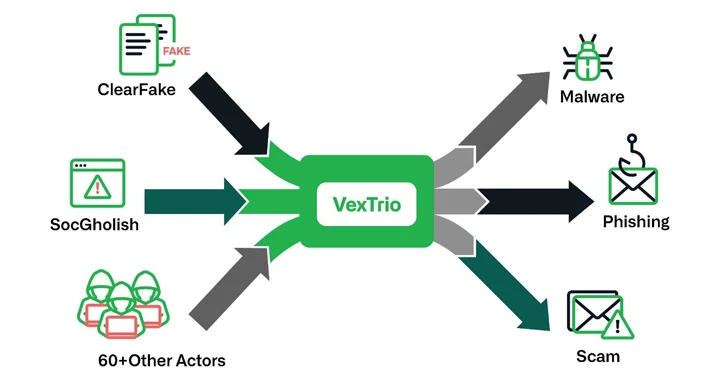
The threat actor behind ClearFake, SocGholish and dozens of other attackers has partnered with another named vix trio New findings from Infoblox reveal that this was part of a large-scale “criminal alliance scheme”.
The company said the latest developments demonstrated “the breadth of their activities and depth of connections within the cybercriminal industry” and described VexTrio as “the largest single malicious traffic proxy described in the security literature.”
VexTrio is believed to have been active since at least 2017 due to malicious campaigns that use Dictionary Domain Generation Algorithm (DDGA) generated domains to spread scams, riskware, spyware, adware, potentially unwanted programs ( PUP) and pornographic content.
This also includes a 2022 active cluster that distributed Glupteba malware after Google attempted to take down much of its infrastructure in December 2021.
In August 2023, the group orchestrated a widespread attack involving compromised WordPress sites, conditionally redirecting visitors to intermediate command and control (C2) and DDGA domains.
The reason these infections are so severe is because the threat actors leverage the Domain Name System (DNS) protocol to retrieve redirect URLs, effectively acting as a DNS-based traffic distribution (or delivery or direction) system (TDS).

It is estimated that VexTrio operates a network of more than 70,000 known domains, proxying traffic for as many as 60 affiliates, including ClearFake, SocGholish and TikTok Refresh.
“VexTrio operates their affiliate program in a unique way, providing each affiliate with a small number of dedicated servers,” Infoblox said in an in-depth report shared with The Hacker News. “VexTrio’s affiliation appears to be long-standing.”

Not only can its attack chain include multiple actors, VexTrio also controls multiple TDS networks, routing website visitors to illegal content based on their profile attributes such as geolocation, browser cookies, and browser language settings. Maximize profits while filtering out the rest.
These attacks are characterized by infrastructure owned by different parties, in which participating affiliates forward traffic originating from their own resources (e.g., compromised websites) to VexTrio-controlled TDS servers. In the next stage, this traffic will be redirected to other scam websites or malicious alliances.
“VexTrio’s network uses TDS to consume other cybercriminals’ network traffic and sell that traffic to its own customers,” researchers said. “VexTrio’s TDS is a large and complex cluster of servers that exploits data to Ten thousand domains to manage all network traffic passing through it.”

There are two types of TDS operated by VexTrio, one based on HTTP that handles URL queries with different parameters, and another based on DNS, which will be used for the first time in July 2023.
It’s worth noting at this stage that while SocGholish (aka FakeUpdates) is a VexTrio affiliate, it also operates other TDS servers such as Keitaro and Parrot TDS, with the latter acting as a mechanism for redirecting web traffic to SocGholish’s infrastructure .
According to Palo Alto Networks Unit 42, Parrot TDS has been active since October 2021, although evidence suggests it may have existed as early as August 2019.
“Websites with Parrot TDS inject malicious script into existing JavaScript code hosted on the server,” the company said in an analysis last week. “The injected script consists of two components: one with used to analyze the victim’s initial login script, as well as a payload script that can direct the victim’s browser to malicious locations or content.”

Injections, in turn, are facilitated by exploiting known security vulnerabilities in content management systems (CMS) such as WordPress and Joomla!
The attack vectors used by VexTrio affiliate networks to harvest victim traffic are no different, as they primarily target websites running vulnerable versions of the WordPress software to insert malicious JavaScript into their HTML pages.
In one instance spotted by Infobox, a compromised website in South Africa was found to have JavaScript injected from ClearFake, SocGholish and VexTrio.
That’s not all. In addition to contributing web traffic to numerous web campaigns, VexTrio is also suspected of running some of its own campaigns, making money by abusing referral programs and receiving web traffic from affiliates and then reselling that traffic to downstream threat actors.
Infoblox concluded: “VexTrio’s advanced business model facilitates collaboration with other players and creates a sustainable and resilient ecosystem that is extremely difficult to disrupt.”
“Due to the complex design and tangled nature of affiliate networks, precise classification and attribution are difficult to achieve. This complexity has allowed VexTrio to thrive while remaining unknown in the security industry for more than six years.”