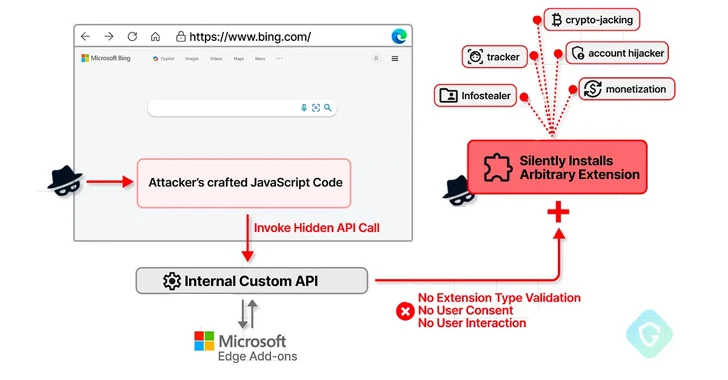
A now-patched security vulnerability in the Microsoft Edge web browser could be abused to install arbitrary extensions on a user’s system and perform malicious actions.
In a new report shared with The Hacker, Guardio Labs security researcher Oleg Zaytsev said: “This flaw could allow an attacker to exploit a private API originally used for marketing purposes to secretly install other devices with broad permissions without the user’s knowledge. Browser extension.” message.
The issue is tracked as CVE-2024-21388 (CVSS score: 6.5) and was addressed by Microsoft in Edge stable version 121.0.2277.83 released on January 25, 2024, following responsible disclosure in November 2023. The Windows maker credits Zaytsev and Jun Kokatsu for reporting the problem.
“An attacker who successfully exploited this vulnerability could gain the necessary permissions to install the extension,” Microsoft said in an advisory for the flaw, adding that it “could lead to a browser sandbox escape.”

The tech giant described it as a privilege escalation flaw, also stressing that successful exploitation requires the attacker to “take additional actions to prepare the target environment before exploiting the vulnerability.”
CVE-2024-21388 allows bad actors to execute JavaScript on Bing, according to Guardio’s findings[.]com or microsoft[.]com page to install any extension from the Edge Add-ons store without user consent or interaction.
This is because the browser has privileged access to certain private APIs, making it possible to install add-ons from the vendor’s own extension market.
One such API in the Chromium-based Edge browser is edgeMarketingPagePrivate, which can be accessed from a set of whitelisted websites belonging to Microsoft, including bing[.]com, microsoft[.]com, microsoftedgewelcome.microsoft[.]com and microsoftedgetips.microsoft[.]com etc.
The API also contains a method called installTheme(), which, as the name suggests, is designed to install a theme from the Edge Add-ons store by passing a unique theme identifier (“themeId”) and its manifest file as input.

The bug discovered by Guardio is essentially a case of insufficient validation, allowing an attacker to provide any extension identifier (instead of a themeId) from the storefront and install it covertly.
“As an added bonus, since this extension is not installed exactly as it was originally designed, it does not require any interaction or consent from the user,” Zaitsev explained.

In a hypothetical attack scenario exploiting CVE-2024-21388, a threat actor could publish a seemingly innocuous extension to an add-on store and use it to inject a piece of malicious JavaScript code into bing[.]com – or any website that allows access to the API – and install any extensions of their choice by calling the API with the extension identifier.
In other words, run a specially crafted extension on the Edge browser and access bing[.]com will automatically install the targeted extension without the victim’s permission.
Guardio told The Hacker News that while there is no evidence that the vulnerability is being exploited in the wild, it highlights the need to balance user convenience and security, and how browser customization can inadvertently break security mechanisms and introduce several new attack vector.
“It is relatively easy for an attacker to trick a user into installing a seemingly innocuous extension, without realizing that this is the first step in a more complex attack,” Zaitsev said. “The vulnerability can be exploited to facilitate the installation of additional extensions, Thereby possible monetary gain.”