
As technology adoption shifts to employee-led, just-in-time, and from any location or device, IT and security teams find themselves dealing with an ever-expanding SaaS attack surface, much of which is often unknown or unmanaged. This significantly increases the risk of identity-based threats, with 80% of today’s breaches using compromised identities, including cloud and SaaS credentials, according to a recent CrowdStrike report.
Given this reality, IT security leaders need practical and effective SaaS security solutions designed to discover and manage their ever-expanding SaaS footprint. Here are 5 main ways Nudge Security can help.
Close the visibility gap
Understanding the full scope of SaaS applications in use is the foundation of a modern IT governance program. If you don’t understand your entire SaaS footprint, you can’t say with confidence where your corporate IP is stored (has anyone synced their desktop to Dropbox?), and you can’t make assumptions about your customer profiles (has anyone synced your customer list uploaded to the new marketing platform) application? ), and you certainly can’t make strong assertions about your production data (has anyone copied their environment into a new AWS account to recreate the support issue?).
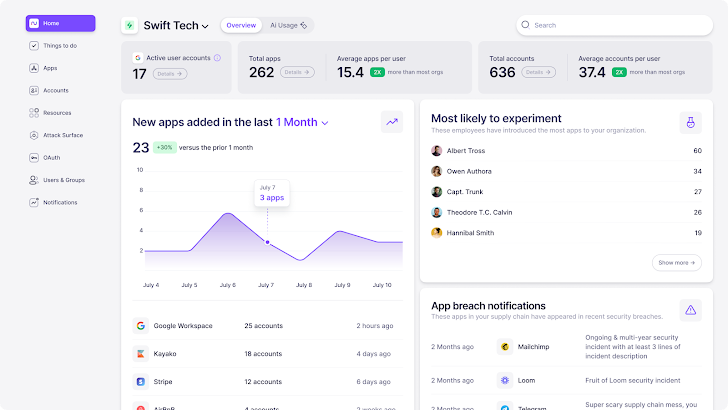
However, given the speed of SaaS adoption, collecting and maintaining an accurate SaaS inventory is a never-ending and daunting task. Nudge Security solves this problem with real-time, continuous SaaS discovery that requires no proxies, browser plug-ins, web proxies or complex API configuration. Within minutes of starting your free trial, you’ll have a complete inventory of all SaaS accounts created by anyone in your organization, along with security context for each application, alerts when new applications are introduced, and the ability to automate SaaS governance tasks.
Managing OAuth Risks
Now, any employee can easily connect multiple SaaS applications and data together using no-code/low-code integration that leverages authorization methods such as OAuth authorization. This creates a complex mesh of SaaS applications that makes it extremely difficult to answer the basic question, “Who (and which SaaS applications) can access my company’s assets?” Attackers are exploiting this sophistication to move laterally in the SaaS supply chain to obtain the crown jewels.
With this in mind, it’s important for IT and security teams to regularly review the introduction of OAuth authorization to their organizations to identify and address overly permissive scopes and application-to-application connections that may violate data privacy and compliance requirements.
This article outlines the key steps to analyze OAuth authorization and assess potential risks, and outlines how Nudge Security provides the context needed to simplify this process.

Monitor your SaaS attack surface
Recent high-profile SaaS supply chain breaches at Circle CI, Okta, and Slack reflect the growing trend of attackers targeting enterprise SaaS tools to penetrate customer environments. As mentioned above, the complexity and interconnectedness of modern SaaS attack surfaces allows attackers to penetrate the software supply chain in search of valuable assets.
Given this reality, it is important to understand which company assets are visible to external attackers and therefore potentially targeted. Arguably, the SaaS attack surface extends to every SaaS, IaaS, and PaaS application, account, user credential, OAuth authorization, API, and SaaS provider (managed or unmanaged) used in an organization. Monitoring this attack surface can feel like a Sisyphus task, as any user with a credit card, or even just a business email address, can expand an organization’s attack surface with just a few clicks.
Nudge Security includes a SaaS attack surface dashboard that shows you all external-facing assets that an attacker can see, including SaaS applications, cloud infrastructure, development tools, social media accounts, registered domains, and more. With this visibility, you can take proactive steps to minimize and protect your SaaS attack surface.

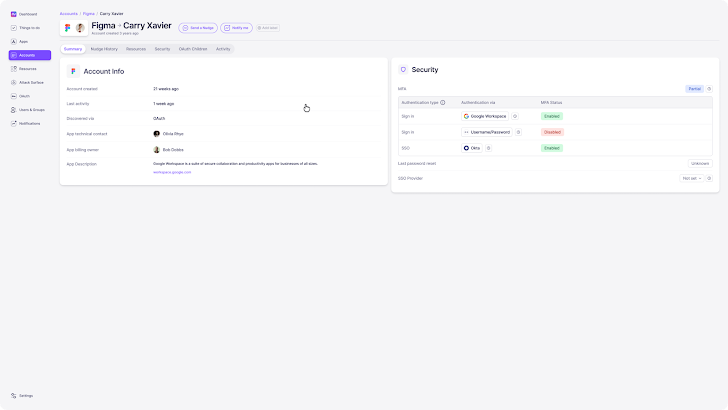
Expand SSO coverage
Single sign-on (SSO) provides a centralized location to manage employee access to enterprise SaaS applications, making it an integral part of any modern SaaS identity and access management plan. Most organizations strive to ensure that all business-critical applications (i.e. applications that handle customer data, financial data, source code, etc.) are registered with SSO. However, when new SaaS applications are introduced outside of IT governance processes, it can be difficult to truly assess SSO coverage.
Nudge Security shows you which applications are registered (and which are not) along with the context of each application so you can prioritize your SSO onboarding efforts appropriately. When you’re ready to add a new application to your SSO tool, Nudge Security starts the SSO onboarding workflow to make the process easier.

Expanding your use of MFA
Multi-factor authentication adds an extra layer of security to protect user accounts from unauthorized access. By requiring multiple factors for verification, such as passwords and unique codes sent to the mobile device, it significantly reduces the chance of hackers accessing sensitive information. This is especially important in today’s digital environment where identity-based attacks are increasingly common.
With Nudge Security, you can see which user accounts have MFA enabled (and not), and send users “prompts” via email or Slack to enable MFA for their accounts. Since long-tail applications are often deployed without IT oversight, this visibility helps IT teams ensure that SaaS security best practices are followed.
Start Improving SaaS Security Today
Nudge Security gives IT and security teams complete visibility into every SaaS and cloud asset created in their organization (managed or unmanaged), with instant alerts when new accounts are created. With this visibility, they can eliminate shadow IT, protect malicious accounts, minimize SaaS attack surfaces and automate tedious tasks, all without hampering the pace of work.
Start your 14-day free trial here.

3 Comments
Pingback: 5 Ways to Reduce SaaS Security Risks – Tech Empire Solutions
Pingback: 5 Ways to Reduce SaaS Security Risks – Mary Ashley
Pingback: 5 Ways to Reduce SaaS Security Risks – Paxton Willson