The U.S. Securities and Exchange Commission (SEC) confirmed that hackers successfully took control of the phone number associated with his Twitter account and used it to post unauthorized messages.
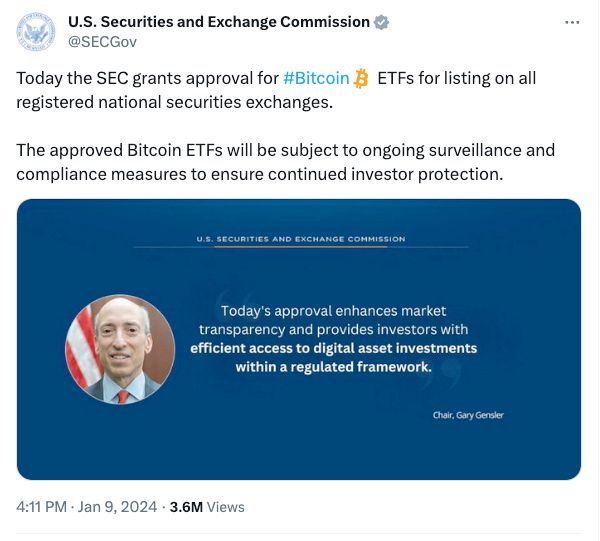
Earlier this month, the U.S. Securities and Exchange Commission posted an unauthorized announcement to 660,000 Twitter followers claiming that a highly anticipated Bitcoin ETF had been approved, causing a temporary jump in the value of the cryptocurrency.
When the truth emerged, Bitcoin’s price fell back, meaning some investors may have suffered losses while others may have profited from the fake news.
The next day, the SEC announced it had a real Bitcoin ETF.
So, how did hackers hijack the SEC’s Twitter account?
Here’s what the SEC says happened:
Six months before the hack, the SEC disabled two-factor authentication (2FA) on its Twitter account.
Subsequently, hackers successfully took control of the mobile phone number associated with the SEC Twitter account through a “SIM swap” attack. This is where scammers succeed in tricking cell phone provider staff into letting them take control of someone else’s phone number. Sometimes scammers will tell telecommunications companies personal details about their targets, tricking them into believing they are someone they are not.
Unfortunately for the SEC, Twitter makes Reset account password Just know and access its associated mobile phone number.
The hackers now have control of the account and can reset the account’s password at will and post unauthorized messages.
So why did the SEC disable 2FA on its Twitter account in the first place? The SEC has not yet taken a position, but Twitter warned in February 2023 that if SMS 2FA was not disabled, accounts would be at risk of being locked out.
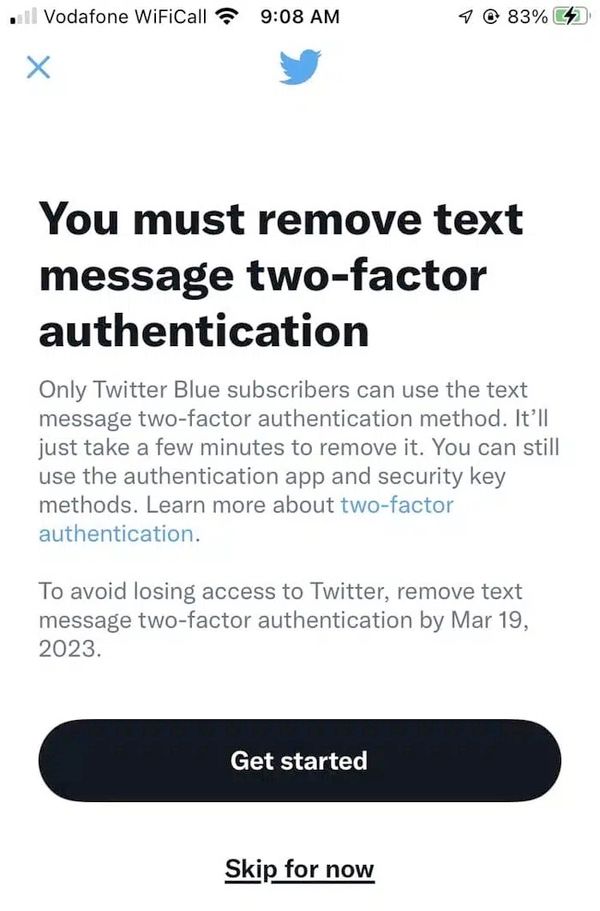
reason? Twitter wants its users to pay to subscribe to Twitter Blue, and Twitter rolled out SMS-based 2FA as a premium feature, which I think is a dangerous move. (The reality is that SMS has been considered a more secure implementation of 2FA than other alternatives for years, so offering it as a premium feature sends a very bad message in my opinion).
Sure enough, in March 2023, Twitter removed SMS-based 2FA from all accounts except those with paid subscriptions to Twitter Blue. Anyone who still has SMS-based 2FA enabled and is unwilling to dig into their wallet to pay Twitter will be locked out of their account.
The SEC said that its account had had 2FA enabled, but after discovering that it could not access its account in July 2023, it asked Twitter support to disable it. Unfortunately, the SEC has since not re-enabled the security feature (although it has enabled 2FA (hopefully not in a SMS-based form) on all of its accounts since the unauthorized tweet was posted.
All in all, it’s a mess. It’s especially embarrassing for the SEC.
Not only does the SEC have a habit of hammering companies that don’t take appropriate steps to protect themselves from hackers, but its chairman Tweets about the importance of multi-factor authentication The SEC’s own accounts were not protected by it at the time.
