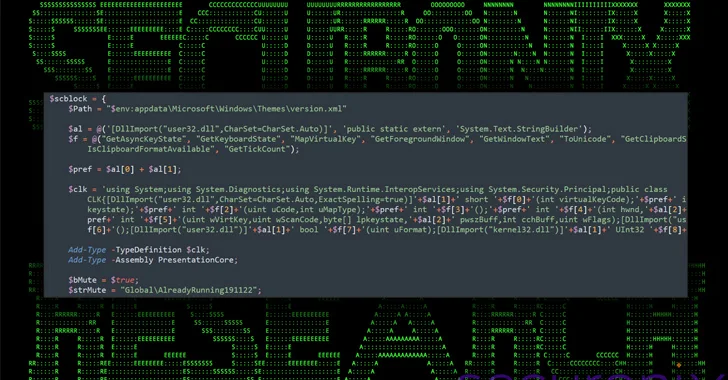
We have observed a new, well-designed attack campaign that utilizes PowerShell and VBScript malware to infect Windows systems and obtain sensitive information.
Cybersecurity firm Securonix dubbed the campaign “DEEP#GOSU,” saying it may be linked to a North Korean state-backed group called Kimsuky.
“Malware payload used Deep #GOSU In a technical analysis shared with The Hacker News, security researchers Den Iuzvyk, Tim Peck and Oleg Kolesnikov said: “It represents a sophisticated, multi-stage threat designed to operate covertly on Windows systems, especially from the web. From a surveillance perspective.”
“Its capabilities include keylogging, clipboard monitoring, dynamic payload execution and data exfiltration, as well as full remote access using RAT software, scheduled tasks, and persistence using jobs to automate the execution of PowerShell scripts.”
One noteworthy aspect of the infection process is that it utilizes legitimate services such as Dropbox or Google Docs for command and control (C2), allowing threat actors to blend into regular network traffic undetected.
Most importantly, using such cloud services to staging payloads can update malware functionality or provide additional mods.
The starting point is said to be a malicious email attachment containing a ZIP archive containing a malicious shortcut archive (.LNK) disguised as a PDF file (“IMG_20240214_0001.pdf.lnk”).
The .LNK file embeds a PowerShell script that also has access to actor-controlled Dropbox infrastructure to retrieve and execute another PowerShell script (“ps.bin”), as well as a decoy PDF document.

The second stage of the PowerShell script obtains a new file (“r_enc.bin”) from Dropbox, which is a .NET component file in binary form. It is actually an open source remote called TruRat (also known as TutRat or C#) Access Trojan (RAT) has the ability to log keystrokes, manage files and facilitate remote control.
Notably, Kimsuky used TruRat in at least two campaigns discovered by the AhnLab Security Intelligence Center (ASEC) last year.
The PowerShell script was also retrieved from Dropbox into a VBScript (“info_sc.txt”), which was designed to execute any VBScript code retrieved from the cloud storage service, including the PowerShell script (“w568232.ps12x”).
VBScript is also designed to use Windows Management Instrumentation (WMI) to execute commands on the system and to set scheduled tasks on the system for persistence.
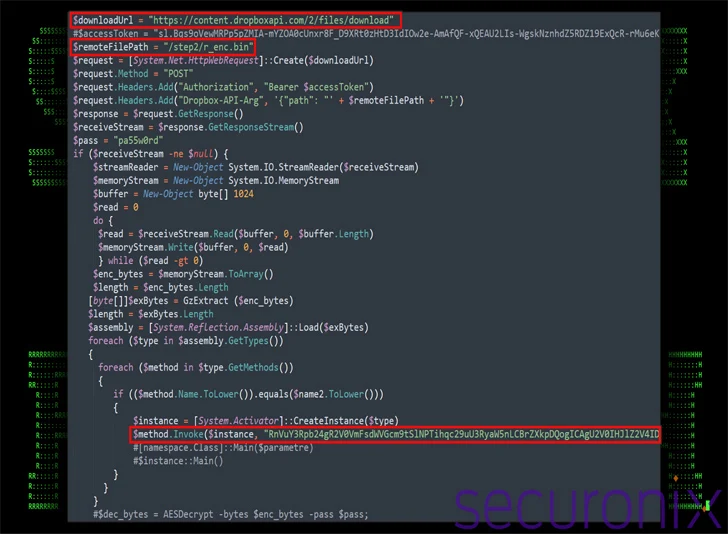
Another noteworthy aspect of VBScript is the use of Google Docs to dynamically retrieve configuration data for a Dropbox connection, allowing threat actors to change account information without changing the script itself.
