
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has added a critical security vulnerability affecting Microsoft SharePoint Server to its Known Exploited Vulnerabilities (KEV) catalog, citing evidence of active exploitation.
The issue is tracked as CVE-2023-29357 (CVSS score: 9.8) is a privilege escalation flaw that allows an attacker to gain administrator privileges. Microsoft released a patch for the bug as part of the June 2023 Patch Tuesday update.
“An attacker who obtains spoofed JWT authentication tokens can use them to perform network attacks, bypassing authentication and allowing them to gain the rights of the authenticated user,” Redmond said. “The attacker does not need to No privileges and no action is required from the user.”
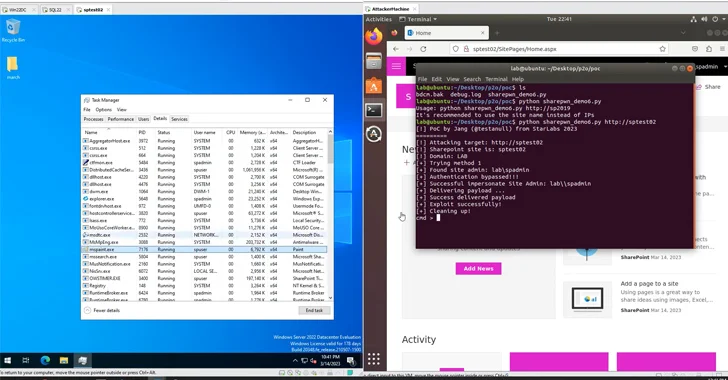
Nguyễn Tiến Giang (Jang), a security researcher at StarLabs SG, demonstrated an exploit for the vulnerability at the Pwn2Own Vancouver hacking competition and received a $100,000 prize.

The pre-authenticated remote code execution chain combines an authentication bypass (CVE-2023-29357) with a code injection bug (CVE-2023-24955, CVSS score: 7.2), which was reported by Microsoft in May 2023 repair.
“The process of discovering and building the exploit chain took nearly a year of careful work and research to complete the complete exploit chain,” Tiến Giang noted in a technical report released in September 2023.
It is currently unclear the actual exploits of CVE-2023-29357 and the identity of the threat actors who may be abusing them. That said, federal agencies are recommended to apply patches by January 31, 2024, to protect against active threats.
3 Comments
Pingback: CISA flags active exploit of Microsoft SharePoint vulnerability – Tech Empire Solutions
Pingback: CISA flags active exploit of Microsoft SharePoint vulnerability – Mary Ashley
Pingback: CISA flags active exploit of Microsoft SharePoint vulnerability – Paxton Willson