
Threat actors are exploiting digital file publishing (DDP) websites hosted on platforms such as FlipSnack, Issuu, Marq, Publuu, RelayTo and Simplebooklet for phishing, credential harvesting and session token theft, once again highlighting how threat actors are re- Utilizing legitimate services for malicious purposes.
“Hosting phishing lures on DDP sites increases the likelihood of a successful phishing attack because these sites typically have a good reputation, are less likely to appear on web filter block lists, and may appear familiar or familiar to others Users of these sites are instilled with a false sense of security. It’s legitimate,” Cisco Talos researcher Craig Jackson said last week.
While attackers have used popular cloud services such as Google Drive, OneDrive, Dropbox, SharePoint, DocuSign and Oneflow to host phishing documents in the past, this latest development marks an escalation aimed at evading email security controls.

The DDP service allows users to upload and share PDF files in a browser-based interactive flipbook format, adding page-turning animations and other skeuomorphic effects to any catalog, brochure or magazine.
We found that threat actors were abusing the free tiers or free trial periods offered by these services to create multiple accounts and publish malicious files.
In addition to exploiting its good domain reputation, the attackers also exploited the fact that the DDP website facilitates temporary file hosting, allowing published content to automatically become unavailable after a predefined expiration date and time.
In addition, built-in productivity features in DDP sites such as Publuu can act as a deterrent to prevent the extraction and detection of malicious links in phishing messages.
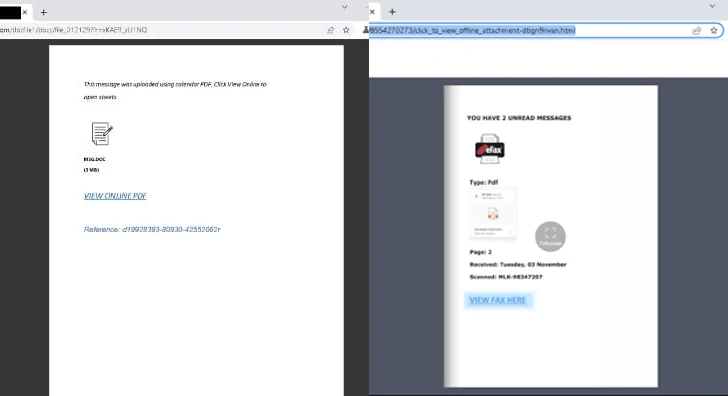
In the incidents analyzed by Cisco Talos, DDP websites were integrated into the attack chain at a secondary or intermediate stage, typically by embedding links in phishing emails to files hosted on legitimate DDP websites.
DDP-hosted files can serve as a gateway to external, adversary-controlled sites, either directly by clicking on links contained in the decoy file, or through a series of redirects (which also require solving a CAPTCHA to prevent automated analysis from working).

The final login page is a fake website that mimics the Microsoft 365 login page, allowing the attacker to steal credentials or session tokens.
“DDP sites can be a blind spot for defenders because trained users are unfamiliar with them and are less likely to be flagged by email and web content filtering controls,” Jackson said.
“DDP websites create an advantage for threat actors trying to thwart contemporary phishing protections. The same features and benefits that attract legitimate users to these websites can be abused by threat actors to increase the effectiveness of phishing attacks.”
