this Federal Bureau of Investigations The FBI revealed today that it had infiltrated the world’s second-largest ransomware gang, a Russia-based criminal gang known as ALPHV and black cat. The FBI said it seized the gang’s dark web site and released a decryption tool that hundreds of victim companies can use to recover their systems. Meanwhile, BlackCat responded by briefly “unblocking” its darknet site and promising to provide 90% commissions to affiliates who continued to work with criminal groups and open up all operations from hospitals to nuclear power plants.
A slightly modified version of the FBI seizure notice on the BlackCat dark web site (with a Santa hat added).
There were rumors of possible law enforcement action against the ransomware group BlackCat after its darknet website went offline and became inaccessible for about five days in the first week of December. BlackCat eventually managed to get the site back online, blaming the outage on Equipment failure.
But earlier today, the BlackCat website was replaced with an FBI seizure notice, and federal prosecutors in Florida issued a search warrant explaining how FBI agents were able to gain entry and disrupt the organization’s operations.
Statement about the action U.S. Department of Justice The FBI developed a decryption tool that enabled the agency’s field offices and global partners to provide more than 500 affected victims with the ability to restore their systems.
“With decryption tools provided by the FBI to hundreds of ransomware victims around the world, businesses and schools can reopen and health care and emergency services can get back online.” Deputy Attorney General Lisa O. Monaco explain. “We will continue to prioritize disruption and put victims at the center of our strategy to dismantle the ecosystem that fuels cybercrime.”
The U.S. Department of Justice reports that since BlackCat was founded about 18 months ago, the criminal organization has targeted the computer networks of more than 1,000 victim organizations. BlackCat attacks typically involve data encryption and theft; if the victim refuses to pay the ransom, the attacker typically publishes the stolen data on a Darknet site linked to BlackCat.
BlackCat was formed by recruiting operators from multiple competing or disbanded ransomware groups, including REvil, BlackMatter, and DarkSide. The latter group was responsible for the Colonial Pipeline attack in May 2021, which caused fuel shortages and price spikes across the country.
Like many other ransomware operations, BlackCat operates in a “ransomware-as-a-service” model, with a development team maintaining and updating the ransomware code and all its supporting infrastructure. Affiliates are incentivized to attack high-value targets as they typically receive 60-80% of any payout, with the remainder going to the crooks running the ransomware operation.
BlackCat was able to briefly regain control of its dark web servers today. Shortly after the FBI’s seizure notice was posted, the homepage was “unblocked” and the incident was recast from the perspective of the ransomware group.
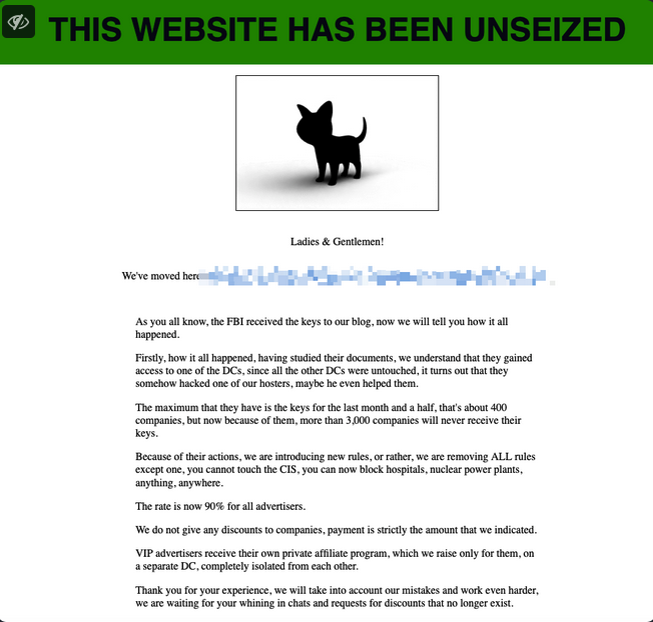
The message briefly appeared on the BlackCat ransomware group’s homepage this morning. Image: @GossiTheDog.
BlackCat claims that the FBI’s actions only affected part of its operations and that an additional 3,000 victims will no longer be able to opt-in to receive decryption keys as a result of the FBI’s actions. The group also said it would formally lift any restrictions or discouragements on hospitals or other critical infrastructure.
“Because of their behavior we are introducing new rules, or rather we are removing all the rules except one, you cannot touch CIS [a common restriction against attacking organizations in Russia or the Commonwealth of Independent States]. Now you can blockade hospitals, nuclear power plants, anything anywhere. “
The criminal organization also said it set affiliate commissions at 90%, presumably to attract interest from potential affiliates who might otherwise be spooked by recent FBI infiltrations. BlackCat also promised that all “advertisers” under this new program will manage their affiliate accounts through completely isolated data centers.
BlackCat’s darknet site currently displays FBI seizure notices.but as Computer beeps founder Lawrence Abrams Mastodon explains that both the FBI and BlackCat possess private keys associated with the Tor hidden service URL of BlackCat’s victim-shaming and exfiltration website.
“Whoever publishes the latest hidden service on Tor, in this case the BlackCat data breach site, will regain control of the URL,” Abrams said. “Expect to see this type of back and forth over the next few days.”
The U.S. Department of Justice said anyone with information about BlackCat affiliates or their activities may be eligible to receive up to $10 million through the State Department’s Rewards for Justice program, which accepts reports submitted through a Tor-based tip hotline. Information (this website can only be accessed using the Tor browser).
Further reading: CISA StopRansomware Alert on the tools, techniques, and procedures used by ALPHV/BlackCat.