The FBI and the Cybersecurity and Infrastructure Security Agency warned in a joint advisory that threat actors are deploying botnets utilizing the Androxgh0st malware. The malware is capable of collecting cloud credentials (such as those from AWS or Microsoft Azure), abusing the Simple Mail Transfer Protocol, and scanning Amazon Simple Email Service parameters.
What is Androxgh0st malware?
The Androxgh0st malware was exposed in December 2022 by cloud security company Lacework. The malware is written in Python and is used to steal Laravel.env files, which contain secrets such as credentials for high-profile applications. For example, organizations can integrate applications and platforms such as AWS, Microsoft Office 365, SendGrid, or Twilio into the Laravel framework and store all application secrets in .env files.
The botnet uses the Laravel web application framework to find websites before determining whether the domain’s root-level .env file is exposed and contains data used to access other services. The data in the .env file may be usernames, passwords, tokens, or other credentials.
Cybersecurity company Fortinet released telemetry data from Androxgh0st, showing that more than 40,000 devices were infected by the botnet (Figure A).
Figure A
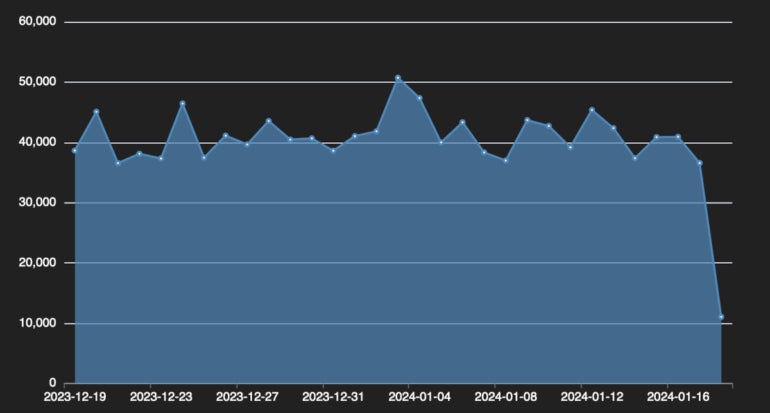
“Androxgh0st malware also supports a number of capabilities that enable Simple Mail Transfer Protocol (SMTP) abuse, such as scanning and exploiting exposed credentials and application programming interfaces (APIs) and web shell deployment,” the FBI/CISA advisory states.
How does Androxgh0st malware exploit old vulnerabilities?
Additionally, Androxgh0st has access to the Laravel application key; if the key is public and accessible, the attacker will attempt to use it to encrypt PHP code passed to the website as the value of the XSRF-TOKEN variable. This is an attempt to exploit the CVE-2018-15133 vulnerability in some versions of the Laravel web application framework. A successful attempt could allow the attacker to remotely upload files to the website. Based on this evidence of active exploitation, CISA added CVE-2018-15133 Laravel Untrusted Data Deserialization Vulnerability to its catalog of known exploited vulnerabilities.
Threat actors deploying Androxgh0st were also found to be exploiting CVE-2017-9841, a vulnerability in the PHP testing framework PHPUnit that allows attackers to execute remote code on a website.
CVE-2021-41773 was also exploited by threat actors. This vulnerability in Apache HTTP Server could allow an attacker to execute remote code on the website.
What do we know about the spam purposes of the Androxgh0st malware?
Lacework wrote in late 2022 that “nearly one-third of the critical incidents observed by Lacework over the past year were believed to be for the purpose of spam or malicious email activity,” with the majority of the activity being driven by Androxgh0st initiated.
The malware has several SMTP-abusing capabilities, including scanning Amazon’s simple email service sending quotas, which may be used to send spam in the future.
How to protect against the Androxgh0st malware threat
A joint CISA and FBI advisory recommends the following actions:
- Keep all operating systems, software and firmware up to date. In particular, the Apache server must be up to date. As can be seen from this article, attackers are still able to trigger the Apache web server vulnerability patched in 2021.
- Verify that the default setting for all URIs is to deny access unless there is a specific need for access from the Internet.
- Make sure your Laravel application is not configured to run in debug or test mode, as this may make it easier for an attacker to exploit weaknesses.
- Remove all cloud credentials from the .env file and revoke them. As CISA and the FBI put it, “All cloud providers have more secure ways to provide temporary, frequently rotated credentials to code running within web servers without storing them in any files.”
- Check for any platforms or services that use .env files for unauthorized access or use.
- Searches for unknown or unrecognized PHP files, especially in the root folder of the web server and in the /vendor/phpunit/phpunit/src/Util/PHP folder (if the web server is using PHPUnit).
- Check outgoing GET requests to file hosting platforms such as GitHub and Pastebin, especially when requesting access to .php files.
Additionally, it is recommended to check for newly created users of any affected services, as Androxgh0st has been observed to create new AWS instances for other scanning activities.
Security solutions must be deployed on all endpoints and servers of the organization to detect any suspicious activity. If possible, your IT department should deploy multi-factor authentication on all services to avoid compromise by attackers with valid credentials.
Reveal: I work for Trend Micro, but the opinions expressed in this article are mine.
