Until earlier this week, the network equipment provider’s support site Juniper Networks Potentially sensitive information related to customer products was exposed, including the exact device purchased by each customer, as well as the warranty status, service contract and serial number of each product. Juniper Networks said it has resolved the issue and that the inadvertent data leakage resulted from a recent upgrade to its support portal.

Juniper Networks, headquartered in Sunnyvale, Calif., makes high-performance network routers and switches, and its products are used by some of the world’s largest organizations. Earlier this week, KrebsOnSecurity heard from a reader who manages multiple Juniper devices and discovered that he could use Juniper’s customer support portal to find other Juniper customers’ devices and Support contract information.
Logan George I am a 17-year-old intern working at an organization that uses Juniper products. George, who declined to give the name of his employer, said he stumbled across the data breach earlier this week while searching for support information for a specific Juniper product.
George discovered that after logging in with a regular customer account, Juniper’s support site allowed him to list details about nearly all Juniper devices purchased by other customers.Search in amazon.com For example, in the Juniper Networks portal, tens of thousands of records are returned. Each record includes the model and serial number of the device, the approximate installation location of the device, as well as the status of the device and related support contract information.
George said that after a few minutes of digging around on the Juniper Support Portal, he discovered that he could even see product and support information for the product. U.S. Department of Defense (Department of Defense).
“If there’s one thing I know, it’s that I shouldn’t be seeing Juniper products from the Department of Defense,” George said. “But hundreds of companies have access to this information, and I can see what products they have installed and where.”
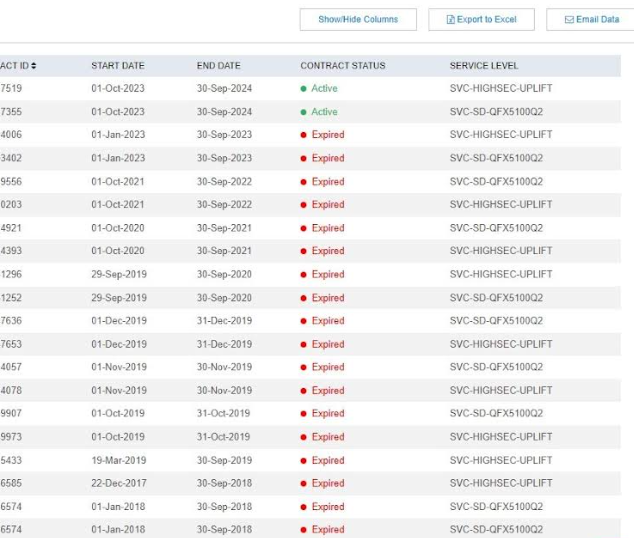
Juniper supports information published by portals. Fields not shown include serial number, software support reference number, product, warranty expiration date, and contract ID.
George said the exposed support contract information could be sensitive because it shows which Juniper products are most likely to lack critical security updates.
“If you don’t have a support contract, you can’t get updates, it’s that simple,” George said. “Using the serial number, I can see which products are not covered by the support contract. I can then narrow down where each device is sent through the serial number tracking system and potentially see everything sent to the same location. Many companies don’t update very often. Their switches, understanding what they are used for can give people an idea of possible attack vectors.”
Juniper said in a written statement that the data breach was the result of a recent upgrade to its support portal.
“We became aware of an inadvertent issue that allowed registered users of our systems to access serial numbers unrelated to their accounts,” the statement read. “We acted quickly to resolve the issue and currently have no reason to believe that any identifiable or individual customers The data was exposed in any way. We take these issues seriously and always use these experiences to prevent similar incidents from happening again. We are actively working to determine the root cause of this flaw and thank the researchers who brought this to our attention.”
The company has not yet responded to a request for precise information on when these overly lenient user rights will be introduced. However, the changes may date back to September 2023, when Juniper announced a rebuild of its customer support portal.
George told KrebsOnSecurity that the backend for the Juniper support site appears to be run by sales force, and Juniper Networks may not have created the appropriate user permissions on its Salesforce assets. In April 2023, KrebsOnSecurity released research showing that a wide range of organizations, including banks, healthcare providers, and state and local governments, are exfiltrating private and sensitive data due to misconfigured Salesforce installations.
Nicholas WeaverThe complexity of modern technical support portals leaves a lot of room for error, said a researcher at the International Computer Science Institute (ICSI) at the University of California, Berkeley, and a lecturer at the University of California, Davis.
“This is a reminder of how difficult it is to build a large system like a support portal, where you need to be able to manage countless users with different access roles,” Weaver said. “One small mistake can have hilarious consequences.”
Last month, computer manufacturers Hewlett Packard Enterprise announced that it will acquire Juniper Networks for $14 billion, reportedly to help enhance the 100-year-old technology company’s artificial intelligence products.
