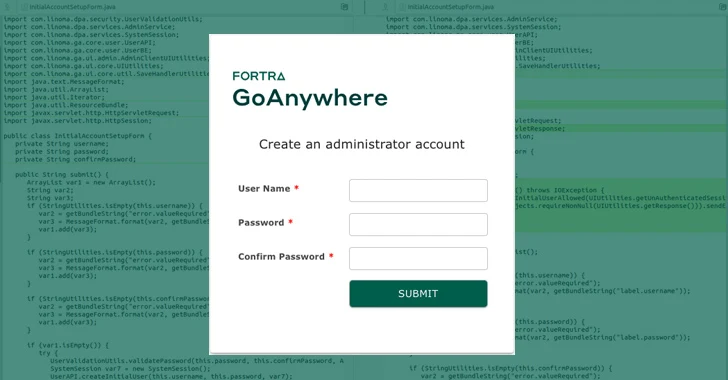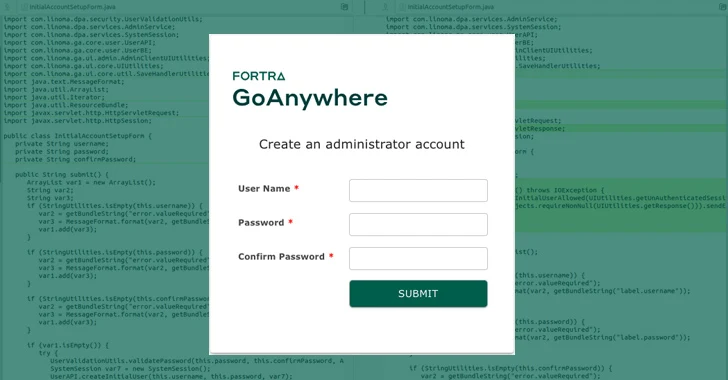
A critical security vulnerability has been disclosed in Fortra’s GoAnywhere managed file transfer (MFT) software that could be abused to create new administrator users.
Tracked as CVE-2024-0204this question has a CVSS score of 9.8 out of 10.
“An authentication bypass in Fortra GoAnywhere MFT prior to 7.4.1 allowed unauthorized users to create administrator users through the admin portal,” Fortra said in an advisory posted on January 22, 2024.

Users unable to upgrade to version 7.4.1 can apply a workaround in non-container deployments by deleting the InitialAccountSetup.xhtml file in the installation directory and restarting the service.
For container-deployed instances, it is recommended to replace the archive with an empty archive and restart.
Mohammed Eldeeb and Islam Elrfai of Cairo-based Spark Engineering Consultants are thought to have discovered and reported the flaw in December 2023.
Horizon3.ai, a cybersecurity company, has released a proof-of-concept (PoC) vulnerability for CVE-2024-0204. The company stated that the issue is caused by a path traversal vulnerability in the “/InitialAccountSetup.xhtml” endpoint. The vulnerability can be exploited to create administrative users.
“The simplest indicator of compromise that can be analyzed is any new addition to the admin user group in the GoAnywhere Admin Portal Users -> Admin Users section,” said Horizon3.ai security researcher Zach Hanley.

“If the attacker has left this user here, you may be able to observe their last login activity here to estimate the approximate date of the compromise.”
While there is no evidence that CVE-2024-0204 is actively exploited in the wild, last year the Cl0p ransomware group abused another flaw in the same product (CVE-2023-0669, CVSS score: 7.2), resulting in nearly 130 victims attack.