A malware botnet called Ebury It is estimated that 400,000 Linux servers have been compromised since 2009, with more than 100,000 servers still compromised as of the end of 2023.
The findings come from Slovak cybersecurity firm ESET, which describes it as one of the most advanced server-side malware campaigns for financial gain.
“Ebery actors have been pursuing monetization activities […]including the spread of spam, network traffic redirection and credential theft,” said security researcher Marc-Etienne M. Léveillé in an in-depth analysis.
“[The] Carriers also use AitM to conduct cryptocurrency heists and steal credit cards through network traffic eavesdropping, often called server-side cyber theft.
Ebury was first documented more than a decade ago as part of a campaign codenamed Operation Windigo, which targeted Linux servers to deploy malware, as well as other backdoors and scripts such as Cdorked and Calfbot for redirection respectively. Network traffic and spam.

Then, in August 2017, a Russian citizen named Maxim Senakh was sentenced to nearly four years in prison in the United States for his role in the development and maintenance of botnet malware.
“Senach and his co-conspirators used the Ebury botnet to generate and redirect Internet traffic to facilitate various click fraud and spam schemes that fraudulently generated millions of dollars in revenue,” the DOJ said at the time.

“As part of his guilty plea, Senach admitted that he supported a criminal enterprise by creating accounts with domain name registrars that helped develop the Ebury botnet infrastructure and personally profited from the traffic generated by the Ebury botnet.”
ESET’s investigation uncovered a variety of methods used by attackers to deliver Ebury, including stealing SSH credentials, credential stuffing, penetrating hosting provider infrastructure, exploiting flaws in control web panels (such as CVE-2021-45467), and SSH adversaries. Method-in-the-Middle (AitM) attack.
Threat actors have also been observed using false or stolen identities to cover their tracks, not to mention using malware to compromise the infrastructure used by other criminals to achieve their goals and obfuscate attribution efforts.
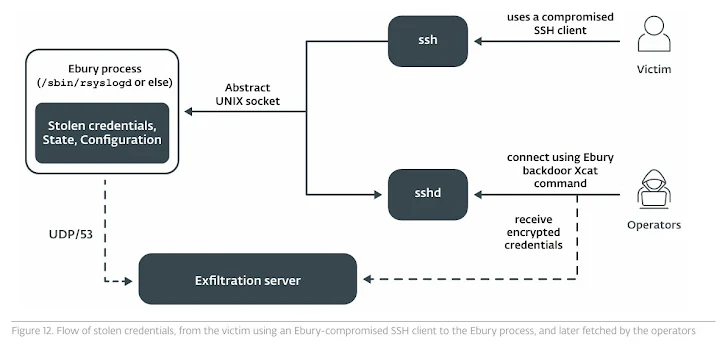
“One example is the compromise of servers responsible for collecting data from Vidar Stealer,” ESET said. “Ebury actors used stolen identities obtained through Vidar Stealer to rent server infrastructure and conduct activities that led law enforcement agencies to Wrong direction.”
In another example, Ebury is said to have been used to compromise the systems of the Mirai botnet authors and steal code before it was made public.
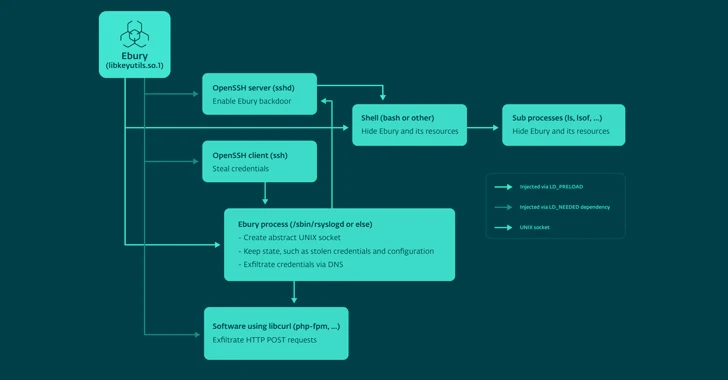
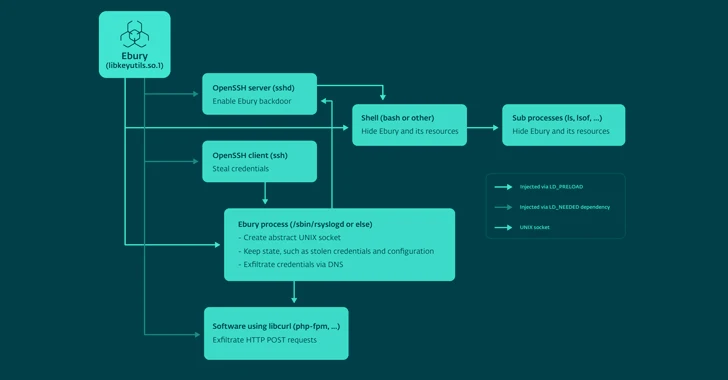
The malware acts as both a backdoor within the OpenSSH daemon and a credential stealer, allowing attackers to deploy additional payloads (such as HelimodSteal, HelimodRedirect, and HelimodProxy) and expand their presence on compromised networks. The latest version of Ebury known to date is 1.8.2.

