
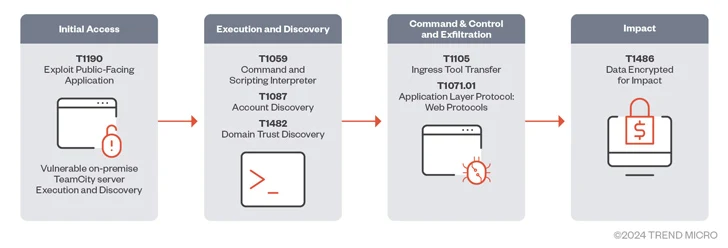
Multiple threat actors are exploiting recently disclosed security vulnerabilities in JetBrains TeamCity software to deploy ransomware, cryptocurrency miners, Cobalt Strike beacons, and a Golang-based remote access Trojan called Spark RAT.
These attacks exploit CVE-2024-27198 (CVSS score: 9.8), which allows attackers to bypass authentication measures and gain administrative control of affected servers.
“The attackers were then able to install malware that could access their command and control (C&C) servers and execute other commands, such as deploying Cobalt Strike beacons and remote access trojans (RATs),” Trend Micro said in a new report. ).” .
“Ransomware can then be installed as the final payload to encrypt files and demand a ransom from the victim.”
After the vulnerability was publicly disclosed earlier this month, threat actors associated with the BianLian and Jasmin ransomware families have weaponized the vulnerability and removed the XMRig cryptocurrency miner and Spark RAT.
Organizations that rely on TeamCity for CI/CD processes are advised to update their software as soon as possible to protect against potential threats.

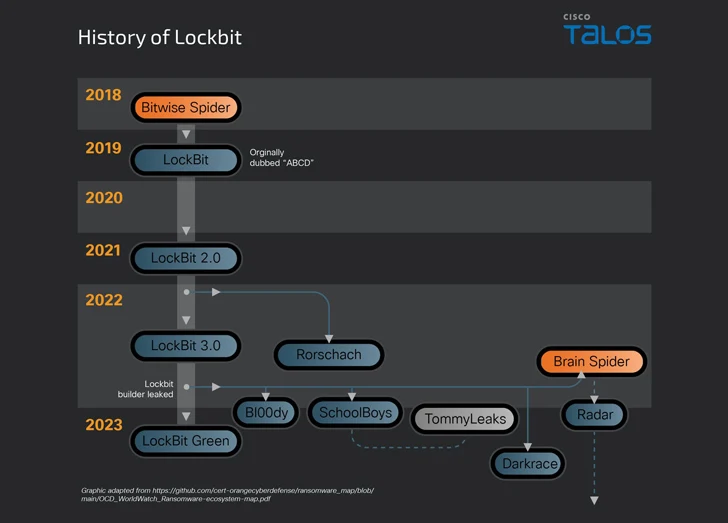
This development comes as ransomware continues to become both powerful and profitable, with new viruses such as DoNex, Evil Ant, Lighter, RA World and WinDestroyer emerging in the wild, and even as notorious cybercriminal gangs like LockBit continue to flout the law. Accept affiliates into their program to take enforcement action against them.
WinDestroyer, in particular, is capable of encrypting files and rendering target systems unusable and data unrecoverable, raising the possibility that the threat actors behind it are geopolitically motivated.
“One of the major issues in dealing with ransomware crimes is the nature of affiliate programs, with actors often working for multiple RaaS organizations simultaneously,” Cisco Talos said. “It requires sustained strategic efforts to significantly compromise RaaS operations and reduce the ability of these groups to regenerate. .”
Data shared by the FBI’s Internet Crime Complaint Center (IC3) shows that 2,825 ransomware infections were reported in 2023, resulting in adjusted losses of more than $59.6 million. Of these, 1,193 are from organizations in the critical infrastructure sector.
The top five ransomware variants affecting U.S. critical infrastructure include LockBit, BlackCat (aka ALPHV or Noberus), Akira, Royal, and Black Basta.
In addition to providing court affiliates with a larger share of the proceeds, there is increasing cooperation between different ransomware groups, which share malicious tools with each other.
These partnerships also manifest themselves in the form of phantom groups, in which one ransomware operation outsources its skills to another ransomware operation, as seen in the cases of Zeon, LockBit, and Akira.
Symantec, a unit of Broadcom, revealed in a report released last week that “even though the number of attacks claimed by ransomware attackers fell by more than 20% in the fourth quarter of 2023, ransomware activity is still on the rise.”
According to statistics released by NCC Group, the total number of ransomware cases in February 2024 increased by 46% from January, from 285 to 416, including LockBit (33%), Hunters (10%), BlackCat (9%), Kirin (9%), Bianlian (8%), Play (7%) and 8Base (7%).
Matt Hull, global director of threat intelligence at NCC Group, said: “Recent law enforcement activity has the potential to polarize the ransomware landscape into a cluster of smaller RaaS operators that are highly active and active due to their agility in underground forums and markets. It’s harder to detect.”, said.

“It appears that the attention generated by larger ‘brand’ ransomware such as LockBit and Cl0p is leading to new small, general-purpose RaaS affiliate partnerships becoming the norm. As a result, detection and attribution may become more difficult for affiliates It may be easy to switch providers due to low barriers to entry and minimal capital investment.”
Threat actors are also finding new ways to infect victims by exploiting vulnerabilities and evading detection, primarily in public-facing applications, and perfecting them by increasingly relying on legitimate software and living off the land (LotL) strategy. technology.
Utilities such as TrueSightKiller, GhostDriver, and Terminator are also popular among ransomware attackers, who exploit Bring Your Own Vulnerable Driver (BYOVD) technology to disable security software.
“BYOVD attacks are attractive to threat actors because they can provide a way to disable AV and EDR solutions at the kernel level,” Sophos researchers Andreas Klopsch and Matt Wixey said in a report this month. “ The large number of known vulnerable drivers means attackers have many options.”
