
Cybersecurity researchers have discovered newer variants of stealers and malware loaders known as rabbit loader Modularize its various functions and enable it to evade detection.
“BunnyLoader is dynamically developing malware capable of stealing information, credentials, and cryptocurrency, as well as delivering additional malware to victims,” Palo Alto Networks Unit 42 said in a report released last week.
The new version, called BunnyLoader 3.0 and released on February 11, 2024 by a developer named Player (or Player_Bunny), rewrites the data-stealing mod, reduces the payload size, and enhances keylogging capabilities.
BunnyLoader was first documented in September 2023 by Zscaler ThreatLabz, which described it as malware-as-a-service (MaaS) designed to collect credentials and facilitate cryptocurrency theft. It is initially available as a subscription price of $250 per month.

Since then, the malware has undergone frequent updates designed to evade anti-virus defenses and expand its data collection capabilities, with BunnyLoader 2.0 released at the end of the same month.
The third generation of BunnyLoader goes a step further, not only incorporating new Denial of Service (DoS) capabilities to launch HTTP flood attacks against target URLs, but also splitting its stealer, clipper, keylogger, and DoS modules into two separate carry file.
“BunnyLoader operators can choose to deploy these modules or use BunnyLoader’s built-in commands to load malware of their choice,” Unit 42 explains.
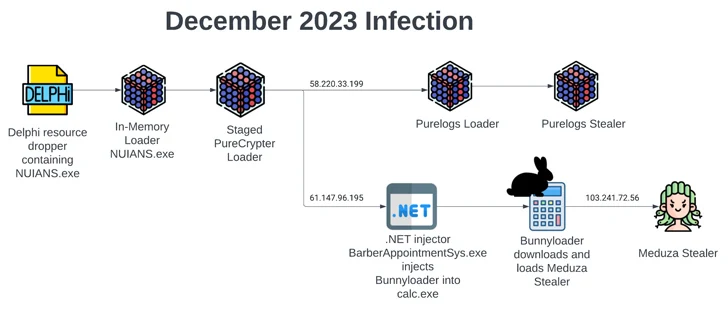
The infection chain delivering BunnyLoader has also become increasingly sophisticated, utilizing a previously undocumented dropper to load PureCrypter and then forking into two separate branches.
While one branch launches the PureLogs loader to ultimately deliver the PureLogs stealer, a second attack sequence drops the BunnyLoader to distribute another stealer malware called Meduza.
“BunnyLoader’s continued evolution in the ever-changing MaaS landscape demonstrates the need for threat actors to frequently retool to evade detection,” Unit 42 researchers said.
This development comes as a Russian cybercriminal suspect known as UAC-006 continues to use SmokeLoader malware (also known as Dofoil or Sharik) to target Ukrainian government and financial entities. It is understood to have been active since 2011.
According to a detailed report published by Ukraine’s State Cyber Protection Center (SCPC), as many as 23 phishing attacks sending SmokeLoader were recorded between May and November 2023.

“SmokeLoader, primarily a loader with additional information-stealing capabilities, has been linked to Russian cybercriminal activity and can be easily found on Russian cybercrime forums,” Unit 42 said.
Added to BunnyLoader and SmokeLoader is a new information-stealing malware codenamed GlorySprout, which is developed in C++ and costs $300 for lifetime access. According to RussianPanda, Stealers are clones of the Taurus Stealers.
“One notable difference is that, unlike Taurus Stealer, GlorySprout does not download additional DLL dependencies from the C2 server,” the researchers said. “In addition, GlorySprout lacks the Anti-VM functionality present in Taurus Stealer.”