The updated Ebury artifact introduces new obfuscation techniques, the Domain Generation Algorithm (DGA), and a technique to better hide its presence by acting as a userspace rootkit when injecting an SSH session shell.
“The common goal of these tools is to profit from the servers they compromise through various methods,” ESET said. “Server monetization methods range from credit card information theft and password theft to traffic redirection, spam sending and credential theft.”
HelimodSteal, HelimodRedirect, and HelimodProxy are Apache HTTP server modules used to intercept HTTP POST requests to web servers, redirect HTTP requests to ads, and proxy traffic for spam. Another new tool used is a core module called KernelRedirect, which implements Netfilter hooks to modify HTTP traffic to perform redirections.
Software that hides and allows malicious traffic to pass through firewalls, as well as Perl scripts that conduct large-scale AitM attacks within hosting providers’ data centers are also utilized to compromise valuable targets and steal cryptocurrency from wallets hosted on these servers. .
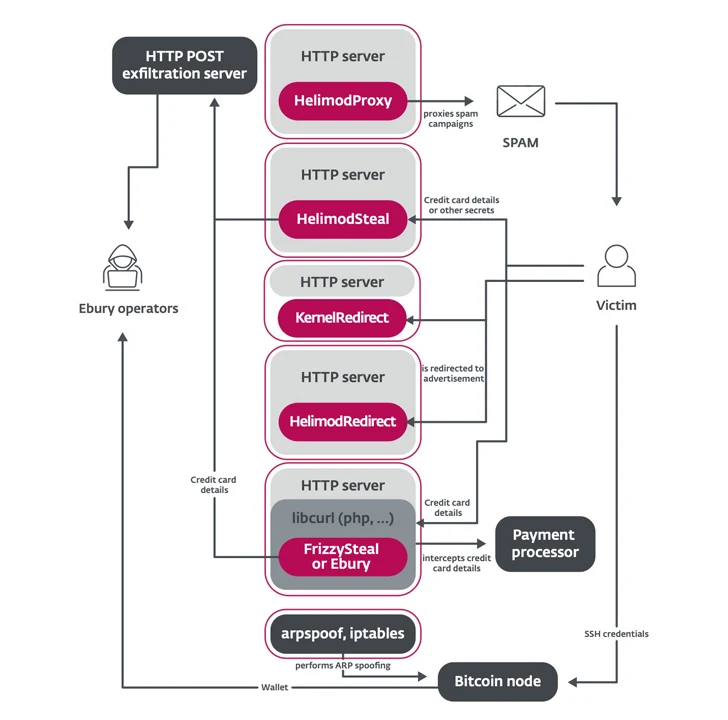
It is believed that as many as 200 servers in more than 75 networks in 34 different countries were targeted in this way between February 2022 and May 2023.
HelimodSteal is also designed to capture credit card data submitted by victims to online stores, effectively acting as a server-side web browser to extract information received by compromised servers.
In another chain of events, financial details can be obtained through Ebury or FrizzySteal, a malicious shared library injected into libcurl that leaks requests from the compromised server to external HTTP servers (such as payment processors) .
ESET notes: “End-to-end encryption (HTTPS) does not protect against this threat since both run within a web server or application.”
“Access to servers used for shared hosting gave them access to large amounts of unencrypted web traffic, which they exploited to covertly redirect or capture details submitted in online forms.”