Kirin ransomware group has targeted big problema street newspaper sold by homeless and disadvantaged people.
as Record According to reports, a post on the Kirin darknet leak website claimed that the group had stolen 550 GB of confidential information.
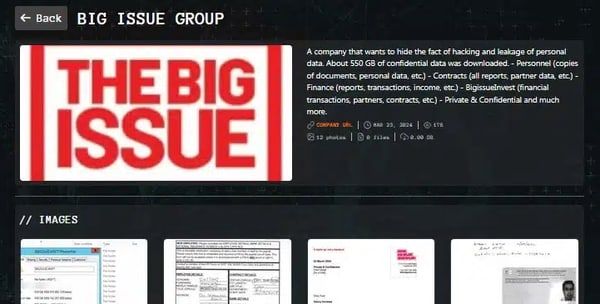
Chealing released photos of Big Issue Group chief executive Paul Cheal’s driving license and salary details to substantiate their claims.
In addition, the bank and passport details of Danyal Sattar, chief executive of Big Issue’s social impact investing arm, appear to have been leaked.
Another screenshot shared by the organization appears to show a document containing scans of employee passports, a spreadsheet containing employee details including full names, email and home addresses, and banking information.
In a statement shared with the media, Big Issue Group confirmed that it had been hit by a cyber attack, but did not mention whether it had received a ransom demand or whether it was prepared to pay the extortionists:
“Last week, Big Issue Group experienced a cyber incident. Upon becoming aware of this, we immediately took steps to restrict access to our systems and are working with external IT security experts. An investigation into the incident is ongoing. Thank you After taking proactive steps, we have been able to begin restoring our systems with limited disruption to operations.”
The world’s most widely circulated street newspaper confirmed that some of its data had been posted to the dark web and that it was working with external cybersecurity experts, law enforcement and regulators.
Perhaps most relevant for people who like to support their vendors big problemThe newspaper said the cyber attack had not affected publication and distribution.
Qillin (also known as Agenda) is a ransomware-as-a-service operation. Qillin was first discovered in August 2022 and is known for attacking organizations with ransomware written in Rust and Go.
Qillin works with affiliates to infect, encrypt, and steal data from organizations. Victims receive ransom demands stating that their stolen information will be leaked if they do not pay the decryption key.
Past victims of Kirin ransomware attacks include auto parts giant Yanfeng and Australia’s court services.
