A previously undocumented China-aligned threat actor has been linked to a series of adversary-in-the-middle (AitM) attacks that hijacked update requests from legitimate software to deliver a sophisticated implant known as NSPX30.
Slovak cyber security company ESET is tracking a group called Advanced Persistent Threat (APT) black wood. It is said to have been active since at least 2018.
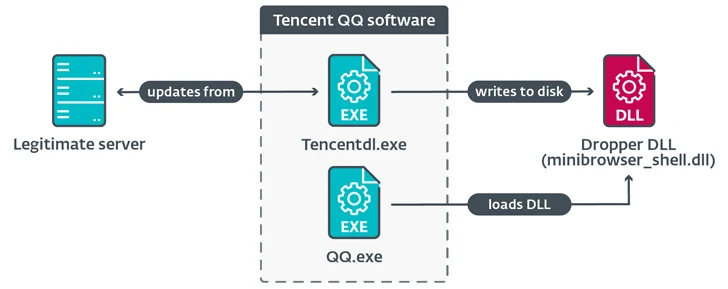
It has been observed that the NSPX30 implant is deployed through the update mechanism of known software such as Tencent QQ, WPS Office, and Sogou Pinyin, and targets manufacturing, trading, and engineering companies in China and Japan, as well as individuals located in China, Japan, and Japan.and the UK
“NSPX30 is a multi-layered implant that includes multiple components such as implants, installers, loaders, orchestrators and backdoors,” said security researcher Facundo Muñoz. “The latter two have their own set of plugins. “
“The implant is designed around the attacker’s ability to perform packet interception, allowing NSPX30 operators to hide their infrastructure.”
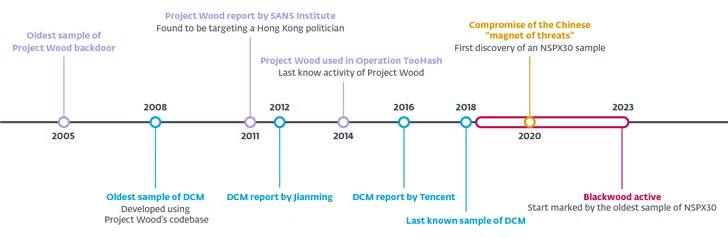
The backdoor is also capable of bypassing multiple Chinese anti-malware solutions by placing itself on an approved list, and its origins can be traced to January 2005 with another piece of malware, codenamed Project Wood, which was designed to collect System and network information, logging keystrokes and taking screenshots from the victim’s system.

Project Wood’s code base was the basis for several implants, including variants such as the 2008 DCM (also known as Dark Specter) malware, which was subsequently used in 2012 and 2014 to target Hong Kong and Greater China. Attacks by interested individuals.
NSPX30 is the latest version of the implant and is released when systems are compromised due to attempts to download software updates from legitimate servers using the (unencrypted) HTTP protocol, paving the way for the deployment of the implant DLL file.
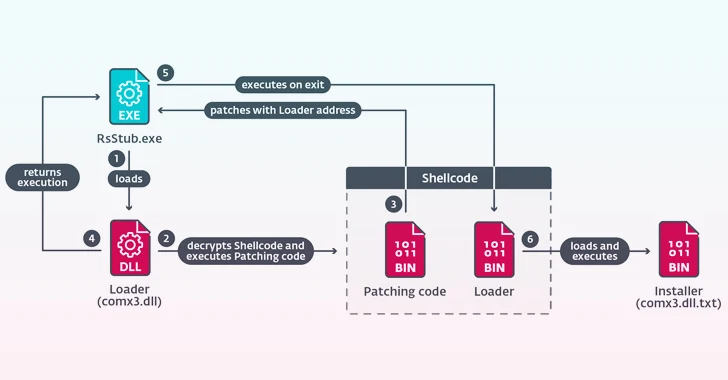
The malicious implant deployed as part of the infected update process creates multiple files on the disk and executes “RsStub.exe” (a binary file related to Rising Antivirus) in order to use it to launch “comx3.dll” are susceptible to DLL sideloading.
“comx3.dll” acts as a loader to execute a third file named “comx3.dll.txt”, which is an installation library responsible for initiating the next stage of the attack chain, ultimately leading to the orchestrator component (” WIN .dll”) execution. cfg”).
It’s unclear how threat actors deliver implants in the form of malicious updates, but Chinese threat actors such as BlackTech, Evasive Panda, and Mustang Panda have used infected routers as conduits to spread malware in the past.
ESET speculates that the attackers are “deploying network implants within the victim’s network, possibly on vulnerable network devices such as routers or gateways.”
“The fact that we found no evidence of traffic redirection via DNS may indicate that when the hypothetical network implant intercepts unencrypted HTTP traffic related to updates, it does so in the form of a DLL, executable, or ZIP Form Reply The implanter for the NSPX30 implant contains an archive of DLLs.”

The coordinator then proceeds to create two threads, one to obtain the backdoor (“msfmtkl.dat”) and another to load its plugin and add exclusions to whitelist the loader DLL to bypass China’s anti- Malware solutions.
The backdoor is downloaded to the Baidu website www.baidu through HTTP requests.[.]com, a legitimate Chinese search engine, has an unusual user-agent string that disguises the request as originating from the Internet Explorer browser on Windows 98.
The response from the server is then saved to a file, from which the backdoor component is extracted and loaded into memory.

As part of the initialization phase, NSPX30 also creates a passive UDP listening socket for receiving commands from the controller and exfiltrating data by potentially intercepting DNS query packets in order to anonymize its command and control (C2) basis facility.
These commands allow the backdoor to create a reverse shell, collect file information, terminate specific processes, capture screenshots, log keystrokes, and even uninstall itself from the infected computer.
A few weeks ago, SecurityScorecard revealed new infrastructure connected to another Beijing-based cyber espionage group, Volt Typhoon (aka Bronze Silhouette), which exploited a known security flaw (CVE) created by exploiting end-of-life Cisco RV320/325 routers. Botnet. -2019-1652 and CVE-2019-1653) operates in Europe, North America, and Asia Pacific.
“Approximately 30% of these (325 out of 1,116 devices) communicated with two IP addresses previously named proxy routers for command and control (C2) communications, namely 174.138.56[.]21 and 159.203.113[.]25th, within thirty days,” the company said.
“Volt Typhoon may have exploited these compromised devices to transmit stolen data or connect to the target organization’s network.”