Cloud solutions are more mainstream than ever, and therefore more exposed.
In 2023 alone, a whopping 82% of data breaches will occur in public cloud, private cloud or hybrid cloud environments. Additionally, nearly 40% of breaches spanned multiple cloud environments. The average cost of a cloud breach is higher than the overall average, at $4.75 million. In an era where the cloud has become the de facto standard, with 65% of IT decision-makers confirming that cloud-based services are their first choice when upgrading or purchasing a new solution, cloud security still faces multiple challenges despite its overwhelming advantages.
Security challenges in the cloud
One major obstacle is lack of visibility. Unlike physical servers that you can see and touch, cloud resources are often spread across vast networks, making it difficult to monitor suspicious activity and allowing vulnerabilities to go undetected. Another challenge is the inconsistency between cloud provider permissions management systems. Different providers have different controls over who can access and modify data. This inconsistency creates complexity and increases the risk of accidental misconfiguration, a leading cause of breaches.
Additionally, with multiple teams involved in cloud deployments (development, operations, security), clear ownership and responsibility for cloud security can become blurred. A lack of coordination can lead to situations where security best practices are ignored or bypassed. Additionally, many attacks migrate across the cloud to on-premises environments and vice versa, potentially putting both environments at risk.
All of these challenges highlight the urgent need for robust cloud security solutions that provide comprehensive visibility, standardized permissions management, and clear lines of responsibility. However, even among the best-equipped teams, security resources can be stretched thin, and cloud security teams need to investigate and remediate thousands of vulnerabilities that may not have the same impact on critical resources. This leads to uncertainty about what to fix first and how to actually address all identified risks, leaving cloud environments open to cyberattacks.
Ongoing exposure management is critical
Security teams need to prioritize the most critical vulnerabilities rather than chasing countless vulnerabilities. This means being able to quickly identify the most dangerous attack paths and take preemptive action against advanced attack methods in the cloud.
By focusing on high-risk areas, cloud security teams can develop targeted remediation plans to prevent critical attacks, streamline workflows, and accurately report real threats across multiple cloud environments. Key to achieving this is Continuous Threat Exposure Management (CTEM), a proactive, continuous five-phase plan or framework that reduces the risk of cyberattacks. First launched by Gartner in 2022, CTEM has proven to be critical for preventing high-impact attacks, improving remediation efficiency, and reporting true risks.
Stop letting hackers securely connect to your cloud. Discover the secret maps they don’t want you to have in our e-book:’The power of attack paths in the cloud‘Learn to visualize, block and protect your digital fortress like never before.
CTEM was introduced to address the endless list of exposures, and more specifically vulnerabilities, in on-premises environments. Without the ability to highlight and fix the most critical vulnerabilities, security teams are left to fix CVEs that may or may not be exploitable or impactful in their specific environment. In a multi-cloud environment, the list of vulnerabilities may be shorter, but coupled with misconfigurations and high-privileged access, they add up to a long list of vulnerabilities that attackers can exploit to compromise multi-cloud environments and that security teams must address. The only way to stop attacks is to identify and remediate the risks that have the greatest impact on your business. This requires the adoption of the CTEM framework in the cloud environment.
Fix important issues in multi-cloud
To help cloud security teams address critical issues and stop high-impact attacks in multi-cloud environments, a comprehensive CTEM program will highlight the most impactful entities that can compromise cloud resources. These solutions identify potentially compromised cloud resources and discover any vulnerabilities that attackers could use to compromise those resources. Mapping attack paths that attackers may exploit helps prioritize and validate the most impactful vulnerabilities exploitable in multi-cloud environments so they can be addressed first.
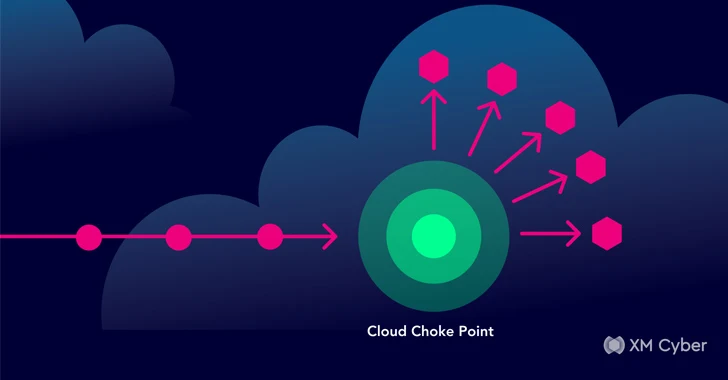
For example, the biggest bottlenecks can be identified from an attacker’s perspective. Choke points are critical weaknesses in cloud defenses, where multiple attack paths converge on a single exposure. They can be easily compromised by an attacker, who can then gain access to a vast network of resources – databases, computers, identity controls, and more. By prioritizing these high-impact areas, security teams maximize the return on their security efforts by focusing on the targets that are most attractive to attackers. Common bottlenecks include Internet-facing systems and unused access accounts. Addressing these issues can significantly reduce the attack surface, effectively hardening the entire cloud environment.
 |
| Cloud choke point example showing inbound and outbound attack paths |
Another example of high-impact exposure results from predefined high-privilege access. Highly privileged accounts (such as predefined administrators) are considered “game over” assets. If compromised, attackers could wreak havoc. Taking a comprehensive CTEM approach can help identify these accounts and uncover weaknesses that could make them vulnerable to attack. This includes discovering administrator access without multi-factor authentication (MFA) or unused service accounts – essentially weaknesses that attackers love to exploit.
To ensure critical exposures are addressed, advanced exposure management solutions provide remediation guidance and alternatives. Typically, highly privileged accounts or internet-facing resources cannot be restricted, but analyzing the attack paths leading to them can identify fixes that reduce their exploitability and therefore their level of risk.
Stop mixed environment attacks
Attackers are not limited by hybrid environments, and defenders must ensure they are not either. Solutions that analyze hybrid attack paths across on-premises and multi-cloud environments enable security teams to stay one step ahead of attacks and understand exactly where they face cyber threats. These tools provide complete details on potential vulnerability points, attack techniques, privilege usage and remediation options to help customers address these vulnerabilities and block the most critical attack paths.
 |
| Example of hybrid attack paths across MS Active Directory and AWS |
generalize
While traditional cloud security struggles to cope with the ongoing volume of exposure, CTEM provides actionable remediation plans by focusing on the most critical issues in a given environment. The right CTEM approach spans on-premises and multi-cloud, covering your entire IT environment. This holistic approach eliminates blind spots and enables organizations to move from reactive to proactive defense. By adopting CTEM, organizations can ensure success in a cloud-based future.
notes: This professional article was written by Zur Ulianitzky, Vice President of Security Research at XM Cyber.