An Operation Triangulation spyware attack targeting Apple iOS devices exploited never-before-seen vulnerabilities that could bypass even the critical hardware-based security protections the company had in place.
Russian cybersecurity firm Kaspersky discovered the campaign in early 2023 after being one of its targets, describing it as “the most sophisticated attack chain” observed to date. The campaign is believed to have been active since 2019.
The exploit campaign involved the use of four zero-day vulnerabilities that were chained to gain unprecedented levels of access and backdoor target devices running iOS versions up to iOS 16.2, with the ultimate goal of gathering sensitive information.
From user to administrator: Learn how hackers gain total control
Learn the secret tactics hackers use to become administrators and how to detect and stop it before it’s too late. Register now for our webinar.
Join now
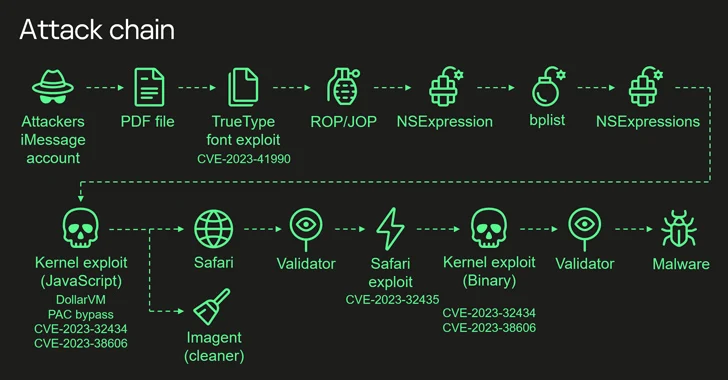
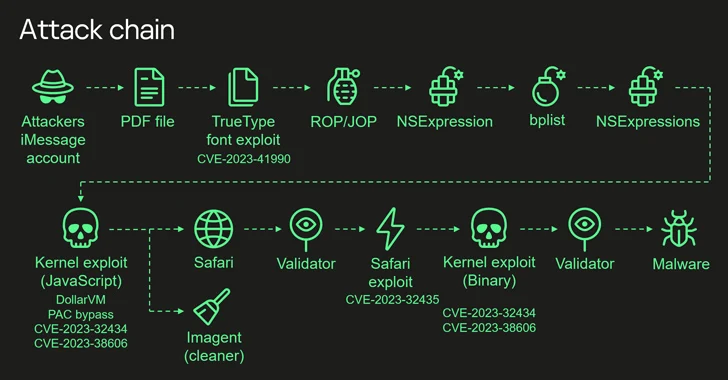
The starting point for a zero-click attack is an iMessage with a malicious attachment, which is automatically processed without any user interaction, ultimately gaining elevated privileges and deploying a spyware module. Specifically, it involves the weaponization of the following vulnerabilities –
- CVE-2023-41990 – A flaw exists in the FontParser component that could lead to arbitrary code execution when handling specially crafted font files sent via iMessage. (Fixed in iOS 15.7.8 and iOS 16.3)
- CVE-2023-32434 – An integer overflow vulnerability exists in the core. Malicious applications can exploit this vulnerability to execute arbitrary code with core privileges. (Fixed in iOS 15.7.7, iOS 15.8 and iOS 16.5.1)
- CVE-2023-32435 – A memory corruption vulnerability exists in WebKit that could lead to arbitrary code execution when processing specially crafted web content. (Fixed in iOS 15.7.7 and iOS 16.5.1)
- CVE-2023-38606 – An issue exists in the core that allows a malicious application to modify sensitive core state. (Fixed in iOS 16.6)
Notably, a patch for CVE-2023-41990 was released by Apple in January 2023, although the company did not disclose details about the exploit until September 8, 2023, the same day it released iOS 16.6.1 to Addresses two additional vulnerabilities related to the Pegasus spyware campaign (CVE-2023-41061 and CVE-2023-41064) that are actively being abused.
This also brings the number of actively exploited zero-day vulnerabilities that Apple has resolved since the beginning of this year to 20.
Of the four vulnerabilities, CVE-2023-38606 deserves special mention because it helps bypass hardware-based exploits targeting sensitive areas of kernel memory by exploiting Memory Mapped I/O (MMIO) registers. security protection, a feature that has never been seen before. Known or documented so far.
This vulnerability specifically targets the Apple A12-A16 Bionic SoC, singling out an unknown MMIO register block belonging to the GPU coprocessor. It is unclear how the mysterious threat actors behind the operation learned of its existence. Also unclear is whether it was developed by Apple or a third-party component like ARM CoreSight.
In other words, CVE-2023-38606 is a critical link in the exploit chain and is closely related to the success of the triangulation operation, as it allowed the threat actor to take full control of the infected system.

Security researcher Boris Larin said: “Our guess is that this unknown hardware feature is most likely used by Apple engineers or factories for debugging or testing purposes, or was included by mistake.” “Because the firmware is not used This feature, so we don’t know how the attacker knew how to use it.”
“Hardware security often relies on ‘security through obscurity’ and reverse engineering is much more difficult than software, but this is a flawed approach because sooner or later, all secrets are revealed. Relying on ‘security through obscurity’ A system that achieves security in obscurity can never be truly secure. “
The development comes as The Washington Post reported that Apple warned in late October that Indian journalists and opposition politicians may have been targeted by state-sponsored spyware attacks, prompting the government to question the veracity of those claims. nature, describing it as an “algorithm glitch.” “Within the systems of the tech giants.
Additionally, senior administration officials asked the company to mitigate the political impact of the warning and urged it to provide alternative explanations for why it issued the warning. So far, India has neither confirmed nor denied the use of spyware such as NSO Group’s Pegasus.
The Washington Post quoted people familiar with the matter as saying that “Indian officials asked Apple to withdraw the warning, saying it had made a mistake” and that “Apple India’s corporate communications executives began privately asking Indian technology journalists to highlight Apple in their reports. “The warning may be a false alarm” in an effort to divert attention from the government.