
Ransomware groups are increasingly turning to remote encryption in their attacks, marking an escalation in the tactics used by financially motivated actors to ensure the success of their campaigns.
“Companies can have thousands of computers connected to their network, and with remote ransomware, it only takes one unprotected device to compromise the entire network,” said Mark Loman, vice president of threat research at Sophos.
“Attackers know this, so they will look for a ‘weak point’ – and most companies have at least one. Remote encryption will be a long-term problem for defenders.”
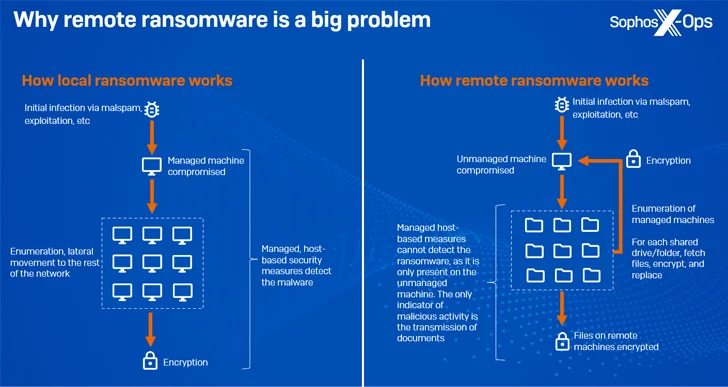
As the name suggests, remote encryption (also known as remote ransomware) occurs when a compromised endpoint is used to encrypt data on other devices on the same network.
From user to administrator: Learn how hackers gain total control
Learn the secret tactics hackers use to become administrators and how to detect and stop it before it’s too late. Register now for our webinar.
Join now
In October 2023, Microsoft revealed that approximately 60% of ransomware attacks now involve malicious remote encryption to minimize their footprint, with more than 80% of ransomware attacks originating from unmanaged devices.
“Known ransomware families that support remote encryption include Akira, ALPHV/BlackCat, BlackMatter, LockBit and Royal, and this technology has been around for some time – CryptoLocker targeted network shares as early as 2013,” Sophos said.
A significant advantage of this approach is that it renders process-based remediation ineffective and the malicious activity cannot be detected by managed computers because it only exists on unmanaged devices.
The development comes amid broader changes in the ransomware landscape, with threat actors adopting atypical programming languages, targeting systems beyond Windows, auctioning off stolen data, and launching attacks after business hours and on weekends to thwart detection. and incident response efforts.
In a report released last week, Sophos highlighted the “symbiotic but often uneasy relationship” between ransomware gangs and the media, not only to attract attention but also to control the narrative and report what they deem to be inaccurate Question. .
This also extends to publishing FAQs and press releases on its data breach website, even including direct quotes from operators, and correcting mistakes made by journalists. Another tactic is to use catchy names and beautiful graphics that show the evolution of cybercriminal specialization.

“For example, the RansomHouse group published a message on its leak site specifically targeted at journalists, which offered to share the information on a ‘PR Telegram channel’ before official release,” Sophos noted.
While ransomware groups like Conti and Pysa are known for employing organizational hierarchies consisting of senior executives, system administrators, developers, recruiters, HR, and legal teams, there is evidence that some ransomware groups Advertising opportunities for English writers and speakers on crime forums.
“Media engagement provides ransomware gangs with a tactical and strategic advantage; it allows them to pressure their victims, while also allowing them to shape narratives, exaggerate their notoriety and ego, and further ‘mythologize’ themselves,” the company said. “.
