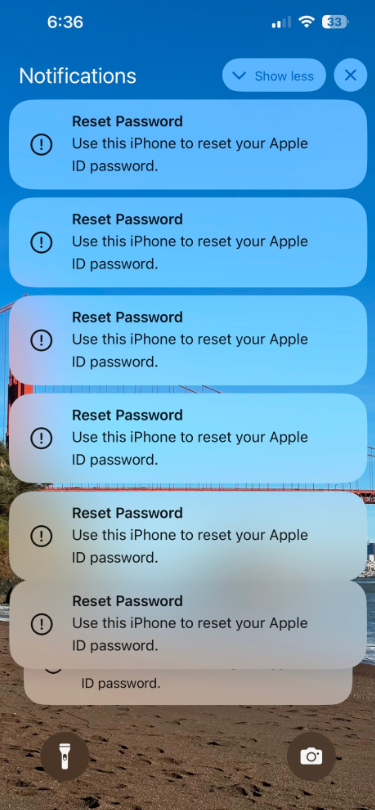
Some apple Customers recently reported that they were targeted by elaborate phishing attacks that appeared to involve a bug in Apple’s password reset feature. In this case, the targeted Apple device is forced to display dozens of system-level prompts that prevent the device from being used until the recipient responds with “Allow” or “Don’t allow” to each prompt. Assuming the user successfully presses the wrong button in numerous password reset requests, the scammer will call the victim while spoofing Apple Support on the caller ID, stating that the user’s account has been compromised and Apple Support requires “verification.” ” one-time code.
Patel said he received many notifications from Apple at once, some of which he received all at once.
Parth Patel is an entrepreneur trying to build a new startup in the cryptocurrency space. March 23, Patel Recorded on Twitter/X Recent phishing campaigns targeting him involve so-called “push bombing” or “MFA fatigue” attacks, in which phishers abuse the capabilities or weaknesses of multi-factor authentication (MFA) systems to flood target device(s) with Alerts for approved password changes or logins.
“All my devices started exploding, my watch, my laptop, my phone,” Patel told KrebsOnSecurity. “Just like the system notification approval issued by Apple [a reset of the account password], but I can’t do anything else with my phone. I had to go through and reject over 100 notifications. “
Faced with such a flood of messages, some people may end up clicking “Allow” on the recurring password reset prompts – just so they can use their phone again. Someone else may inadvertently approve one of the prompts, and the prompt will appear on the user’s Apple Watch if it has that prompt.
But the attackers in this campaign had an ace up their sleeve: After rejecting all password reset prompts from Apple, Patel said he received a call on his iPhone that said it was from Apple Support. (The number displayed is 1-800-275-2273, Apple’s real customer support hotline).
“I picked up the phone and I was very skeptical,” recalls Patel. “So I asked them if they could verify some information about me and after hearing some aggressive typing on his end, he gave me all the information he had about me and it was completely accurate.”
All this except his real name.Patel said that when he asked the fake Apple support representative to verify the name they had on their Apple account, the caller gave a name that was not his but one that Patel had only seen in background reports about him. By name, these reports are for sale on a people search site called People Data Lab.
Patel said he had worked diligently to remove his information from multiple people search sites and discovered that PeopleDataLabs uniquely and consistently listed the inaccurate name as an alias in his consumer profile.
“For some reason, when you search for me, PeopleDataLabs shows three profiles, two of which are mine, but one of which is an elementary school teacher from the Midwest,” said Patel. “I asked them to verify my name and they said it was Anthony.”
Patel said the goal of the voice phisher is to trigger an Apple ID reset code to be sent to the user’s device, which is a text message containing a one-time password. If the user provides a one-time code, the attacker can reset the account password and lock the user out. They can then also remotely wipe all of the user’s Apple devices.
Phone number is key
Chris is a cryptocurrency hedge fund owner who asked that only his first name be used to avoid setting a larger target for himself. Chris told KrebsOnSecurity that he experienced a very similar phishing attempt in late February.
“When I got the first alert, I clicked ‘Don’t allow,’ but then I got about 30 more notifications in a row,” Chris said. “I thought maybe I was sitting on my phone weirdly or accidentally pressing a button that was causing this, so I just denied it all.”
Chris said that in the following days, the attacker continued to send reset notifications to his device, and at one point his iPhone received a call claiming to be from Apple support.
“I said I would call them back and hung up,” Chris said, demonstrating the proper response to such an unsolicited request. “When I called the actual Apple company, they couldn’t confirm if anyone had been on the support call with me at the time. They just said that Apple makes it very clear that it never makes outbound calls to customers – unless the customer requests contact. .”

Chris was so scared that someone was trying to hijack his digital life that he said he changed his password and went to an Apple store to buy a new iPhone. From there, he created a new Apple iCloud account using a brand new email address.
Chris said he subsequently received more system alerts on his new iPhone and iCloud account – Been sitting at the local Apple Genius Bar.
Chris told KrebsOnSecurity that his Genius Bar technology is confused about the source of the alerts, but Chris said he suspects whatever method phishers are abusing to quickly generate these Apple system alerts requires knowing the phone number of the target Apple account.After all, that is only Some aspects of Chris’ new iPhone and iCloud account haven’t changed.
careful!