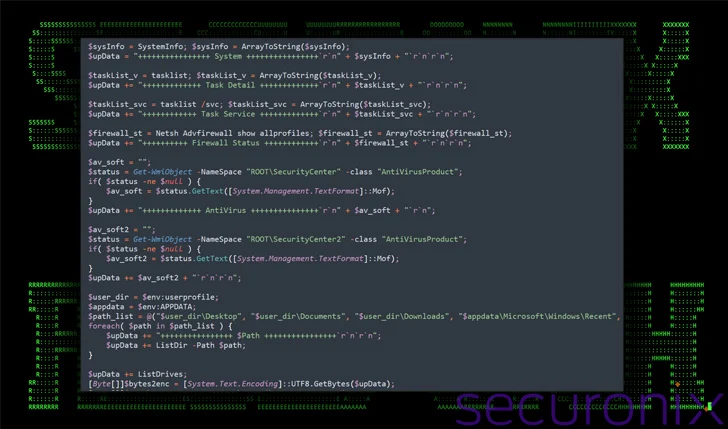
The downloaded PowerShell script can collect extensive information about the system and exfiltrate the details by making a POST request to Dropbox.
“The purpose of the script appears to be as a tool for regular communication with a command and control (C2) server via Dropbox,” the researchers said. “Its main purposes include encrypting, stealing or downloading data.”
In other words, it acts as a backdoor to take control of the infected host and continuously logs user activity, including keystrokes, clipboard contents, and foreground windows.
Security researcher Ovi Liber detailed how North Korea-linked ScarCruft embeds malicious code in Korean Word Processor (HWP) bait files in phishing emails to deliver malware such as RokRAT.
“The email contained an HWP document with embedded OLE objects in the form of a BAT script,” Liber said. “Once the user clicks on the OLE object, the BAT script executes, creating a PowerShell-based reflected DLL injection attack on the victim’s computer.”
It also leverages a legitimate remote desktop solution called MeshAgent to install malware such as AndarLoader and ModeLoader, a JavaScript malware designed to execute commands.
“This is the first confirmed use of MeshAgent by the Andariel Group,” ASEC said. “Andariel Group has continued to abuse domestic companies’ asset management solutions to spread malware during lateral movement, starting with the Innorix Agent in the past.”

Andariel, also known as Nicket Hyatt or Silent Chollima, is a sub-cluster of the notorious Lazarus Group that actively orchestrates cyber espionage and attacks for financial gain.
The prolific state-sponsored threat actor has since been observed using Tornado Cash to launder a large amount of crypto assets stolen by hackers from cryptocurrency exchange HTX and its cross-chain bridge, also known as the HECO Bridge. The leak resulted in the theft of $112.5 million worth of cryptocurrency in November 2023.
“Following common cryptocurrency laundering patterns, the stolen tokens were immediately exchanged for ETH via decentralized exchanges,” Elliptic said. “The stolen funds then lay dormant until March 13, 2024, when the stolen crypto assets began Send via Tornado Cash.”
The blockchain analytics firm said Tornado Cash continues to operate despite sanctions, which could make it an attractive proposition for Lazarus Group to conceal its trading trajectory after Sinbad shuts down in November 2023.
“The mixer operates via smart contracts running on a decentralized blockchain, so it cannot be seized and shut down like centralized mixers like Sinbad.io,” it states.