Threat actors can weaponize a new exploit technique called Simple Mail Transfer Protocol (SMTP) smuggling to send spoofed emails with fake sender addresses while bypassing security measures.
“Threat actors could abuse vulnerable SMTP servers around the world to send malicious emails from arbitrary email addresses to conduct targeted attacks,” said Timo Longin, senior security consultant at SEC Consult, in an analysis published last month. Phishing attack.”
SMTP is a TCP/IP protocol used to send and receive email over the Internet. In order to relay messages from an email client (also called a mail user agent), an SMTP connection needs to be established between the client and the server in order to transfer the actual content of the email.

The server then relies on what’s called a Mail Transfer Agent (MTA) to check the domain of the recipient’s email address, and if it’s different from the sender’s domain, it queries the Domain Name System (DNS) to find the MX ( Mail exchanger) records the recipient’s domain and completes the mail exchange.
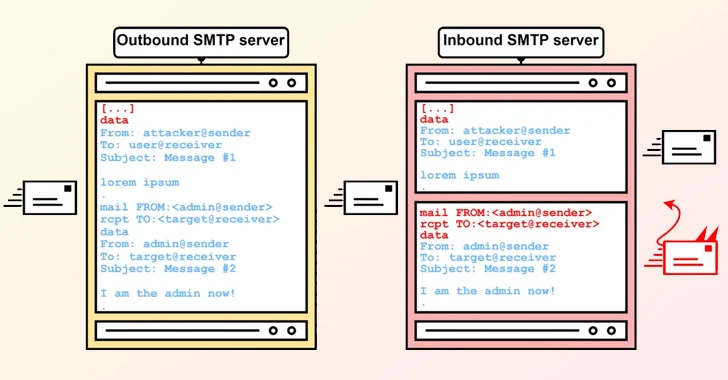
The crux of SMTP smuggling is an inconsistency in how outbound and inbound SMTP servers handle end-of-data sequences differently, which could allow threat actors to breach email data, “smuggle” arbitrary SMTP commands, or even send separate email emails .

It borrows concepts from a known attack method called HTTP request smuggling, which exploits differences in the interpretation and processing of “Content-Length” and “Transfer-Encoding” HTTP headers to add ambiguous requests to Inbound requests are chained.
Specifically, it exploited security vulnerabilities in Microsoft, GMX, and Cisco messaging servers to deliver emails that spoofed millions of domains. Postfix and Sendmail’s SMTP implementations are also affected.

This allows forged emails to be sent that appear to be from legitimate senders, with appropriate checks to ensure the authenticity of incoming messages, namely Domain Key Identified Mail (DKIM), domain-based email verification, reporting and Conformance (DMARC) ) and Sender Policy Framework (SPF).
While Microsoft and GMX have fixed the issues, Cisco said the findings do not constitute a “vulnerability, but a feature and they will not change the default settings.” Therefore, it is still possible to smuggle inbound SMTP to a Cisco Secure Email instance using the default settings.
As a solution, SEC Consult recommends that Cisco users change their settings from Clean to Allow to avoid receiving spoofed emails with valid DMARC checks.