
Media organizations and leading experts on North Korea have been on the receiving end of new campaigns orchestrated by threat actors Scarcruft December 2023.
“ScarCruft has been experimenting with new infection chains, including using technical threat research reports as bait, potentially targeting cybersecurity professionals and other threat intelligence sources,” SentinelOne researchers Aleksandar Milenkoski and Tom Hegel said in a report shared with The Hacker News. consumers.”
The North Korea-linked adversary, also known as APT37, InkySquid, RedEyes, Ricochet Chollima, and Ruby Sleet, is assessed as part of the Ministry of State Security (MSS), distinct from Lazarus Group and Kimsuky, which are members of the Ministry of State Security (MSS). MSS ) part. Is a unit within the Reconnaissance General Bureau (RGB).

The group is known for targeting governments and defectors, using spear phishing lures to deliver RokRAT and other backdoors, with the ultimate goal of covertly gathering intelligence to advance North Korea’s strategic interests.
In August 2023, ScarCruft was linked to an attack on the Russian missile engineering company NPO Mashinostroyeniya in conjunction with the Lazarus Group, which was considered a “highly desirable strategic espionage mission” to benefit its controversial missile program.
Earlier this week, North Korean state media reported that the country had tested its “underwater nuclear weapons system” in response to drills by the United States, South Korea and Japan, which it said posed a threat to its national security.
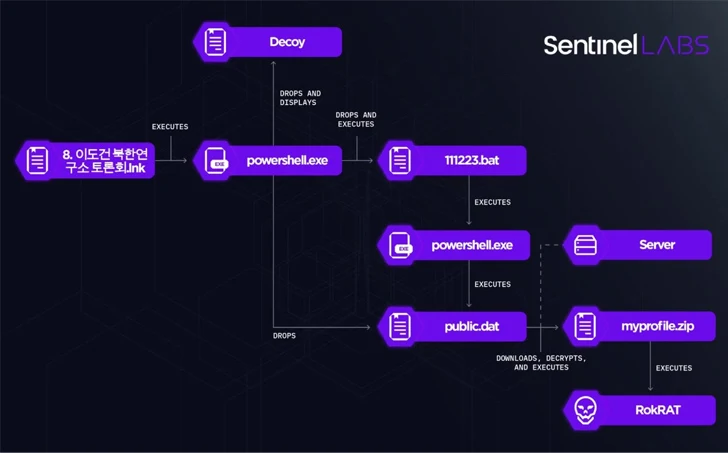
The latest attack chain observed by SentinelOne targets experts on North Korea affairs, posing as members of the North Korea Institute, urging recipients to open a ZIP archive containing presentation materials.
While seven of the nine files in the archive are benign, two of them are malicious Windows Shortcut (LNK) files, reflecting a multi-stage infection used to distribute the RokRAT backdoor previously disclosed by Check Point in May 2023 sequence.
There is evidence that some of the individuals targeted around December 13, 2023, had also been previously singled out a month earlier, on November 16, 2023.
SentinelOne said its investigation also uncovered malware – two LNK files (“inteligence.lnk” and “news.lnk”) and a shellcode variant delivering RokRAT – that it said was part of the threat actor’s planning and testing process. part.

While the previous shortcut file simply opened the legitimate Notepad application, shellcode executed via news.lnk paves the way for the deployment of RokRAT, although this infection process has not yet been observed in the wild, suggesting it may be used future events.
This development suggests that nation-state hacking groups are actively adapting their methods, possibly to avoid detection of public disclosures of their tactics and techniques.
“ScarCruft remains committed to obtaining strategic intelligence and may intend to gain insights into non-public cyber threat intelligence and defense strategies,” the researchers said.
“This allows adversaries to better understand how developments in North Korea are viewed by the international community and thereby contribute to North Korea’s decision-making process.”
