.jpg)
The Russian-speaking cybercriminal organization is named red curly hair A legitimate Microsoft Windows component called the Program Compatibility Assistant (PCA) is exploited to execute malicious commands.
“The Program Compatibility Assistant Service (pcalua.exe) is a Windows service designed to identify and resolve compatibility issues with older programs,” Trend Micro said in an analysis report released this month.
“Adversaries could exploit this utility to enable command execution and bypass security restrictions by using it as an alternative command line interpreter. In this investigation, threat actors used this tool to mask their activities.”

RedCurl, also known as Earth Kapre and Red Wolf, has been active since at least 2018, organizing corporate cyber espionage attacks against entities located in Australia, Canada, Germany, Russia, Slovenia, the United Kingdom, Ukraine and the United States.
In July 2023, FACCT revealed that a major Russian bank and an Australian company were targeted by threat actors in November 2022 and May 2023, stealing confidential company secrets and employee information.
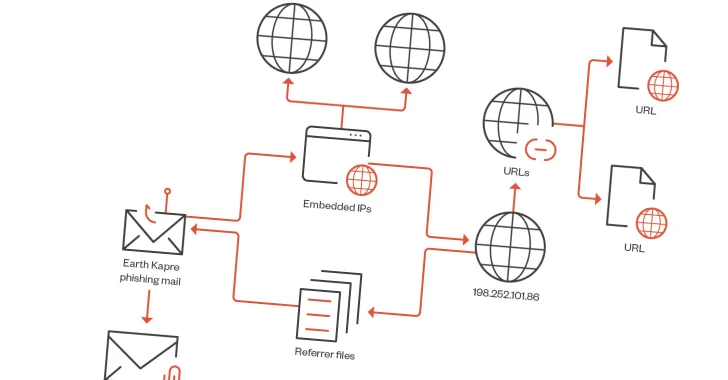
The attack chain examined by Trend Micro requires the use of phishing emails containing malicious attachments (.ISO and .IMG files) to initiate a multi-stage process that first uses cmd.exe to remotely download a legitimate file named “curl” The utility server then acts as a conduit to the loader (ms.dll or ps.dll).
In turn, the malicious DLL file uses PCA to spawn a downloader process, which is responsible for establishing a connection to the same domain used by curl to obtain the loader.
The Impacket open source software was also used in the attack to execute unauthorized commands.
The connection to Earth’s Kapre stems from overlap in command and control (C2) infrastructure and similarity to known downloader artifacts used by the group.
“This case highlights the ongoing and active threat posed by Earth Kapre, which targets a variety of industries in multiple countries,” Trend Micro said.

“The attackers used sophisticated tactics, such as abusing PowerShell, curl, and the Program Compatibility Assistant (pcalua.exe) to execute malicious commands, demonstrating their dedication to evading detection within the target network.”
This development comes as Russian nation-state group Turla (aka Iron Hunter, Peptic Ursa, Secret Blizzard, Snake, Uroburos, Venomous Bear, and Waterbug) begins deploying the .NET-based Kazul backdoor using a new wrapper DLL codenamed Pelmeni .
Pelmeni – disguised as a library related to SkyTel, NVIDIA GeForce Experience, vncutil or ASUS – loaded via DLL sideloading. Lab52 said that once the legitimate software installed on the machine calls the spoofed DLL, it decrypts and launches Kazuar.