
Threat actors related to this 8220 Gang Malware has been observed exploiting high-severity flaws in Oracle WebLogic Server to spread its malware.
The security flaw, CVE-2020-14883 (CVSS score: 7.2), is a remote code execution error that could be exploited by an authenticated attacker to take over a vulnerable server.
Imperva said: “This vulnerability allows an authenticated remote attacker to execute code using a small tool chain, and is commonly associated with CVE-2020-14882 (an authentication bypass vulnerability that also affects Oracle Weblogic Server) or using a leaked, stolen or weak Credentials are associated.” in a report released last week.

The 8220 gang has a history of exploiting known security vulnerabilities to spread cryptojacking malware. In early May this year, the group was discovered to have exploited another flaw in Oracle WebLogic servers (CVE-2017-3506, CVSS score: 7.4) to connect devices to a cryptocurrency mining botnet.
The latest attack chain documented by Imperva requires exploiting CVE-2020-14883 to specifically craft an XML file and ultimately run code responsible for deploying stealer and coin-mining malware such as Agent Tesla, rhajk, and nasqa.
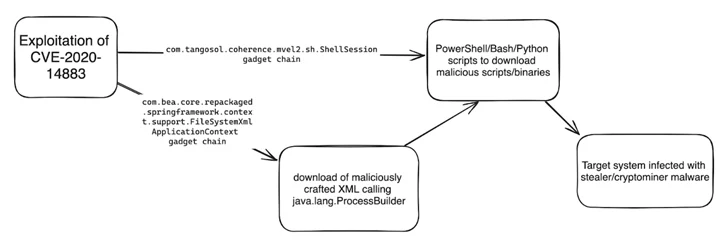
“The group appears to be opportunistic in selecting targets, with no clear country or industry trends,” said Daniel Johnston, a security researcher at Imperva.
Targets of the campaign include the healthcare, telecommunications and financial services industries in the United States, South Africa, Spain, Colombia and Mexico.
“The group relies on simple, publicly available vulnerabilities to attack well-known vulnerabilities and exploit simple targets to achieve their goals,” Johnston added. “While they are considered immature, they continue to evolve their tactics and techniques to Evade detection.”