“Ken” is a security industry veteran who wishes to remain anonymous. Ken said he started receiving these unsolicited system alerts on his Apple devices earlier this year, but he didn’t receive any fake Apple support calls as others have reported.
“This happened to me recently at 12:30 in the middle of the night,” Ken said. “Even though I set my Apple Watch to be quiet when I usually go to sleep at night, it still wakes me up with one of the alarms. Thank God I didn’t press “Allow,” which is what appears on my watch. An option. I have to scroll the watch wheel to see and press the ‘disallow’ button.”
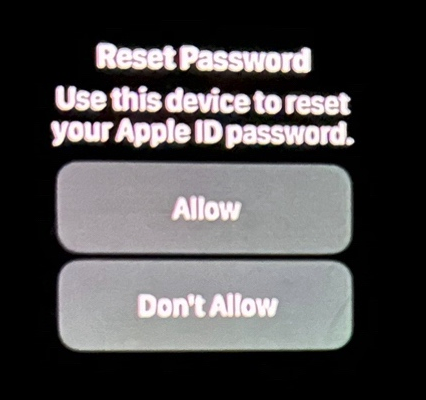
Ken shared this photo of the alert he took on his watch that woke him up at 12:30 a.m. Ken said he had to scroll on the watch face to see the “Don’t Allow” button.
Ken said he was so disturbed by the idea that he could turn over his watch in his sleep and let criminals take over his Apple account that he contacted real Apple support and was eventually upgraded to an Apple Senior Engineer. Engineers assured Ken that opening his account’s Apple recovery key would stop the notifications once and for all.
Recovery keys are an optional security feature that Apple says “helps improve the security of your Apple ID account.” It’s a randomly generated 28-character code that should disable Apple’s standard account recovery process when you enable a recovery key. The problem is, enabling it isn’t a simple process, and if you lose that code and all your Apple devices, you’ll be locked out permanently.
Ken said he followed instructions and enabled a recovery key for his account, but that didn’t stop the unsolicited system alerts from appearing on all his devices every few days.
KrebsOnSecurity tested Ken’s experience and can confirm that enabling a recovery key does not prevent password reset prompts from being sent to associated Apple devices. Visit Apple’s “Forgot Password” page – https://iforgot.apple.com – where visitors are asked to provide their email address and enter a verification code.
After that, the page will display the last two digits of the phone number tied to your Apple account. Regardless of whether the user has enabled an Apple recovery key, filling in the missing numbers and clicking “Submit” on the form will send a system alert.
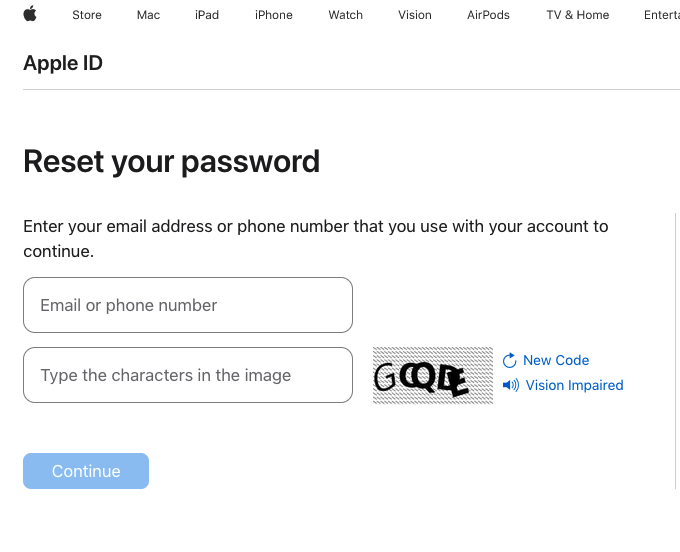
Password reset page at iforgot.apple.com.
interest rate limit
What properly designed authentication system would send dozens of password change requests in a short period of time before the first request has even been executed by the user? Could this be caused by a bug in Apple’s system?
Apple has not yet responded to a request for comment.
Throughout 2022, a criminal hacker group called LAPSUS$ used MFA bombing to conduct huge intrusions on the following websites: Cisco, Microsoft and Uber. In response, Microsoft began enforcing an “MFA number matching” feature that displays a series of numbers to users trying to log in using their credentials. These numbers must then be entered into the Microsoft Authenticator app on the account owner’s mobile device to verify that they are signing in to the account.
Kishan Bagaria An amateur security researcher and engineer who founded the texts.com website (now owned by Automattic), he was convinced that something was wrong with Apple. In August 2019, Bagaria reported a vulnerability to Apple that allowed an exploit that he called “AirDoS” because it could be used to allow an attacker to spam all nearby iOS devices indefinitely and via system-level Tips for sharing files via AirDrop (one file) Apple products have built-in sharing functionality.
Apple fixed the vulnerability nearly four months later in December 2019 and thanked Bagaria in a related security advisory. Bagaria said Apple’s fix for the bug was to add stricter rate limits to AirDrop requests, and he suspects someone has found a way to get around Apple’s restrictions on how many password reset requests can be sent in a given time frame. Rate limiting.
“I think this may be a legitimate rate limiting bug on Apple’s part and should be reported,” Bagaria said.