting network for phishing and spam delivery platforms. In January 2024, the operators implored the author to unpublish a previous story about their work, claiming that the group had turned over a new leaf and become legitimate. But New research shows that even though these fools have improved the quality of their products and services, they’re still terrible at hiding their illegal activity.
In May 2015, KrebsOnSecurity published a brief article about a team of brazen manipulators, noting that they openly operate hundreds of websites selling tools designed to trick people into giving up their usernames and passwords or deploy malware on their PCs .
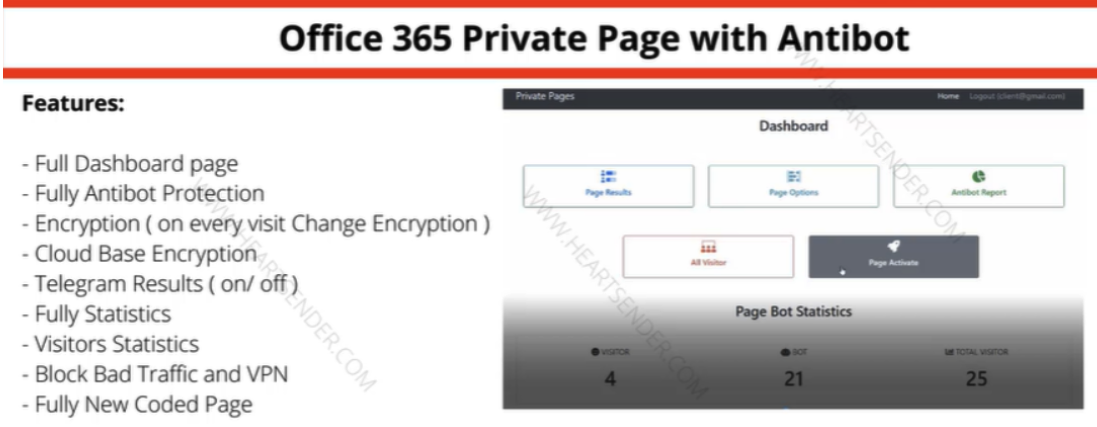
Operator advertisement for the “Office 365 Private Pages with Antibot” phishing kit for sale on the heartsender.com domain. “Anti-bots” refers to attempts to evade automated detection techniques and deploy phishing capabilities for as long as possible. Image: Domain Tools.
The manipulator’s core brand has long been a common cybercriminal identity called “Syed Raza,” who for the past decade has peddled a popular spam and phishing service variously called “Ford Tools,” “Forpage,” “foot transmitter,” “ford companyetc. The term “FUD” in these names stands for “FUli Un-D“Detectable” refers to cybercriminal resources that can evade detection by security tools such as anti-virus software or anti-spam devices.
A report by The Manipulators in September 2021 found that Saim Raza and company were thriving under the FudCo brand, which they secretly managed through a front company called “FudCo.” Our coding solutions.
The article worked backwards from all known Saim Raza email addresses to identify the Facebook profiles of multiple We Code Solutions employees, many of whom gathered around a giant cake with the word “FudCo” painted on it to celebrate Company anniversary.

Since the report was published, KrebsOnSecurity has been contacted by Saim Raza twice. The first was in the weeks after this article was published in September 2021, when a known email address for Saim Raza — bluebtcus@gmail.com —Requesting that this story be taken down.
Saim Raza’s identity wrote: “Hello, we have left those boring things behind years ago.” “Why do you send us emails? Why do you want to ruin our lives? We never Harm anyone. Please delete it.”
Not wanting to be manipulated by phishing gangs, KrebsOnSecurity ignored these requests. But on January 14, 2024, KrebsOnSecurity received a message from the same bluebtcus@gmail.com address without warning.
“Please delete this article,” Sam Raza wrote, linking to a 2021 profile. “Ask my police to book me. I’ve given up everything.”
When asked to elaborate on the police investigation, Syed Raza said he had just been released from prison.
“I was there many days,” the reply explained. “Now I’m back after bail. Now I’m going to start my new job.”
Saim Raza did not reveal exactly what this “new job” means.But a new report from researchers domaintools.com It was discovered that several computers associated with The Manipulators had been subject to large-scale hacking attacks with malicious data and password-stealing malware over an extended period of time.
DomainTools said malware infections on Manipulators PCs exposed “a vast amount of account-related data, as well as an overview of the group’s membership, operations and position within the wider underground economy.”
“Oddly, the majority of identified Manipulators customers appear to have been affected by the same stolen malware,” DomainTools wrote. “All observed customer malware infections began after the Manipulators PC was initially compromised, This raises many questions about the origin of these infections.”
There are indeed many questions.Today, Manipulators’ core product is a spam sending service called Heart senderwhose homepage openly promotes phishing kits targeting users of various online companies, including Microsoft 365, Yahoo, America Online, Intuit, iCloud and My IDto name just a few.
Screenshot of the HeartSender 4 home page showing the IP address bound to fudtoolshop@gmail.com. Image: Domain Tools.
HeartSender customers can interact with the subscription service through the website, but the product appears to be more efficient and user-friendly if HeartSender is downloaded as a Windows executable. It is unknown whether the HeartSender program was compromised in some way and used to infect customers of the service.
However, DomainTools also discovered that the hosted version of the HeartSender service leaked a large amount of user information that may not have been intended for public access. Apparently, the HeartSender web interface has several pages accessible to unauthenticated users, thereby exposing customer credentials and support requests to HeartSender developers.
“Ironically, manipulators may pose more short-term risks to their own customers than to law enforcement,” DomainTools wrote. The fact sheet “User Feedback” (sic) disclosed what appeared to be customer authentication tokens, using Operator identifiers and even customer support requests exposing root-level SMTP credentials, all of which are visible to unauthenticated users in domains controlled by the operator. Due to the risk of abuse, this domain will not be published. “
This isn’t the first time a manipulator has shot himself in the foot. 2019, The manipulator failed to update its core domain — manipulator[.]com — is tied to many of the company’s past and current business operations. The domain was quickly seized by Scylla Intel, a cyber intelligence company that specializes in linking cybercriminals to their real-life identities.
Currently, The Manipulators appear to be focused on building and supporting HeartSender, a company that specializes in spam and email-to-SMS spam services.
“A renewed interest in email-to-SMS spam by operators may be a response to a significant increase in text message activity impersonating the USPS,” DomainTools writes. “Evidence posted on HeartSender’s Telegram channel contains a wealth of content regarding Postal Service impersonation, including Attesting to the delivery of USPS-themed phishing lures and the sale of USPS phishing kits.”
Saim Raza declined to answer questions about DomainTools’ findings when contacted via email.
“First [of] We never study viruses or infected computers, etc.,” Raza replied. “If you want to write falsehoods like that, then go ahead. Secondly, I have left the country. If someone binds anything to an exe file and spreads it on the Internet, it is not my fault.”
When asked why he left Pakistan, Saeem Raza said the local authorities just wanted to suppress them.
“After your article was published, our police [identity],” explained Sym Raza. “FIR” in this case stands for “First Information Report,” which is the first complaint filed in Pakistan’s criminal justice system.
“They only get money from me and nothing else,” Saim Raza continued. “Now some police officers are asking for money again. Brother, there are no good laws in Pakistan, they just need money.”
Saim Raza has a history of being dishonest about the truth, so who knows if the manipulator and/or its leader actually fled Pakistan (it was probably more like an extended vacation abroad). With any luck, these people will soon venture into a more Western-friendly country with “good laws” and be warmly welcomed by the local government.
