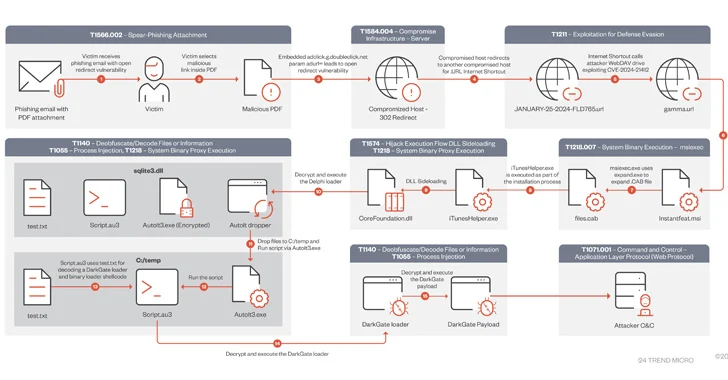
The DarkGate malware campaign observed in mid-January 2024 exploited a recently patched security vulnerability in Microsoft Windows as a zero-day vulnerability using a fake software installer.
“During this campaign, users were lured by a PDF containing a Google DoubleClick Digital Marketing (DDM) open redirect, which led unsuspecting victims to a compromised website hosting Microsoft Windows SmartScreen, bypassing CVE-2024-21412. Resulting in a malicious Microsoft (.MSI) installer,” Trend Micro said.
CVE-2024-21412 (CVSS score: 8.1) involves a network shortcut file security feature bypass vulnerability that allows an unauthenticated attacker to circumvent SmartScreen protection by convincing a victim to click on a specially crafted file.
Microsoft fixed the issue as part of the February 2024 Patch Tuesday update, but not before it was weaponized by a threat actor known as Water Hydra (aka DarkCasino) for use in targeting financial institutions. The DarkMe malware was spread during the attack.
New findings from Trend Micro indicate that the vulnerability is more widely exploited than previously thought, with the DarkGate campaign exploiting it in conjunction with open redirects from Google Ads to spread malware.

The complex attack chain begins when a victim clicks on a link embedded in a PDF attachment sent via a phishing email.This link deploys an open redirect from Google Double Click[.]net domain to a compromised web server hosting a malicious .URL Internet shortcut file that exploits CVE-2024-21412.
Specifically, open redirects are designed to distribute fake Microsoft software installers (.MSI) disguised as legitimate software, such as Apple iTunes, Notion, and NVIDIA. These installers come with sideloaded DLL files that can be decrypted and used by DarkGate (version 6.1.7).
Notably, over the past few months, threat actors have exploited another now-fixed bypass flaw in Windows SmartScreen (CVE-2023-36025, CVSS score: 8.8) to deliver DarkGate, Phemedrone Stealer, and Mispadu.
Abuse of Google Ads technology allows threat actors to increase the scope and scale of their attacks through different advertising campaigns tailored to specific audiences.
“Using fake software installers and open redirects is a potent combination that can lead to many infections,” said security researchers Peter Girnus, Aliakbar Zahravi and Simon Zuckerbraun. “Be vigilant and instruct users not to trust them through official channels. Any software installers received externally are critical.”
At the same time, the AhnLab Security Intelligence Center (ASEC) and eSentire revealed that fake installers for Adobe Reader, Notion, and Synaptics are being distributed through fake PDF files and legitimate-looking websites to deploy information-stealing programs such as LummaC2 and XRed backdoors.
It also discovered new stealer malware families such as Planet Stealer, Rage Stealer (a.k.a. xstealer) and Tweaks (also known as Tweakers), add to the plethora of cyber threats capable of obtaining sensitive information from infected hosts.
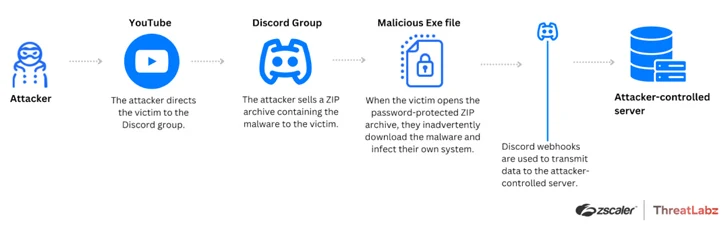
“Attackers are leveraging popular platforms such as YouTube and Discord to distribute Tweaks to Roblox users, leveraging the ability of legitimate platforms to evade detection by web filter blocklists that typically block known malicious servers,” Zscaler ThreatLabz said.
“Attackers share malicious files disguised as frame-per-second (FPS) optimization packages with users, who in turn infect their systems with Tweaks malware.”

PowerShell-based stealers can exfiltrate sensitive data, including user information, location, Wi-Fi profiles, passwords, Roblox IDs, and in-game currency details, to an attacker-controlled server via a Discord webhook.
It has been observed that malvertising and social engineering campaigns are also used as initial access vectors to spread various stealing programs and remote access Trojans, such as Agent Tesla, CyberGate RAT, Fenix botnet, Matanbuchus, NarniaRAT, Remcos RAT, Rhadamanthys, SapphireStealer and zgRAT.