this U.S. Cybersecurity and Infrastructure Security Agency (CISA) said today it is investigating breaches at a business intelligence firm sixth sense, whose product is designed to allow companies to view the status of multiple third-party online services in a single dashboard. CISA is urging all Sisense customers to reset any credentials and secrets they may have shared with the company, which is the same advice Sisense provided to its customers Wednesday night.
Headquartered in New York City, Sisense has more than 1,000 customers in a range of vertical industries including financial services, telecommunications, healthcare and higher education. April 10, Sisense Information Security Chief Sangram Dash Telling customers that the company is aware of reports that “certain Sisense Company information may have been made available on restricted-access servers known to us (not typically available on the Internet).”
“We are taking this matter seriously and are investigating immediately,” Dash continued. “We have engaged industry-leading experts to assist with our investigation. This incident has not resulted in a disruption to our business operations. Out of an abundance of caution, while we continue our investigation, we urge you to immediately rotate the devices you use in your Sisense applications Any credentials.”
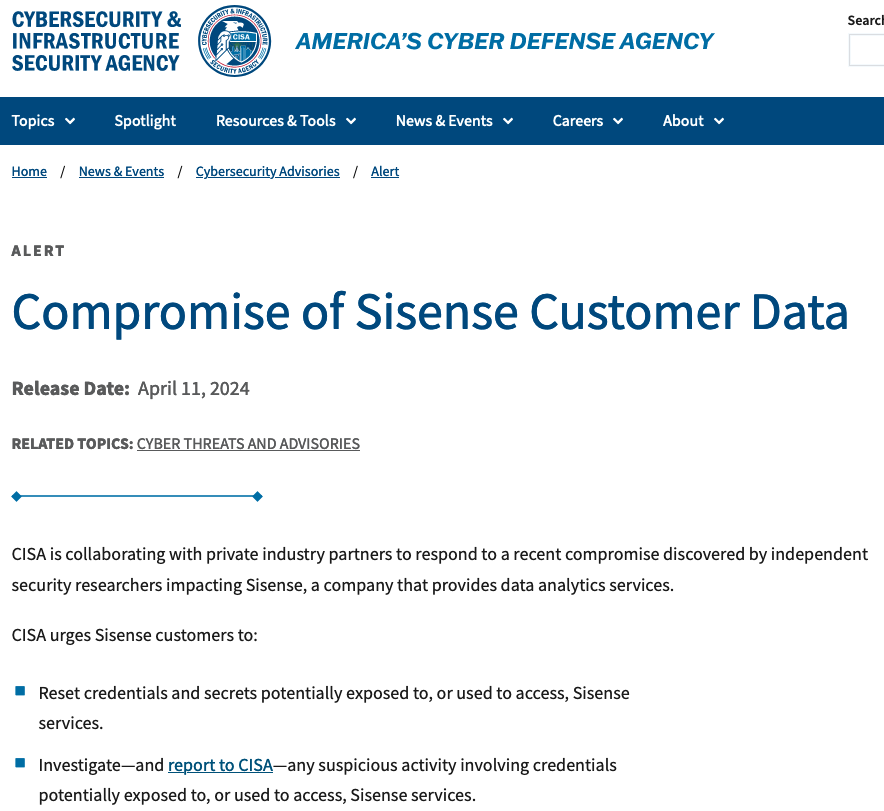
CISA said in the alert that it is working with private sector partners to respond to attacks involving Sisense recently discovered by independent security researchers.
“CISA is actively working with private industry partners to respond to this incident, particularly as it involves impacted critical infrastructure sector organizations,” the sparse alert reads. “We will provide updates as more information becomes available .”
Sisense declined to comment when asked about the veracity of information shared by two trusted sources familiar with the breach investigation. The breach appears to have begun when an attacker somehow gained access to the company’s code repository in GitLab, and the tokens or credentials in that repository allowed the bad guys to access Sisense’s database, these sources said. Amazon S3 bucket in the cloud.
Both sources said the attackers used S3 access to copy and steal terabytes worth of Sisent customer data, which apparently included millions of access tokens, email account passwords, and even SSL credentials.
The incident raises questions about whether Sisense is doing enough to protect the sensitive data entrusted to it by its customers, such as whether a large amount of stolen customer data was encrypted while at rest in these Amazon cloud servers.
However, it has become apparent that unknown attackers now have all of the credentials used by Sisense customers in their dashboards.
The leak also makes it clear that Sisense is somewhat limited in the cleanup actions it can take on behalf of its customers, as access tokens are essentially text files on your computer that allow you to stay logged in for a long time – sometimes indefinitely. Depending on the service we’re discussing, an attacker may be able to reuse these access tokens to authenticate as the victim without providing valid credentials.
Beyond that, it’s largely up to Sisense customers to decide if and when to change their passwords for the various third-party services they previously entrusted to Sisense.
Earlier today, a PR firm that works with Sisense contacted KrebsOnSecurity to ask if KrebsOnSecurity planned to release any further updates about its breach (KrebsOnSecurity posted a screenshot of the CISO’s client email to LinkedIn and Mastodon on Wednesday night). PR representatives said Sisense wanted to ensure they had an opportunity to comment before the story was published.
But when faced with the details my source shared, Sisense apparently changed her mind.
“After consulting with Sisense, they told me they did not want to respond,” a PR representative said in an email response.
Nicholas WeaverA company entrusted with so many sensitive logins should absolutely encrypt the information, said a researcher at UC Berkeley’s International Computer Science Institute (ICSI) and a lecturer at UC Davis.
“If they’re hosting customer data on a third-party system like Amazon, it’s a good idea to encrypt it,” Weaver said. “If they tell people to leave the credential, that means it’s not encrypted. So the first mistake is leaving the Amazon credential in your Git archive. The second mistake is using S3 without using encryption on top of it. The former While it’s bad, it’s forgivable, but the latter is inexcusable given their business.”
