It has been observed that a threat actor named Water Curupira is actively distributing pickup robot In 2023, loader malware will become part of spam campaigns.
“The operators of PikaBot conducted a phishing campaign that targeted victims through two of its components (loader and core module), which allowed unauthorized remote access and allowed access via its command and Execute arbitrary commands over a connection established by a control and control (C&C) server,” Trend Micro said in a report released today.

The event kicks off in the first quarter of 2023 and runs until the end of June before heating up again in September. It also overlaps with previous campaigns using similar tactics to spread QakBot, particularly those orchestrated by cybercriminal groups such as TA571 and TA577.
The increase in the number of phishing campaigns related to PikaBot is believed to be a result of QakBot being destroyed in August, with DarkGate emerging as an alternative.
PikaBot is primarily a loader, meaning it is designed to launch another payload, including Cobalt Strike, a legitimate post-exploitation toolkit that often acts as a precursor to ransomware deployment.
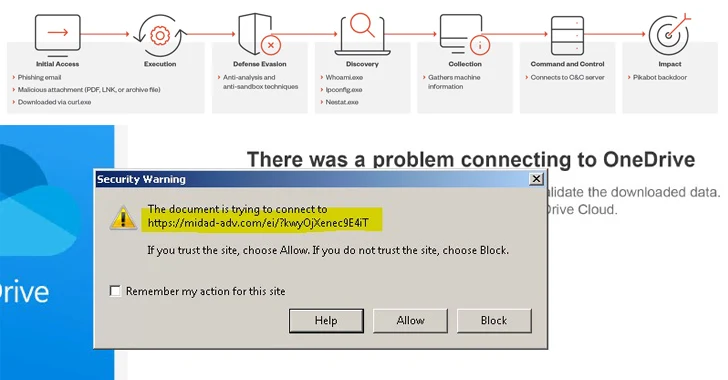
The attack chain leverages a technique called email thread hijacking, which uses an existing email thread to trick the recipient into opening a malicious link or attachment, effectively initiating the malware execution sequence.

The ZIP archive attachment contains JavaScript or IMG files that serve as a launchpad for PikaBot. For its part, the malware checks the language of the system and stops execution if it is Russian or Ukrainian.
Next, it collects detailed information about the victim’s system and forwards it to the C&C server in JSON format. Water Curupira’s campaign aimed to abandon Cobalt Strike, which subsequently led to the deployment of the Black Basta ransomware.
“This threat actor also conducted several DarkGate spam campaigns and a small number of IcedID campaigns in the first few weeks of Q3 2023, but has since turned exclusively to PikaBot,” Trend Micro said.