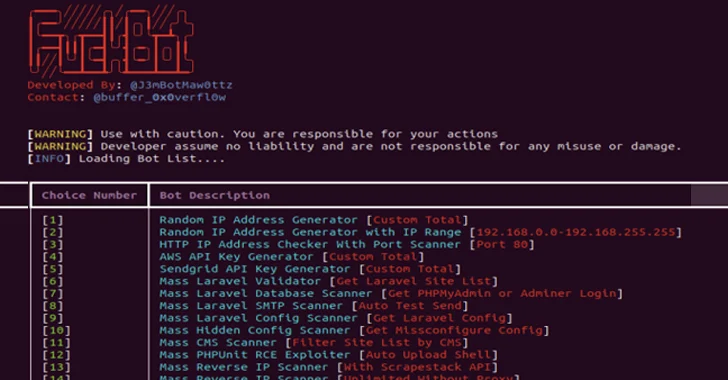
A new Python-based hacking tool called Forbot Attacks have been discovered targeting web servers, cloud services, content management systems (CMS), and SaaS platforms such as Amazon Web Services (AWS), Microsoft 365, PayPal, Sendgrid, and Twilio.
“Key capabilities include gathering credentials for spam attacks, AWS account hijacking tools, and the ability to target PayPal and various SaaS accounts,” SentinelOne security researcher Alex Delamotte said in a report shared with The Hacker News.
FBot is the latest addition to a long list of cloud hacking tools including AlienFox, GreenBot (also known as Mainance), Legion and Predator, the latter four of which have code-level overlap with AndroxGh0st.
SentinelOne describes FBot as “related to but distinct from these families” as it does not reference any source code from AndroxGh0st, although it shows similarities to Legion, which was first exposed last year.

The ultimate goal of this tool is to hijack cloud, SaaS and web services and obtain credentials to gain initial access and profit from selling access to other actors.
In addition to generating API keys for AWS and Sendgrid, FBot includes various features to generate random IP addresses, perform reverse IP scanners, and even verify PayPal accounts and the email addresses associated with those accounts.
“The script makes a Paypal API request through the hxxps://www.robertkalinkin.com/index.php website, which is a retail website for a Lithuanian fashion designer,” Delamotte noted. “Interestingly, all identified FBot samples use this website to authenticate Paypal API requests, as do some Legion Stealer samples.”
Most importantly, FBot includes AWS-specific functionality to examine AWS Simple Email Service (SES) email configuration details and determine EC2 service quotas for the target account. Likewise, Twilio related features are used to collect details about the account, namely the balance, currency, and phone number associated with the account.
The capabilities don’t stop there, as the malware is also able to extract credentials from Laravel environment files.

The cybersecurity company said it discovered samples from July 2022 to this month, suggesting it is being actively used. That said, it’s unclear whether the tool is actively maintained and how it can be distributed to other players.
“We found indications that FBot is the product of private development efforts, so contemporary builds may be distributed through smaller-scale operations,” De La Motte said.
“This is consistent with the theme of cloud-based attack tools being ‘private bots’ tailored for individual buyers, a theme prevalent in AlienFox builds.”