The cryptojacking group is called Jinxin It has demonstrated its ability to evolve and adapt, proving to be a persistent threat by rapidly incorporating newly revealed vulnerabilities to exploit its arsenal and expand its botnet.
The findings come from cloud security company Aqua, which describes the threat actors as actively orchestrating illegal cryptocurrency mining operations since 2019.
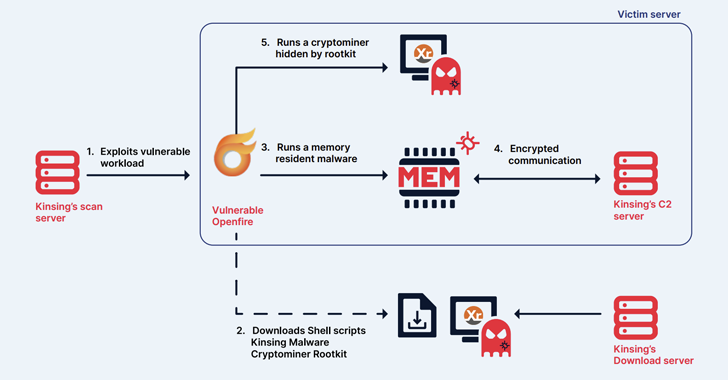
Kinsing (aka H2Miner) is the name of the malware and the adversary behind it, which continues to expand its toolkit with new vulnerabilities to register infected systems into cryptocurrency mining botnets. TrustedSec first documented it in January 2020.
In recent years, campaigns involving Golang-based malware have exploited various flaws in Apache ActiveMQ, Apache Log4j, Apache NiFi, Atlassian Confluence, Citrix, Liferay Portal, Linux, Openfire, Oracle WebLogic Server, and SaltStack to compromise vulnerable system.

Other methods involve leveraging misconfigured Docker, PostgreSQL, and Redis instances to gain initial access and then marshalling the endpoints into a botnet for cryptomining, but not before deactivating security services and removing installed files on the host. Rival miners.
Subsequent analysis by CyberArk in 2021 found commonalities between Kinsing and another malware called NSPPS, concluding that the two viruses “represent the same family.”
Kinsing’s attack infrastructure is divided into three main categories: initial servers used to scan and exploit vulnerabilities, download servers responsible for staging payloads and scripts, and command and control (C2) servers that maintain contact with infected servers. device.
The IP address used for the C2 server resolved to Russia, while the IP addresses used to download scripts and binaries spanned countries such as Luxembourg, Russia, the Netherlands, and Ukraine.
“Kinsing uses different tools for different operating systems,” Aqua said. “For example, Kinsing often uses shell and Bash scripts to exploit Linux servers.”
“We also found Kinsing using PowerShell scripts to target Openfire on Windows servers. When running on Unix, it typically downloads binaries that run on x86 or ARM.”
Another noteworthy aspect of the threat actor’s activity is that 91% of targeted applications were open source, with the group primarily targeting runtime applications (67%), databases (9%), and cloud infrastructure (8).
 |
| Image source: Forescout |
Extensive analysis of the artifacts further revealed three distinct categories of procedures –
- Type I and Type II scriptsDeployed after initial access, it is used to download the next stage of attack components to eliminate competition and circumvent defenses by turning off firewalls, terminating security tools such as SELinux, AppArmor, and Alibaba Cloud Aegis, and deploying rootkits to hide malicious processes.
- helper scriptIt aims to achieve initial access by exploiting vulnerabilities, disable specific security components related to Alibaba Cloud and Tencent Cloud services from the Linux system, open a reverse shell of the server under the attacker’s control, and facilitate the retrieval of miner load
- binary fileas a second-stage payload, including the core Kinsing malware and a cryptominer that mines Monero
For its part, the malware is designed to keep an eye on the mining process and share its process identifier (PID) with the C2 server, perform connection checks and send execution results, etc.

“Kinsing targets Linux and Windows systems, often by exploiting vulnerabilities in web applications or misconfigurations such as the Docker API and Kubernetes to run cryptocurrency mining programs,” Aqua said. “To prevent potential threats like Kinsing , proactive measures such as strengthening pre-deployment workloads are critical.”
The disclosure comes as botnet malware families are increasingly looking for ways to expand their reach and recruit machines into networks to carry out malicious activities.
The best example is P2PInfect, a Rust malware that was found to exploit less secure Redis servers to deliver variants compiled for the MIPS and ARM architectures.
Nozomi Networks, which discovered the sample targeting ARM earlier this year, said: “The main payload is capable of performing various operations, including propagating and delivering other modules with self-explanatory file names such as miner and winminer.”
“As the name suggests, the malware is capable of performing peer-to-peer (P2P) communications without relying on a single command and control server (C&C) to deliver the attacker’s commands.”