
A new Android backdoor has been discovered that has the power to perform a range of malicious actions on an infected device.
dubbing malicious Developed by the McAfee mobile research team, the malware is so named because it was developed using an open source mobile application framework called Xamarin and abuses the operating system’s accessible permissions to achieve its goals.
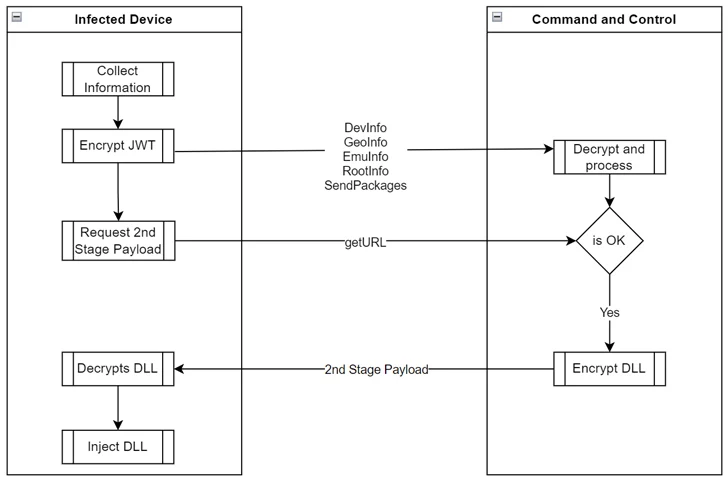
It is also able to collect metadata about the infected device and contact the command and control (C2) server to obtain the second-stage payload, but only after determining whether it meets the requirements.
Security researcher Fernando Ruiz said the second stage “is dynamically injected in the form of an assembly DLL at runtime to fully control the device and potentially perform fraudulent actions such as clicking on ads, installing apps, and other financially motivated actions without the user’s consent. ”. .
The cybersecurity firm said it discovered 25 apps that posed this active threat, some of which had been distributed on the official Google Play store since mid-2020. These apps are estimated to have been installed at least 327,000 times.
From user to administrator: Learn how hackers gain total control
Learn the secret tactics hackers use to become administrators, and how to detect and stop it before it’s too late. Register now for our webinar.
Join now
Most infections occur in Brazil, Argentina, the United Kingdom, Australia, the United States, Mexico and other parts of Europe and the Americas. Some of the apps are listed below –
- Essential Horoscope for Android (com.anomenforyou.essentialhorscope)
- 3D skin editor for PE Minecraft (com.littleray.skineditorforpeminecraft)
- Logo Maker Pro (com.vyblystudio.dotslinkpuzzles)
- Automatic click repeater (com.autoclickrepeater.free)
- Count easy calories calculator (com.lakhinstudio.counteasycaloriecalculator)
- Volume Expander (com.muranogames.easyworkoutsathome)
- LetterLink (com.regaliusgames.llinkgame)
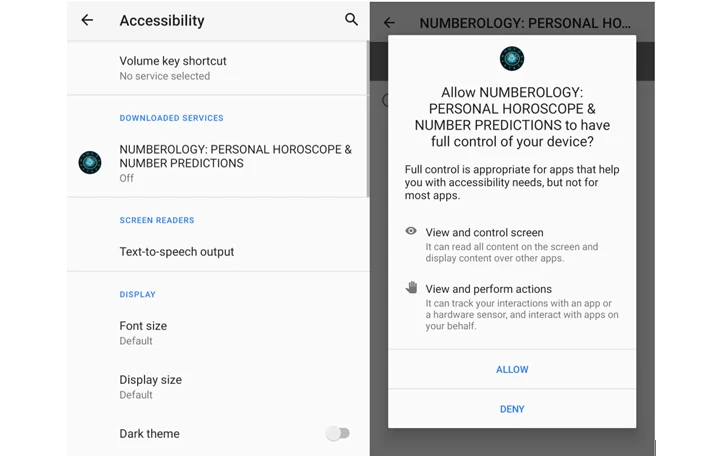
- Numerology: Personal Horoscopes and Numeric Predictions (com.Ushak.NPHOROSCOPENUMBER)
- Step Keeper: Simple pedometer (com.browgames.stepkeepereasymeter)
- Track your sleep (com.shvetsStudio.trackYourSleep)
- Volume Booster (com.devapps.soundvolumebooster)
- Astrology Navigation: Daily Horoscopes and Tarot (com.Osinko.HoroscopyTaro)
- Universal Calculator (com.Potap64.universalcalculator)
Often disguised as health, gaming, horoscopes, and productivity apps, Xamalicious is the latest in a long line of malware families that abuse Android accessibility services, requiring users to access it after installation to perform its tasks.
“To evade analysis and detection, the malware authors encrypted all communications and data transmitted between the C2 and the infected device, not only protected by HTTPS, but also encrypted as JSON using RSA-OAEP and 128CBC-HS256 algorithms Web Encryption (JWE) tokens,” Ruiz noted.
Even more disturbingly, the first-stage implant contains the ability to self-update the main Android package (APK) file, meaning it can be weaponized to act as spyware or a banking Trojan without any user interaction. .
McAfee said it discovered a link between Xamalicious and an ad fraud app called Cash Magnet, which facilitates app downloads and auto-clicker activity to illegally earn revenue by clicking on ads.

“Android apps written in non-Java code using frameworks like Flutter, React Native, and under surveillance and keep them safe. Be on the app market,” Ruiz said.
Android phishing campaign targets India with Banker malware
The disclosure comes as the cybersecurity firm detailed a phishing campaign that used social messaging apps such as WhatsApp to distribute rogue APK files that impersonated legitimate banks such as the State Bank of India (SBI) and Users are prompted to install them to complete mandatory know-your-customer (KYC) procedures.
Once installed, the app asks the user to grant its SMS-related permissions and redirects to a fake page that only captures the victim’s credentials along with their account, credit/debit card, and national identity information.
The data collected and intercepted text messages are forwarded to attacker-controlled servers, allowing the attacker to complete unauthorized transactions.
It is worth noting that Microsoft warned last month that similar campaigns used WhatsApp and Telegram as distribution vehicles to target Indian online banking users.
Researchers Neil Tyagi and Ruiz said: “India has highlighted the serious threat posed by this banking malware in the country’s digital environment, and some attacks have also been detected in other parts of the world, possibly from Indian SBI users living in other countries.”
