
McPhee Labs’ investigation revealed that a new information-stealing program has been discovered that leverages Lua bytecode to enhance stealth and sophistication.
The cybersecurity firm has assessed it as a variant of a known malware called RedLine Stealer because the command and control (C2) server IP address has been previously identified as associated with the malware.
RedLine Stealer was first recorded in March 2020 and is typically spread via email and malvertising campaigns either directly or via exploit kits and loader malware such as dotRunpeX and HijackLoader.
This off-the-shelf malware is capable of collecting information from cryptocurrency wallets, VPN software, and web browsers, such as saved credentials, autocomplete data, credit card information, and geolocation based on the victim’s IP address.
RedLine Stealer has been incorporated into their attack chains by multiple threat actors over the years, making it a prevalent virus across North and South America, Europe, Asia, and Australia.
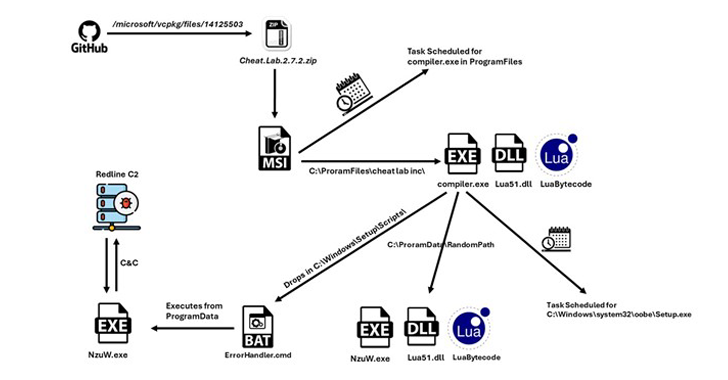
The infection sequence discovered by McAfee abused GitHub, using two of Microsoft’s official repositories for the C++ Standard Library (STL) and vcpkg, to host the malware-laden payload in the form of a ZIP archive.

It’s unclear how these archives were uploaded to the repository, but the technique suggests threat actors are exploiting the trust associated with trusted repositories to spread malware. ZIP files are no longer available for download from the Microsoft repository.
The ZIP files (“Cheat.Lab.2.7.2.zip” and “Cheater.Pro.1.6.0.zip”) are disguised as game cheats, indicating that gamers may be targeted by the campaign. It comes with an MSI installer designed to run malicious Lua bytecode.
Researchers Mohansundaram M. and Neil Tyagi said: “The advantage of this approach is that it can obfuscate malicious attacks and avoid the use of easily identifiable scripts such as wscript, JScript or PowerShell scripts, thereby enhancing the threat actor’s stealth and evasion capabilities.”
To deliver the malware to other systems, the MSI installer displays a message urging victims to share the program with friends to obtain an unlocked version of the software.
The “compiler.exe” executable in the installer uses a scheduled task to set persistence on the host and delete the CMD file when executing the Lua bytecode embedded in the “readme.txt” file in the ZIP file. In turn, run “compiler.exe” under another name “NzUw.exe”.
In the final stage, “NzUw.exe” initiates communication via HTTP with a command and control (C2) server at the above IP address belonging to RedLine.
The malware functions more like a backdoor, performing tasks obtained from the C2 server (for example, taking screenshots) and leaking the results back to the server.
The exact method of distributing links to ZIP files is currently unclear. Earlier this month, Checkmarx revealed how threat actors exploited GitHub’s search capabilities to trick unsuspecting users into downloading malware-filled repositories.
The development comes as Recorded Future details a “large-scale Russian-language cybercrime operation” that specifically targeted the gaming community and used fake Web3 gaming lures to spread malware capable of stealing sensitive information from macOS and Windows users. This technique is called trap phishing.
Insikt Group said: “The activity involved the creation of imitation Web3 gaming projects, with slight modifications to the name and branding to appear legitimate, and the use of fake social media accounts to enhance their authenticity.”

“These projects’ main web pages offer downloads that, once installed, infect devices with various types of ‘infostealer’ malware, such as Atomic macOS Stealer (AMOS), Stealc, Rhadamanthys or RisePro, depending on the operating system.”
It also saw a wave of malware activity targeting enterprise environments, including loaders such as PikaBot and a new virus called NewBot Loader.
“The attackers demonstrated multiple techniques and infection vectors in each campaign designed to deliver PikaBot payloads,” McPhee said.
These include phishing attacks that exploit email conversation hijacking and a Microsoft Outlook flaw called MonikerLink (CVE-2024-21413), which lures victims into downloading malware from an SMB share.
1 Comment
I don’t think the title of your article matches the content lol. Just kidding, mainly because I had some doubts after reading the article.