
A new analysis shows that malicious code inserted into the open source library XZ Utils, a widely used software package in major Linux distributions, can also facilitate remote code execution.
Last week, this bold supply chain compromise was tracked as CVE-2024-3094 (CVSS score: 10.0), when Microsoft engineer and PostgreSQL developer Andres Freund warned of a backdoor in the data compression utility, a remote attack The attacker provides a method to bypass secure shell authentication and gain full access to the affected system.
XZ Utils is a command-line tool for compressing and decompressing data in Linux and other Unix operating systems.
The malicious code was allegedly introduced intentionally by a project maintainer named Jia Tan (also known as Jia Cheong Tan or JiaT75) in what appears to be a sophisticated attack spanning several years. GitHub user accounts were created in 2021. The identities of the participants are currently unknown.

“Threat actors began contributing to the XZ project approximately two years ago, slowly building credibility until they were given maintainer responsibilities,” Akamai said in a report.
In a more clever act of social engineering, sock accounts like Jigar Kumar and Dennis Ens were believe Used to send feature requests and report various issues in the software to force the original maintainer (Lasse Collin of the Tukaani project) to add new co-maintainers to the repository.
Jia Tan made a series of changes to XZ Utils in 2023, eventually releasing version 5.6.0 in February 2024. They also hide a sophisticated backdoor.
“As I hinted in previous emails, Jatan may play a larger role in the plan in the future,” Colin said in a June 2022 exchange with Kumar.
“He helps a lot outside the list and is actually a co-maintainer already. 🙂 I know not much is happening in the git repository yet, but things will happen step by step. Anyway, maintenance has been done Something has changed. At least for XZ Utils, it’s a work in progress.”
This backdoor affects the XZ Utils 5.6.0 and 5.6.1 tarballs, which contain modified versions of the same implant. Collins has since acknowledged the breach in the project, saying that both tarballs were created and signed by Jia Tan and that they could only access the now-defunct GitHub repository.
