
Brazilian users targeted by so-called “neobanking trojan” chav cloak It is spread via phishing emails with PDF attachments.
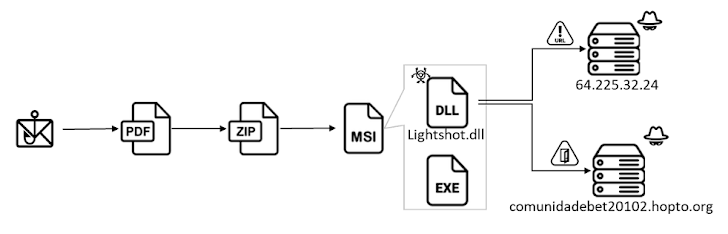
“This sophisticated attack involves PDF downloading a ZIP file and then utilizing DLL sideloading techniques to execute the final malware,” said Cara Lin, a researcher at Fortinet FortiGuard Labs.
The attack chain involves using a contract-themed DocuSign lure to trick users into opening a PDF file that contains buttons for reading and signing the document.
In fact, clicking the button will cause the installer file to be retrieved from a remote link shortened using the Goo.su URL shortening service.
There is an executable file named “Lightshot.exe” in the installer, which uses DLL sideloading to load “Lightshot.dll”, a CHAVECLOAK malware that helps steal sensitive information.
This includes collecting system metadata and performing checks to determine if the infected computer is located in Brazil, and if so, periodically monitoring the front window to compare it to a predefined list of bank-related strings.

If there is a match, a connection is made to the command and control (C2) server and the information continues to be collected and exfiltrated to different endpoints on the server (depending on the financial institution).
“The malware facilitated various actions to steal victims’ credentials, such as allowing the operator to block the victim’s screen, log keystrokes, and display deceptive pop-ups,” Lin said.
“The malware actively monitors victims’ access to specific financial portals, including multiple banks and Mercado Bitcoin, which includes traditional banks and cryptocurrency platforms.”
Fortinet said it also discovered a Delphi variant of CHAVECLOAK, once again highlighting the prevalence of Delphi-based malware targeting Latin America.
“The emergence of the CHAVECLOAK banking Trojan highlights the changing landscape of cyber threats targeting the financial sector, particularly Brazilian users,” Lin concluded.
The findings come amid an ongoing mobile banking fraud campaign targeting the UK, Spain and Italy that requires the use of SMS and voice phishing (i.e. SMS and voice phishing) tactics to deploy Android malware called Copybara , with the purpose of making an unauthorized bank transfer to a certain bank. A network of bank accounts run by money mules.
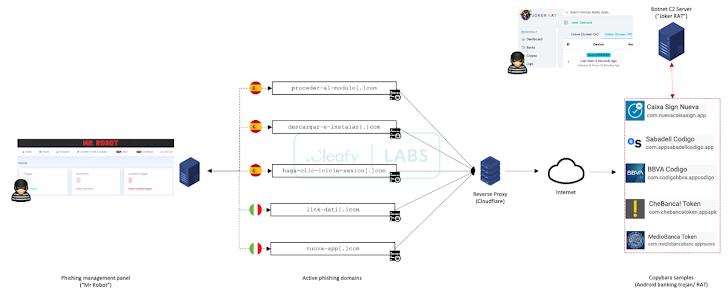
“them [Threat actors] A structured approach was found to be used to manage all ongoing phishing campaigns through a centralized web panel named “Mr.” Robots,” Cliffie said in a report published last week.
“Through this panel, TAs can enable and manage multiple phishing campaigns (targeting different financial institutions) based on their needs.”
The C2 framework also allows attackers to conduct customized attacks against different financial institutions using phishing kits designed to mimic the target entity’s user interface, while also employing anti-detection through geofencing and device fingerprinting. Method to limit connections from mobile devices only.
This phishing kit acted as a fake login page, capturing retail banking customer credentials and phone numbers, and sending the details to a Telegram group.
Some of the malicious infrastructure used by this campaign is designed to spread Copybara, which is managed using a C2 panel called JOKER RAT, which displays all infected devices and their geographical distribution on a live map.
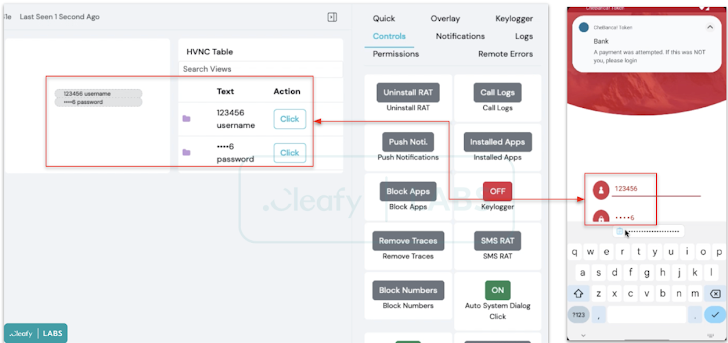
它還允許威脅行為者使用VNC 模組與受感染的設備進行遠端即時交互,此外還可以在銀行應用程式頂部注入虛假覆蓋層以竊取憑證、透過濫用Android 的輔助服務來記錄擊鍵以及攔截SMS message.

Most importantly, JOKER RAT comes with an APK builder that allows you to customize the rogue application’s name, package name, and icon.
“Another feature available within the panel is ‘Push Notifications’, which may be used to send fake push notifications to infected devices that look like bank notifications to trick users into opening the bank’s app, thus allowing the malware to Credentials can be stolen,” said Cleafy researchers Francesco Iubatti and Federico Valentini.
The growing sophistication of on-device fraud (ODF) schemes is further demonstrated by the recently revealed TeaBot (also known as Anatsa) campaign, which successfully infiltrated the Google Play Store under the guise of a PDF reader app.
“The application acts as an implant that facilitates the download of the TeaBot family of banking Trojans through multiple stages,” Iubatti said. “Before downloading the banking Trojan, the implant performs advanced evasion techniques, including obfuscation and file deletion, while also targeting Victimized countries conduct multiple inspections.”
