Prominent figures working on Middle East affairs at universities and research institutions in Belgium, France, Gaza, Israel, the UK and the US have been targeted by Iranian cyber espionage groups Psychic Sandstorm From November 2023.
Microsoft’s threat intelligence team said in an analysis on Wednesday that the threat actors “used customized phishing lures in an attempt to socially engineer targets to download malicious files,” describing them as a “technically and operationally mature Mind Sandstorm subgroup. ”.
In some cases, these attacks involved the use of a previously undocumented backdoor called MediaPl, suggesting that Iranian threat actors are working to improve post-intrusion espionage techniques.
Mint Sandstorm, also known as APT35, Charming Kitten, TA453, and Yellow Garuda, is known for its skilled social engineering campaigns, even resorting to legitimate but compromised accounts to send customized phishing emails to potential targets. It is assessed to be affiliated with Iran’s Islamic Revolutionary Guard Corps (IRGC).

Raymond said the subcluster engages in resource-intensive social engineering to single out journalists, researchers, professors and other individuals with insights into security and policy issues of interest to Tehran.
The latest set of intrusions features the use of decoys related to the Israel-Hamas war, sending harmless emails under the guise of journalists and other high-profile individuals to establish rapport with targets and establish a level of trust before attempting Send malware to targets. Target.
Microsoft said the campaign was likely conducted by nation-state threat actors to gather opinions on war-related incidents.
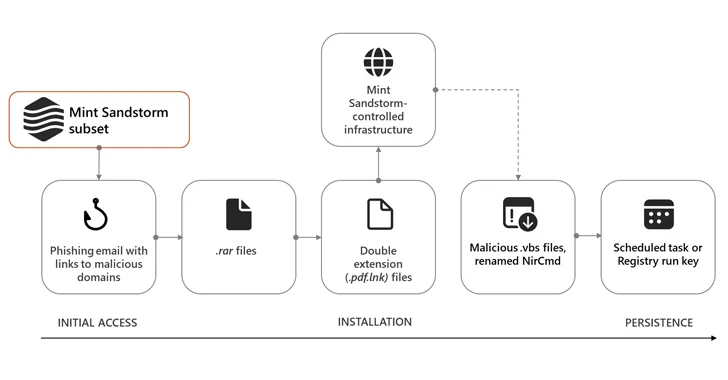
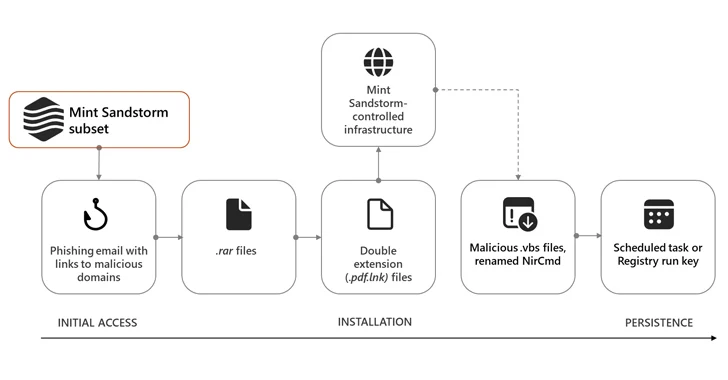
Using a compromised account to send emails belonging to the person they are trying to impersonate is an unprecedented new Sandstorm tactic that uses the curl command to connect to the command and control (C2) infrastructure.
If the target comes into contact with the threat actor, they receive a follow-up email containing a malicious link to a RAR archive file that, when opened, causes a Visual Basic script to be retrieved from the C2 server and retained on the target’s environment.
These attack chains further pave the way for custom implants such as MischiefTut or MediaPl, the former of which was first revealed by Microsoft in October 2023.
Implemented in PowerShell, MischiefTut is a basic backdoor that can run reconnaissance commands, write the output to a text file, and download other tools on the infected system. The first recorded use of this malware dates back to the end of 2022.
MediaPl, on the other hand, disguises itself as Windows Media Player and aims to transmit encrypted communications to its C2 server and initiate commands received from the server.

“Mint Sandstorm continues to improve and modify the tools used in targeted environments, and these activities may help the group persist in infected environments and better evade detection,” Microsoft said.
“The ability to gain and maintain remote access to target systems allowed Mint Sandstorm to conduct a range of activities that could adversely affect the confidentiality of the systems.”
Dutch newspaper De Volkskrant revealed earlier this month that Erik van Sabben, a Dutch engineer recruited by Israeli and US intelligence services, may have used water pumps to make the disclosure. deploy An early variant of the notorious Stuxnet malware was discovered in Iran’s nuclear facilities in 2007.