
An active Android malware campaign called eXotic Visit targets South Asian users, particularly those in India and Pakistan, with the malware being distributed through specialized websites and the Google Play Store.
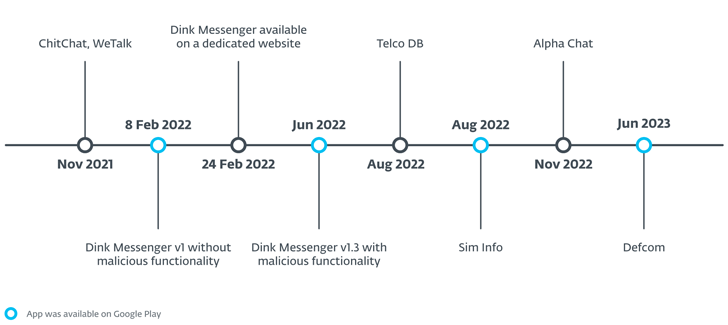
The Slovak cybersecurity company said that this activity has been ongoing since November 2021 and is not associated with any known threat actors or groups.It is tracking the group behind the operation virtual intruder.
“The downloaded application provides legitimate functionality, but also contains code from the open-source Android XploitSPY RAT,” ESET security researcher Lukáš Štefanko said in a technical report released today.
The campaign is said to be highly targeted, with the number of installs of the apps available on Google Play being minimal, ranging from 0 to 45. These apps have been removed.

These fake but useful apps mainly pretend to be messaging services such as Alpha Chat, ChitChat, Defcom, Dink Messenger, Signal Lite, TalkU, WeTalk, Wicker Messenger and Zaangi Chat. About 380 victims allegedly downloaded the apps and created accounts to use them to send messages.
eXotic Visit also uses apps like Sim Info and Telco DB, both of which claim to provide SIM card owner details by simply entering a Pakistani phone number. Other apps pretended to be a Pakistani food ordering service and a legitimate Indian hospital called Specialist Hospital (now renamed Trilife Hospital).
XploitSPY, uploaded As early as April 2020, a user named RaoMK, who is associated with an Indian cybersecurity solutions company called XploitWizer, posted this message on GitHub. It is also described as a fork of another open source Android Trojan called L3MON, which in turn draws inspiration from AhMyth.
It has extensive capabilities to collect sensitive data from infected devices such as GPS location, microphone recordings, contacts, SMS, call logs and scrapbook contents; extract notification details from apps like WhatsApp, Facebook, Instagram and Gmail Information; download and upload files; view installed applications; and queue commands.
On top of that, the malicious app is designed to take photos and enumerate files in multiple directories related to screenshots, WhatApp, WhatsApp Business, Telegram and unofficial WhatsApp mod (called GBWhatsApp).

“Over the years, these threat actors have added obfuscation, emulator detection, hiding [command-and-control] addresses as well as the use of local libraries,” Štefanko said.
The main purpose of the native library (“defcome-lib.so”) is to encode C2 server information and hide static analysis tools. If the emulator is detected, the application uses a fake C2 server to evade detection.
Some applications have been distributed through websites created specifically for this purpose (“chitchat.ngrok[.]io”), providing a link to the Android package file (“ChitChat.apk”) hosted on GitHub. It’s unclear how victims were directed to these apps.
“Distribution starts on dedicated websites and then even moves to the official Google Play store,” Štefanko concluded. “The purpose of this activity was espionage and may have targeted victims in Pakistan and India.”
