In a world of ever-expanding terminology, adding another FLA (four-letter abbreviation) to your vocabulary may seem like the last thing you want to do. However, if you are looking for ways to continuously reduce risk across your environment while making significant and ongoing improvements to your security posture, we think you may want to consider establishing a Continuous Threat Exposure Management (CTEM) program.
CTEM is a cyber risk management approach that combines attack simulation, risk prioritization and remediation guidance in a coordinated process. The term “persistent threat exposure management” first appeared in the Gartner ® report “Implementing a Persistent Threat Exposure Management Program (CTEM)” (Gartner, July 21, 2022). Since then, we’ve seen organizations around the world see the benefits of this integrated, ongoing approach.

Webinar: Why and How to Adopt the CTEM Framework
XM Cyber is hosting a webinar on March 27th hosted by Gartner Vice President Analyst Pete Shoard on Adopting the CTEM Framework, and even if you can’t attend, we’ll share an on-demand link so don’t miss it!
Focus on areas of greatest risk
But why is CTEM so popular, and more importantly, how does it improve the already overcrowded world of vulnerability management?
At its core, CTEM is about uncovering real, actionable risks to critical assets. Anyone can identify security improvements in an organization’s environment. The problem is not in discovering risk exposures, but in being overwhelmed by them – and being able to know which risks pose the greatest risk to key assets.
We believe the CTEM program can help you:
- Identify your most exposed assets and how attackers might exploit them
- Understand the impact and likelihood of potential breaches
- Prioritize the most pressing risks and vulnerabilities
- Get actionable advice on how to fix these problems
- Continuously monitor your security posture and track your progress
Through the CTEM program you gain an “attacker’s perspective”, cross-referencing vulnerabilities in your environment and their likelihood of being exploited by an attacker. The result is a prioritized list of exposure issues to address, including issues that can be safely addressed later.
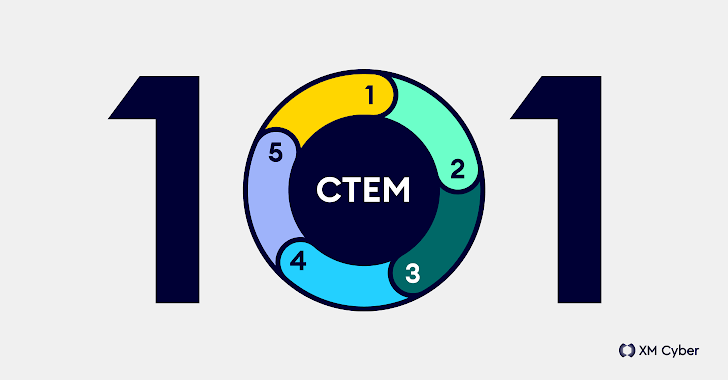
Five Phases of CTEM Programs

CTEM is not a specific product or service, but a plan to reduce cybersecurity risks through five phases:
- scoping – According to Gartner, “To define and subsequently refine the scope of a CTEM initiative, security teams first need to understand what is important to the business partner and what the impact may be (such as the need to disrupt production systems)” Severe enough to warrant Collaborative Remedies. ”
- Discover – Gartner says, “After scoping is complete, it is important to begin the process of discovering the assets and their risk profile. Discovery of business areas that have been identified by the scoping process should be prioritized, although this is not always the driver. Exposure discovery includes more than just vulnerabilities: it This may include misconfiguration of assets and security controls, as well as other vulnerabilities such as counterfeit assets or adverse reactions to phishing tests.”
- Priority – Gartner states that at this stage, “the goal of exposure management is not to try to fix every identified issue or the most common zero-day threat, but to identify and address the threats most likely to be exploited against the organization.” Gartner further states, “Organizations cannot handle the traditional way of prioritizing risks through predefined base severity scores because they need to consider vulnerability exploit prevalence, available controls, mitigation options, and business criticality to reflect the impact on risk. potential impact on the organization.
- verify – According to Gartner, this phase “is part of the process by which an organization verifies how a potential attacker could actually exploit the identified exposure and how monitoring systems might react.” Gartner also states that the goals of the verification step include verifying that an attacker can Leverage previously discovered and prioritized vulnerabilities to “evaluate possible attack successes.”
- mobilization – Gartner states, “To ensure success, security leaders must acknowledge and communicate to all stakeholders that remediation cannot be fully automated.” The report further states, “The goal of ‘mobilization’ efforts is to reduce the number of approvals, implementation processes, and Eases friction in deployment and ensures teams put CTEM results into action. It requires organizations to define communication standards (information requirements) and document cross-standard-team approval workflows.”
CTEM versus alternative methods
There are several alternative approaches to understanding and improving the security posture, some of which have been used for decades.
- Vulnerability Management/RBVM Focus on mitigating risk by identifying vulnerabilities through scanning, then prioritizing and fixing them based on static analysis. Automation is critical given the increasing number of assets that need to be analyzed and the number of vulnerabilities identified. However, RBVM is limited to identifying CVEs and cannot resolve identity issues and misconfigurations. Additionally, it does not have the information needed to properly prioritize fixes, often resulting in widespread backlogs.
- red team practice It is manual, expensive point-in-time testing of network security defenses. They try to determine whether a successful attack path existed at a specific point in time, but they cannot identify the full risk.
- Similarly, Penetration testing Use testing methods as a risk assessment and provide point-in-time results. Since it involves active interaction with networks and systems, it is often limited in terms of critical assets due to the risk of disruption.
- Cloud Security Posture Management (CSPM) Focus solely on misconfiguration issues and compliance risks in cloud environments. While important, it does not account for interactions between remote employees, on-premises assets, or multiple cloud providers. These solutions don’t understand the full path of attack risk across different environments—a common risk in the real world.
We believe that an approach based on the CTEM program has the following advantages:
- Cover all assets (cloud, on-premises, and remote) and understand which assets are most critical.
- Continuously discover all types of exposures – traditional CVE, identity and misconfiguration.
- Presenting real-world insights from the attacker’s perspective
- Prioritize repair efforts to eliminate paths with the fewest repairs
- Provide remediation recommendations to achieve reliable, repeatable improvements
The value of CTEM
We believe that CTEM methods have significant advantages over other methods, some of which have been used for decades. Essentially, organizations spend years identifying risks, adding them to never-ending “to-do” lists, and spend countless hours hunkering down on those lists with no discernible benefit. With CTEM, a more thoughtful approach to discovery and prioritization adds value through:
- Quickly reduce overall risk
- Increase the value of each fix and potentially free up resources
- Improve coordination between security and IT teams
- Provide a common perspective on the entire process, encourage a positive feedback loop, and drive continuous improvement
Getting Started with CTEM
Because CTEM is a process rather than a specific service or software solution, getting started is a holistic endeavor. Organizational support is a critical first step. Other considerations include:
- Use the right software components to support processes and data collection
- Define critical assets and update remediation workflows
- Perform proper system integration
- Determine appropriate execution reporting and security posture improvement methods
We believe that through CTEM programs, organizations can develop a common language of security and IT risk; and ensure that the level of risk for each exposure becomes clear. This allows the few that actually pose a risk out of the thousands of risks that exist to be addressed in a meaningful and measurable way.
For more information on how to get started with a CTEM program, check out XM Cyber’s white paper, XM Cyber Operations Gartner®’s Continuous Threat Exposure Management (CTEM) Framework.