“This is clearly a very sophisticated state-sponsored operation and the complexity and years of planning are impressive,” firmware security firm Binarly said. “Such a complex and expertly designed comprehensive implant framework is not intended for a one-time surgery. developing.”
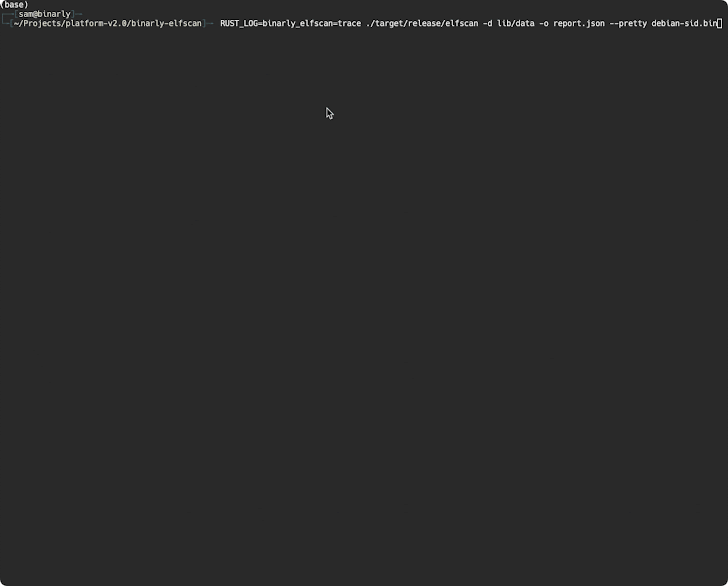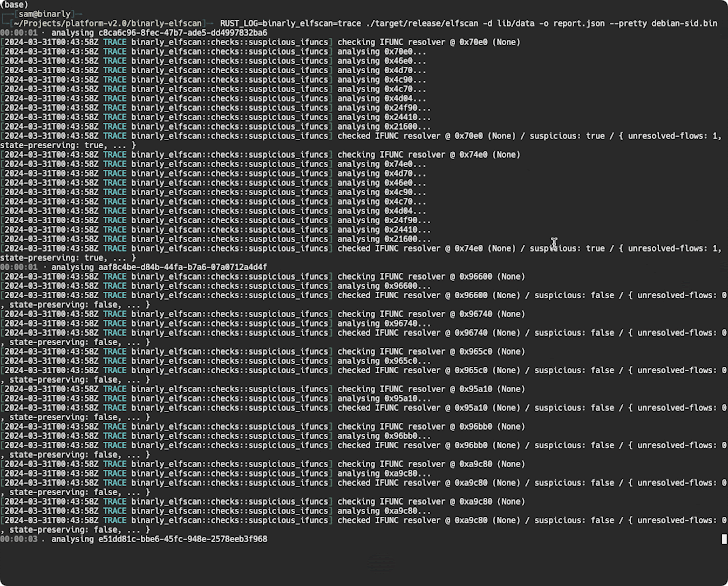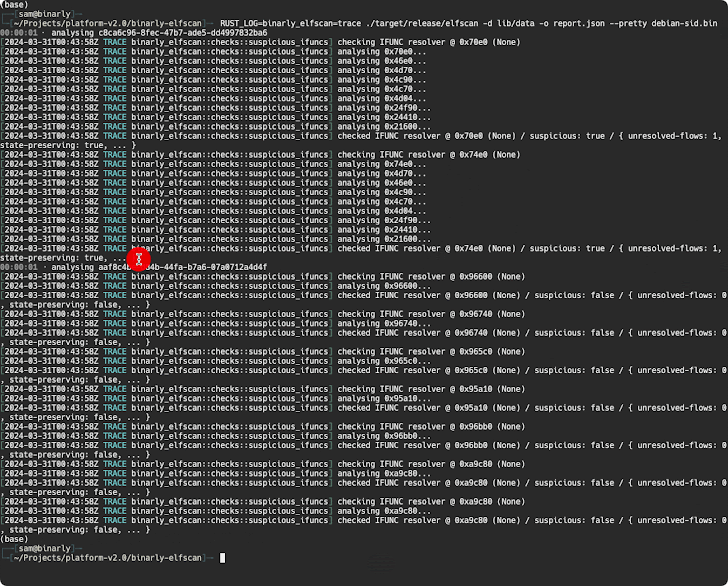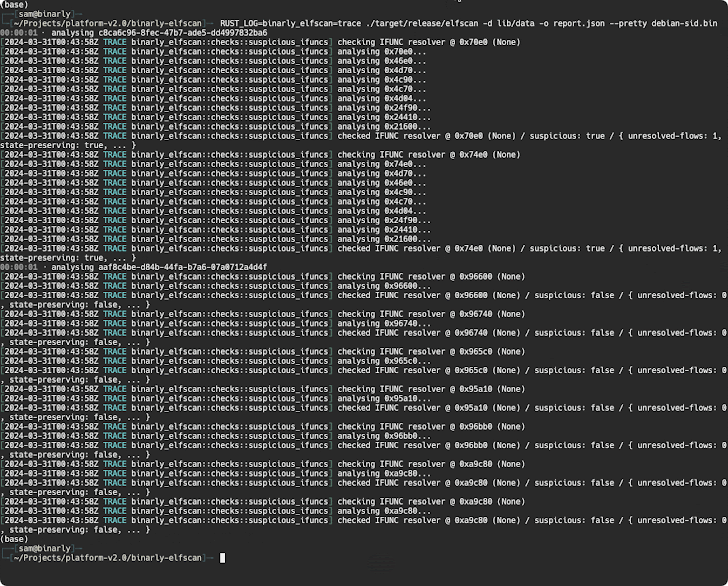
Open source cryptographer Filippo Valsorda conducted a deeper examination of the backdoor and also discovered that the affected version allows specific remote attackers to send arbitrary payloads via SSH credentials, which will be executed in a way that bypasses the authentication protocol. thereby effectively seizing control of the victim’s machine.
“A backdoor appears to have been added to the SSH daemon on vulnerable computers, allowing a remote attacker to execute arbitrary code,” Akamai said. “This means that any vulnerable package with an exploit that exposes SSH to the internet machines may be vulnerable.”

Needless to say, Freund’s accidental discovery is one of the most serious supply chain attacks discovered to date, and could have caused a serious security disaster if the package had been integrated into stable versions of Linux distributions.
“The most striking part of this supply chain attack was the extreme dedication of the attackers, who took more than two years to establish themselves as legitimate maintainers, offering to take over work on various OSS projects. And commit code in multiple projects to commit code in order. To avoid detection,” JFrog said.
As with the case of Apache Log4j, this incident once again highlights the reliance on open source software and volunteer-run projects, and the possible consequences if they are compromised or contain major vulnerabilities.
“The bigger ‘fix’ is for organizations to adopt tools and processes that enable them to identify signs of tampering and malicious functionality in the open source and commercial code used in their own development processes,” ReversingLabs said.

4 Comments
Pingback: Malicious code in XZ Utils on Linux can achieve remote code execution – Tech Empire Solutions
Pingback: Malicious code in XZ Utils on Linux can achieve remote code execution – Paxton Willson
Pingback: Malicious code in XZ Utils on Linux can achieve remote code execution – Mary Ashley
Your point of view caught my eye and was very interesting. Thanks. I have a question for you.