Australian, British and US authorities this week imposed financial sanctions on a Russian man accused of stealing the data of nearly 10 million customers of the Australian health insurance giant medical bank. 33 years old Alexander Yermakov He allegedly stole and exfiltrated Medibank data while working with one of Russia’s most destructive ransomware groups, but little additional information about the defendant has been revealed. Here’s a detailed look at the activities of Mr. Ermakov’s alleged hacktivists.

Aleksandr Ermakov, 33, Russian. Picture: Australian Department of Foreign Affairs and Trade.
The charges against Ermakov mark the first time Australia has sanctioned cybercriminals. The documents released by the Australian government include multiple photos of Yermakov, clearly trying to convey the message that this is personal.
It’s not hard to see why. Attackers who broke into Medibank in October 2022 stole 9.7 million records of current and former Medibank customers. When the company refused to pay a $10 million ransom demand, the hackers selectively leaked highly sensitive health records, including those related to abortion, HIV, and alcoholism.
The U.S. government says Ermakov and other participants behind the Medibank hack are believed to be tied to a Russian-backed cybercrime group evil.
“REvil was one of the most notorious cybercriminal gangs in the world until its disappearance in July 2021. REvil was a ransomware-as-a-service (RaaS) operation, often motivated by financial gain.” U.S. Treasury Department read. “REvil ransomware has been deployed on approximately 175,000 computers worldwide, and at least $200 million has been paid in ransom.”
The sanctions say Ermakov used multiple aliases on Russian cybercriminal forums, including Gustave Dole, Jim Jonesand “Blade Runner.”A search for the GustaveDore account on the cyber intelligence platform Intel 471 showed that the user created a ransomware adjunct in November 2021 called sugar (also known as Encoded01), focuses on single computers and end users rather than companies.
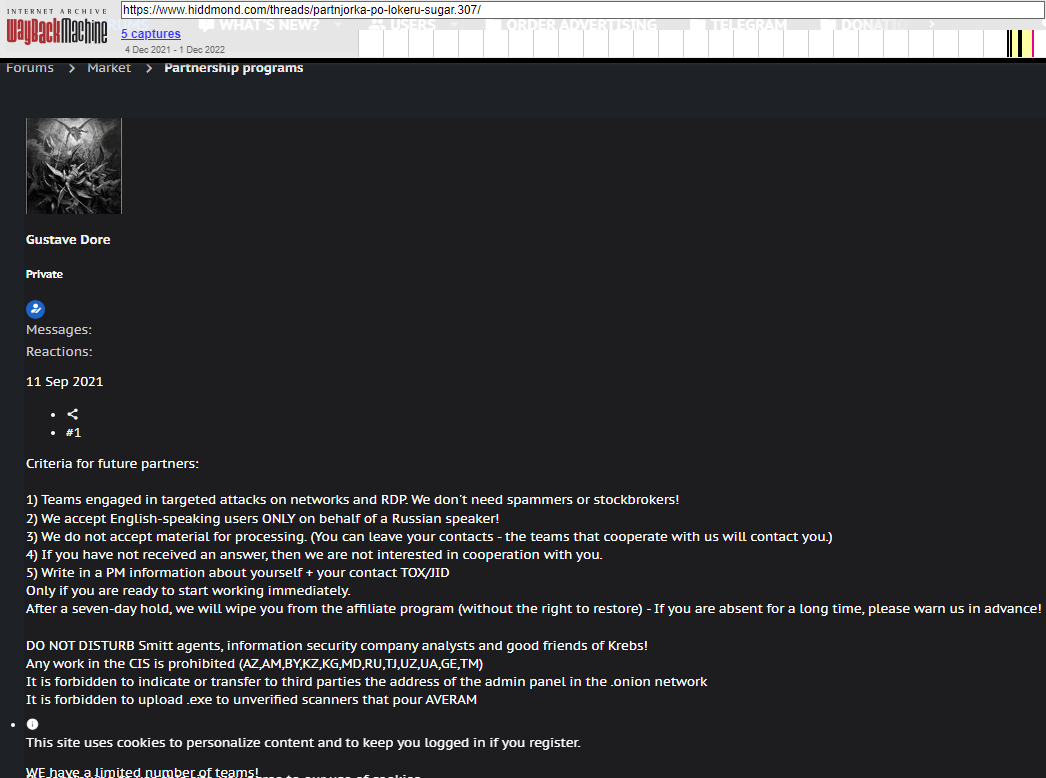
Advertisements for the ransomware-as-a-service program Sugar posted by GustaveDore.
