A remote access Trojan (RAT) named Remcos RAT was found to be spreading through network drives in South Korea disguised as adult-themed games.
WebHard is the abbreviation of network hard disk. It is a popular online file storage system in China, used for uploading, downloading and sharing files.
While network drives have been used to spread njRAT, UDP RAT, and DDoS botnet malware in the past, new analysis from the AhnLab Security Emergency Center (ASEC) shows that this technology has been used to spread Remcos RAT.

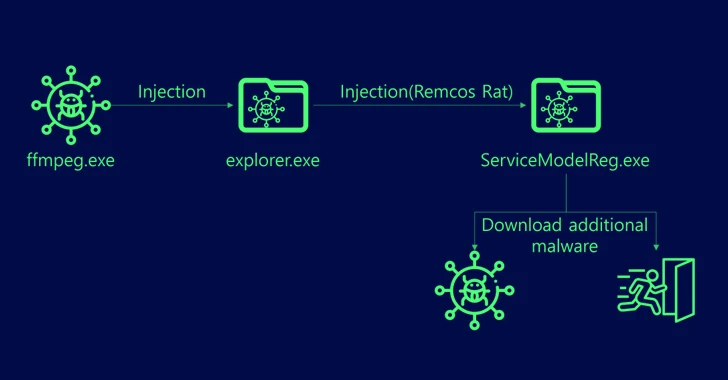
In these attacks, users are tricked into opening booby-trapped files pretending to be adult games. When launched, these files execute a malicious Visual Basic script to execute an intermediate binary file named “ffmpeg.exe.”
This results in the Remcos RAT being retrieved from a server controlled by the actor.

Remcos (also known as Remote Control and Monitoring) is a sophisticated RAT that facilitates unauthorized remote control and monitoring of infected hosts, allowing threat actors to steal sensitive data.
The malware was originally marketed by German company Breaking Security in 2016 as a true remote management tool, but has transformed into a powerful weapon used by adversaries to penetrate systems and establish unfettered control.

“Remcos RAT has evolved into a malicious tool used by threat actors in a variety of activities,” Cyfirma noted in an August 2023 analysis.
“This malware’s multifunctional capabilities, including keylogging, recording, screenshots, and more, highlight its potential to compromise user privacy, leak sensitive data, and manipulate systems. The RAT disables User Account Control (UAC) and creates persistent capabilities further amplify its potential impact.”