Threat actors linked to North Korea are called Kim Soo-ki It has been observed that Malware (also known as Black Banshee, Emerald Sleet or Springtail) is changing its tactics and using compiled HTML Help (CHM) files as a vector to spread malware in order to collect sensitive information.
Kimsuky has been active since at least 2012, targeting entities located in South Korea as well as North America, Asia, and Europe.
According to Rapid7, the attack chain leveraged weaponized Microsoft Office files, ISO files, and Windows Shortcut (LNK) files, and the group also leveraged CHM files to deploy malware on infected hosts.
The cybersecurity firm attributed the activity to Kimsuky with moderate confidence, citing similar espionage activity observed in the past.

“While CHM files were originally designed as help files, they have also been used for malicious purposes, such as distributing malware, because they can execute JavaScript when opened,” the company said.
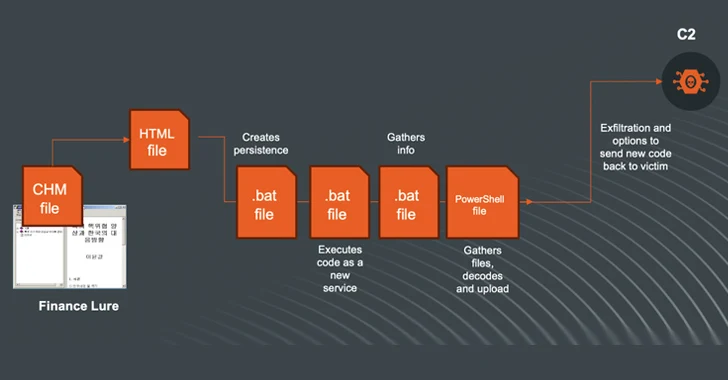
CHM files are delivered in ISO, VHD, ZIP or RAR files and when opened execute a Visual Basic Script (VBScript) to set up persistence and connect to a remote server to obtain the next stage payload of sensitive data responsible for collection and exfiltration.
Rapid7 said the attacks are ongoing and evolving, targeting organizations in South Korea. It also identified an alternative infection sequence that uses a CHM file as a starting point, dropping batch files responsible for gathering information and a PowerShell script that connects to the C2 server and transfers data.
“The modus operandi and reuse of code and tools indicate that threat actors are actively using and refining/reinventing their techniques and strategies to gather intelligence from victims,” the report said.
Broadcom-owned Symantec has revealed that Kimsuky attackers are spreading malware impersonating apps from legitimate public entities in South Korea.
“When compromised, the implant installs the Endor backdoor malware,” Symantec said. “This threat allows the attacker to collect sensitive information from the victim or install additional malware.”
It is worth noting that Golang-based Endor and Troll Stealer (also known as TrollAgent) were recently deployed for cyber attacks against users who downloaded security programs from the Korean Construction Related Association website.

The United Nations investigated 58 suspected cyberattacks carried out by North Korean nation-state actors between 2017 and 2023, which generated $3 billion in illicit proceeds to further North Korea’s nuclear weapons program.
“Hacker groups affiliated with the General Reconnaissance Directorate reportedly continue to launch a large number of cyberattacks,” the report said. “Trends include targeting defense companies and supply chains, and increasing sharing of infrastructure and tools.”
The Reconnaissance General Bureau (RGB) is North Korea’s main foreign intelligence agency and consists of the threat clusters of the widely tracked Lazarus Group and its affiliates Andariel and Brunorov, as well as Kim Suki.
“Kimsuky has shown interest in using generative artificial intelligence, including large language models, possibly for coding or writing phishing emails,” the report further adds. “Kimsuky was observed using ChatGPT.”