A new Go-based malware loader called jinx loader Threat actors are using it to deliver next-stage payloads such as Formbook and its successor XLoader.
The disclosure comes from cybersecurity firms Palo Alto Networks Unit 42 and Symantec, both of which highlighted a multi-step attack sequence that led to the deployment of JinxLoader via a phishing attack.
“The malware pays homage to the League of Legends character Jinx, showing the character on its advertising posters. [command-and-control] Login panel,” Symantec said. “JinxLoader’s primary function is simple – to load malware. “
Unit 42 disclose In late November 2023, the malware service was first advertised on hacker forums[.]Net payment starting April 30, 2023, $60 per month, $120 per year, or $200 lifetime fee.

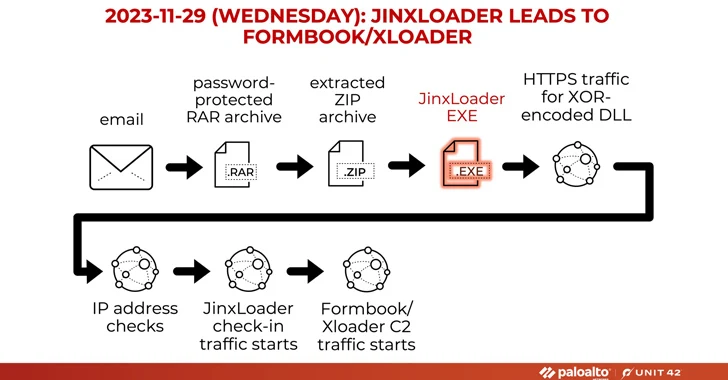
The attacks began with a phishing email impersonating the Abu Dhabi National Oil Company (ADNOC), urging recipients to open a password-protected RAR archive attachment, which upon opening dropped the JinxLoader executable, which then acted as a Formbook Or XLoader’s gateway.
The development comes as ESET revealed a surge in infections, with the company releasing another new family of malware called Rugmi to deliver a variety of information-stealing programs.
At the same time, there was a surge in activity distributing DarkGate and PikaBot, and a threat actor known as TA544 (also known as Narwal Spider) exploited a new variant of the loader malware called IDAT Loader to deploy Remcos RAT or SystemBC malware.
Additionally, the threat actors behind Meduza Stealer have released an updated version of the malware (version 2.2) on the dark web, extending support for browser-based cryptocurrency wallets and improving the credit card (CC) grabber.

Researchers have discovered a new stealer family called Vortex Stealer that is capable of stealing browser data, Discord tokens, Telegram conversations, system information and files smaller than 2 MB, showing that stealer malware is still a cybercrime The lucrative market for molecules is in size.
“The stolen information will be archived and uploaded to Gofile or Anonfiles; the malware will also use a webhook to post it to the author’s Discord,” Symantec said. “It can also be posted to Telegram via Telegram bots. “