In November 2020, analysts at Intel 471 concluded that Gustave Dore’s pseudonym Jim Jones “is using and operating multiple different ransomware variants, including a private, undisclosed variant and one developed by the REvil gang.”
In 2020, Gustav Dole advertised on several Russian discussion forums that he was a member of a Russian technology company called Shtazi, where he could be employed in computer programming, web development and “reputation management” . Shtazi’s website is still operational today.
Google Translate version of Shtazi dot ru. Image: Archive.org.
The third result of your current search Shtazi[.]Ru In Google is a Instagram Posts from user named Mikhail Borisovich Shefir, he promoted Shtazi’s services as if it were his business too. If that name sounds familiar, that’s because in December 2023, KrebsOnSecurity identified Shefel as a “Rescator,” a cybercriminal whose identity was linked to data stolen from companies like big box retailer Target and Home Depot in 2013 and 2014. Tens of millions of payment cards are linked. .
How close was the connection between Gustave Dole and Mr. Scheifele?The Treasury Department’s sanctions page says Ermakov used the email address ae.ermak@yandex.ru. Searching for this email on DomainTools.com shows that it is only used to register a domain: million 1[.]com. DomainTools further discovered that a phone number associated with Mr. Shefel (79856696666) was used to register two domains: mega[.]passwordand Shtazi[.]net.
Reports in December 2023 referred to Mr. Schaefer as Rescart and noted that Mr. Schaefer had recently changed his last name to “Lenin,” and launched a service called Lenin[.]I sold Soviet-era ruble banknotes bearing the portrait of Vladimir Lenin, the founding father of the Soviet Union. Mr. Schaefer’s Instagram account contains images of stacked Soviet-era ruble notes, as well as multiple links to Shtazi.

Mikhail Borisovich Shefel has the best Instagram account in the world.
In a report published this week, Intel 471 said investigators linked Ermakov to REvil because the stolen Medibank data was posted on a blog that was at one time controlled by REvil affiliates who carried out the Attacks and paid affiliate fees to the gang.
But by the time the Medibank hack occurred, the REvil group had largely dispersed after a series of high-profile attacks led to the organization being disrupted by law enforcement. November 2021, Europol Announced the arrests of seven REvil affiliates who have collectively made more than $230 million worth of ransom demands since 2019. Meanwhile, US authorities have filed two indictments against two alleged REvil cybercriminals.
“However, Medibank data posted on the blog suggested a connection to the group, although the connection was not clear at the time,” Intel 471 wrote. “In retrospect, this makes sense because Ermakov’s organization was also an affiliate of REvil.”
It is easy to think that such sanctions are ineffective because as long as Yermakov remains in Russia, he does not have to worry about being arrested.However, his alleged high-level membership in REvil positions him as someone who may own large amounts of cryptocurrency, he said Patrick GrayCo-host and founder of the Australian Security News Podcast risky business.
“I’ve seen some people scoff at sanctions … but the sanctions part is really not as important as the doxing part,” Gray said. “Because this guy’s situation is getting more complicated. He probably needs to pay a bribe to stay out of trouble. Now every criminal in Russia knows he’s a 33-year-old guy with a lot of Bitcoin. So it doesn’t matter to him. Not a happy moment.”
