Cybersecurity researchers further reveal a remote access Trojan (RAT) called Deuterbear used by China-linked Internet companies Montenegro The hacker group is part of a cyber espionage campaign targeting the Asia-Pacific region this year.
Trend Micro researchers Pierre Lee and Cyris Tseng said in a new analysis: “Deuterbear, while similar to Waterbear in many ways, has improved functionality, such as supporting shellcode plug-ins, avoiding RAT operation handshakes, and using HTTPS. C&C communications.
“Comparing the two malware variants, Deuterbear differs from Waterbear in that it uses a shellcode format, has anti-memory scanning, and shares traffic keys with its downloader.”
BlackTech has been active since at least 2007 and is also on the radar of the broader cybersecurity community, with names including Circuit Panda, Earth Hundun, HUAPI, Manga Taurus, Palmerworm, Red Djinn, and Temp.Overboard.
For nearly 15 years, the group’s orchestrated cyberattacks have involved the deployment of malware called Waterbear (also known as DBGPRINT), although campaigns observed since October 2022 have also used a newer version called Deuterbear.

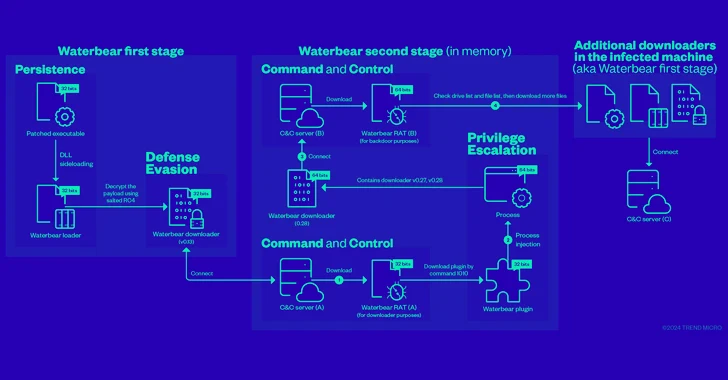
Waterbear is delivered via a patched, legitimate executable that utilizes DLL sideloading to launch a loader that then decrypts and executes a downloader that then contacts a command and control (C&C) server to retrieve the RAT module .
Interestingly, the RAT module was retrieved twice from attacker-controlled infrastructure. The first time was just to load the Waterbear plugin, which retrieved the RAT module from another C&C server by launching a different version of the Waterbear downloader. group to further harm.
In other words, the first Waterbear RAT acted as a plug-in downloader, while the second Waterbear RAT acted as a backdoor to obtain sensitive information from the infected host through a set of 60 commands.
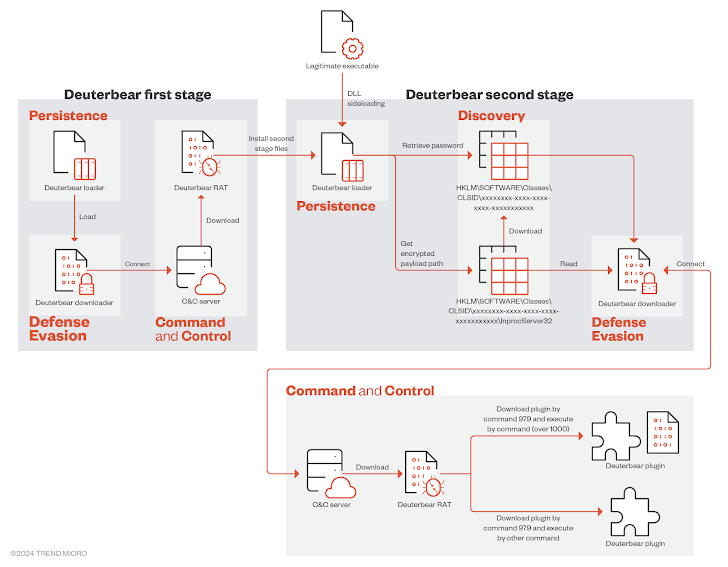
Deuterbear’s infection pathway is very similar to Waterbear’s, which also implements a two-stage installation of RAT backdoor components, but also undergoes a certain degree of adjustment.
In this case, the first stage uses a loader to initiate the downloader, which connects to the C&C server to obtain the Deuterbear RAT, an intermediary used to sideload the DLL via the second stage loader. Build persistence.
The loader is ultimately responsible for executing the downloader, which in turn downloads the Deuterbear RAT from the C&C server for information theft.
“On most infected systems, only the second-stage Deuterbear is available,” the researchers said. “After the ‘persistent installation’ is completed, all components of the first-stage Deuterbear are completely removed.”
“This tactic effectively protects their traces and prevents the malware from being easily analyzed by threat researchers, especially in simulated environments rather than real victim systems.”
Deuterbear RAT is also a more streamlined version of its predecessor, retaining only a subset of commands in favor of a plugin-based approach to incorporating more functionality.
“Waterbear has undergone continuous evolution, culminating in the emergence of a new malware called Deuterbear,” Trend Micro said. “Interestingly, both Waterbear and Deuterbear have continued to evolve independently, rather than simply replacing the other. ”
Targeted campaigns offer SugarGh0st RAT
The disclosure comes as Proofpoint details a “highly targeted” cyber campaign targeting U.S. organizations involved in artificial intelligence efforts, including academia, private industry, and government, to spread a malicious malware known as the SugarGh0st RAT. software.
The enterprise security company is tracking an emerging cluster of activity called UNK_SweetSpecter.
“SugarGh0st RAT is a remote access Trojan that is a custom variant of Gh0st RAT, an older commodity Trojan commonly used by Chinese threat actors,” the company said. “SugarGh0st RAT has historically been used to target Users in Central and East Asia.”
The SugarGh0st RAT was first recorded by Cisco Talos late last year in connection with a campaign targeting Uzbekistan’s Ministry of Foreign Affairs and South Korean users since August 2023.
The attack chain involves sending an AI-themed phishing message containing a ZIP archive, which is then packaged with a Windows shortcut file to deploy a JavaScript dropper responsible for launching the SugarGh0st payload.

“The May 2024 campaign appears to have targeted fewer than 10 individuals, all of whom appear to have direct ties to a leading U.S. artificial intelligence organization, based on open source research,” the company said.
The ultimate goal of these attacks is unclear, but it could theoretically be an attempt to steal non-public information about generative artificial intelligence (GenAI).
What’s more, the attacks against U.S. entities coincide with news reports that the U.S. government is seeking to restrict China’s use of GenAI tools from companies like OpenAI, Google DeepMind, and Anthropic, providing a potential motive.
Earlier this year, the U.S. Department of Justice (DoJ) also indicted a former Google software engineer, accusing him of stealing the company’s proprietary information and trying to use it for two artificial intelligence-related technology companies in China, including one where he A company founded around May 2023.
“If Chinese entities are restricted from accessing technology that supports the development of artificial intelligence, China-aligned cyber actors may target those with access to this information to further China’s development goals,” the company said.