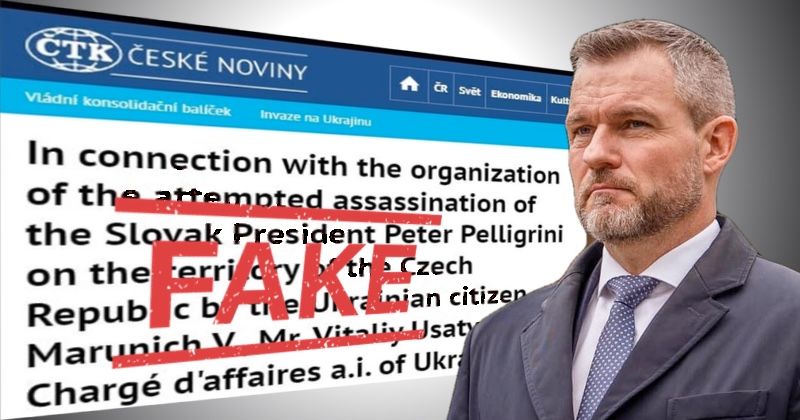
Czech news agency ČTK announced on Tuesday that a hacker had successfully broken into its systems and published a fake news report about a plot to murder the president of a neighboring country.
One of the false stories published by the hackers in Czech and English claimed that the Czech Security Information Service (BIS) prevented an assassination attempt against the new Slovak president Peter Pelligrini.
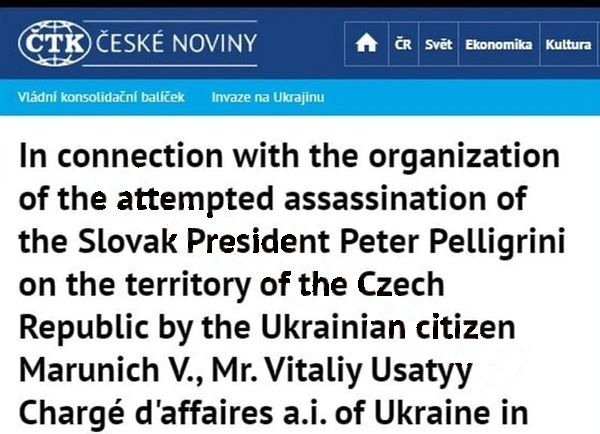
According to false reports fabricated by hackers, the plot against the life of the Slovak president was orchestrated by Ukraine’s charge d’affaires Vitaly Usati and others.
Subsequent fake news reports published by the hackers on the ČTK website and mobile app claimed that Czech Foreign Minister Jan Lipavský had commented on the alleged murder plot.
Hackers’ haste to publish fake news results in careless mistakes that make readers aware of its lack of factual basis.
For example, the surname of the President of Slovakia is called “Pellegrini” instead of the correct Pellegrini.
Suspicions are likely to point to the attack as a deliberate disinformation effort by pro-Kremlin hackers to discredit Ukraine as it continues its fight against Russian invaders.
Last year, security researchers described how a hacker group called “Ghostwriter” affiliated with the Belarusian government accessed media organizations’ content management systems to publish false stories.
ČTK News Agency issued a statement on its website confirming that news reports of the assassination plot were false, removed the false reports from its website and blocked hackers’ access to its content management system.
ČTK said it was working closely with Czech authorities to investigate the hack and would not provide any additional information at this time.
All businesses need to implement multiple layers of protection to prevent malicious hackers from gaining access to their IT systems. It is critical to tightly control access to internal infrastructure, such as a media organization’s content management services, and to verify the true identity of users.
Security breaches have repeatedly shown that simply requiring users to choose strong, unique passwords and be wary of phishing attacks may not be enough. Additional defenses such as two-factor authentication can help make system intrusion more challenging.