
印度政府實體和能源公司已成為未知威脅行為者的目標,目的是提供名為HackBrowserData 的開源資訊竊取惡意軟體的修改版本,並在某些情況下透過使用Slack 作為命令和控制(C2) 來竊取敏感information.
“The information stealers were sent via phishing emails disguised as invitations from the Indian Air Force,” EclecticIQ researcher Arda Büyükkaya said in a report released today.
“The attackers used Slack channels as an exfiltration point to upload confidential internal documents, private emails and cached web browser data after the malware was executed.”
The Dutch cybersecurity company began observing the campaign on March 7, 2024, codenamed “Operation FlightNight” in reference to the Slack channel operated by the adversary.

The malicious campaign targeted multiple government entities in India, including those related to electronic communications, IT governance, and defence.
Threat actors are said to have successfully compromised private energy companies to obtain financial documents, personal details of employees and details about oil and gas drilling activities. A total of approximately 8.81 GB of data was leaked during the campaign.
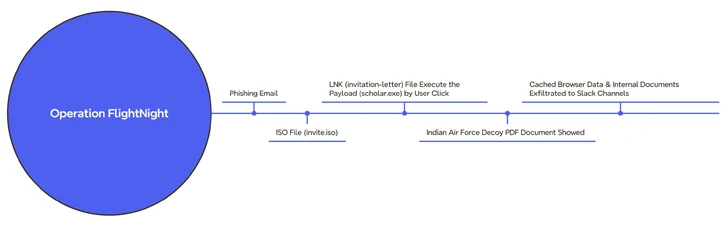
The attack chain begins with a phishing message containing an ISO file (“invite.iso”), which in turn contains a Windows shortcut (LNK) that triggers the execution of a hidden binary file present in the file (“scholar.iso”). exe”). Mounted disc image.
At the same time, the victim is shown a decoy PDF file claiming to be an invitation letter from the Indian Air Force, while the malware secretly collects the file and cached web browser data and transmits it to an attacker-controlled Slack channel called FlightNight. .
The malware is a modified version of HackBrowserData that goes beyond browser data stealing to include siphoning files (Microsoft Office, PDF and SQL database files), communicating through Slack, and using obfuscation techniques to better evade detection. Function.

The threat actor is suspected of stealing decoy PDFs in previous intrusions, with behavioral similarities traced to phishing campaigns targeting the Indian Air Force using a Go-based stealer called GoStealer.
Details of the campaign were disclosed by an Indian security researcher who goes by the alias xelemental (@ElementalX2) in mid-January 2024.
The GoStealer infection sequence is actually identical to FlightNight, using a procurement-themed lure (“SU-30 Aircraft Procurement.iso”) to display the lure file, while deploying a stealer payload to steal information of interest via Slack.
By adopting freely available attack tools and repurposing legitimate infrastructure like Slack that is ubiquitous in enterprise environments, it allows threat actors to reduce time and development costs and fly under the radar with ease.
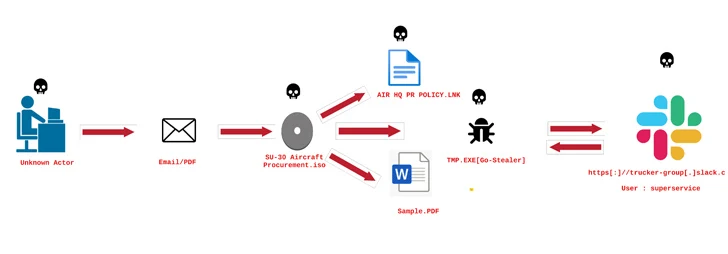 |
| Image source: ElementalX2 |
Efficiency advantages also mean it becomes easier to launch targeted attacks, allowing even less skilled and aspiring cybercriminals to take action and cause significant damage to organizations.
“Operation FlightNight and the GoStealer campaign highlight a simple yet effective way for threat actors to use open source tools to conduct cyber espionage,” Büyükkaya said.
“This highlights the evolving landscape of cyber threats, with attackers abusing widely available open source attack tools and platforms to achieve their goals with minimal detection and investment risk.”
